AZ-900 Microsoft Azure fundamentals 5
Cloud Concepts 6
Language of Cloud Computing 6
Pricing 7
Cloud Service Model 7
Azure architecture 9
Regions 9
Availability zone 9
Callouts 9
Resource group 10
Callouts 10
Azure resource manager (ARM) 10
Callouts 10
Compute 10
Virtual machine 10
Objectives 10
Scale set 11
App service 11
Azure container instances 11
Azure Kubernetes services: manage containers 12
Windows virtual desktop 13
Serverless azure functions 13
Demo of app service 13
Networking 14
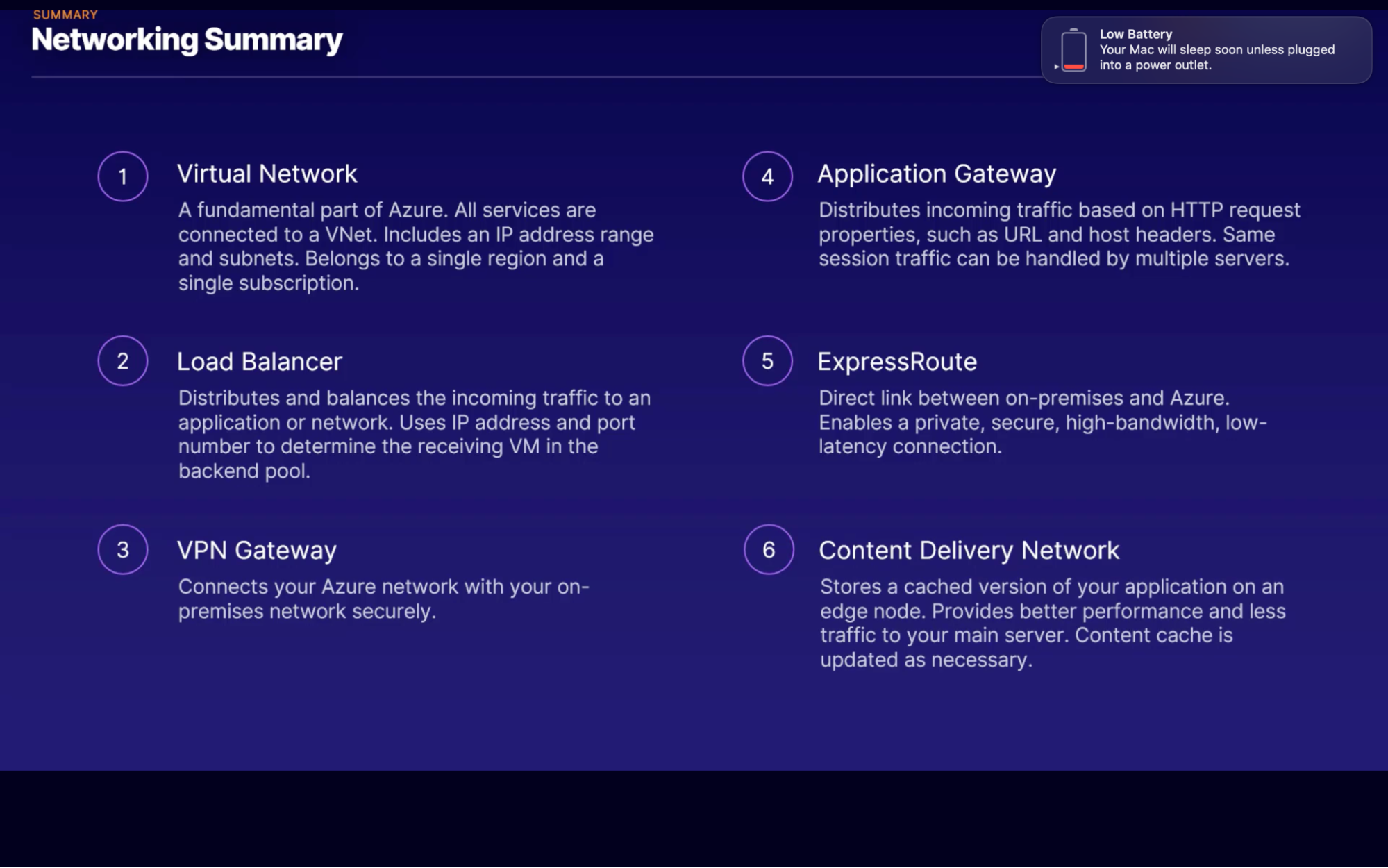
Virtual network 14
VNet 14
IP Address 14
4 category 14
Adreess space 14
Subnet 14
Regions & Subscription 15
Benefits 15
VNet Peering 15
Demo 15
Load balancer 16
VPN Gateway 16
Virtual network gateway(VNG) 16
VPN Gateway 16
When to use? 17
How it works? 17
Setup 17
Application gateway 18
Express route 19
Azure content delivery network 19
Summery 19
Storage 20
Blob 20
When: 20
Blob type: 20
Price tier: 20
Disk 20
Disk type: 20
File 21
Issues 21
Resolve 21
Scenarios 21
Archive 21
Database 22
Cosmos DB 22
Issue 22
Resolve 22
Features 22
Azure SQL 22
Usecase 22
Benefits 23
Azure SQL database vs. Azure SQL managed instance 23
MySQL 23
What 23
Benefits 24
Usecases 24
Postgre SQL 24
What 24
Features 24
Usecases 24
Database migration service 24
Authentication AND Authorization 25
Identity service 25
Azure Active Directory 25
Tenant 26
Subscription 26
Hybrid cloud architecture 26
Multi-factor authentication 26
SSO 26
Azure Solutions 27
Internet of Things 27
what 27
Example: 28
2 azure service for IOT 28
Big Data 29
Why BigData 29
How data collected 29
Azure BigData services 29
Outcomes 30
Machine Learning 30
Azure service 30
Serverless 30
Services 30
DevOps 30
Services 31
Security 32
Defense in depth 32
What 32
Why 32
Security leval 32
Securing network connectivity 32
Why 32
Azure services 32
Public and private endpoint 34
What for 34
Microsoft defender for cloud (formerly azure security center) 36
What 36
Highlights 37
How to use 37
Azure key vault 37
Azure information protection 37
Why 37
When 37
How to use 38
Azure sentinel 38
What 38
When 38
How 38
Features 38
Azure dedicated host 38
When 38
What 38
Benefits 38
Microsoft defender for identity (formerly Advance threat protection) 39
What 39
When 39
Privacy, Compliance And Trust 39
Governance 39
Tools & service 39
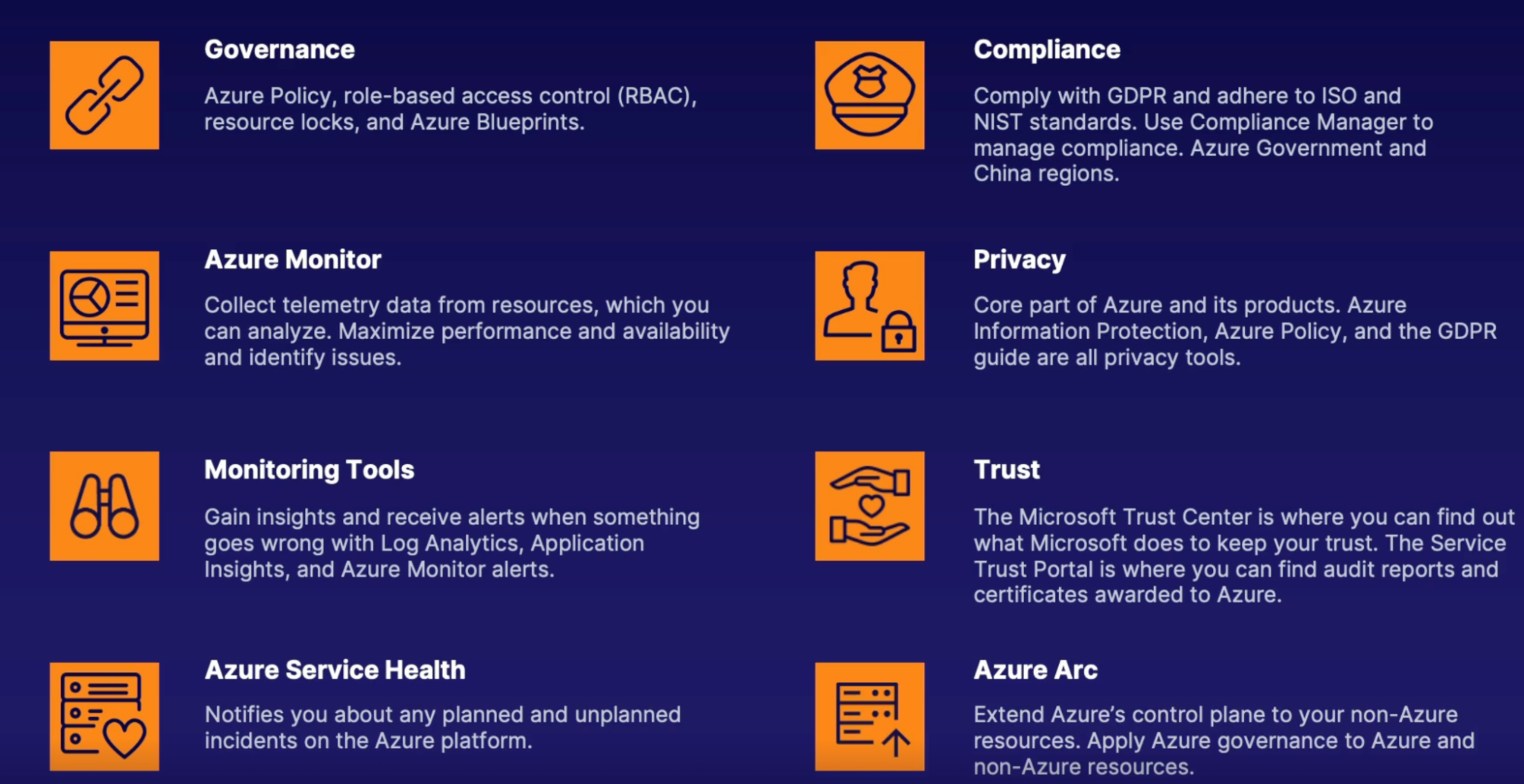
Azure monitor 41
Why 41
Monitoring tools 41
Log analytics 41
Application insight 41
Azure Alerts 42
Azure service health 42
What 42
Features 42
Scenarios 42
Compliance 42
What 42
When 43
Tool 43
Benefits 43
Why compliance 43
Privacy 44
Trust 44
Services 44
azure Arc 44
what 44
How 44
Benefits 45
Scenarios 45
Price 45
Subscriptions 46
Management groups 46
Cost management 46
Pricing factors 47
Factors 47
Billing zones 47
Azure pricing calculator 47
Total cost of ownership calculator 47
Best practices 47
Credits 48
AZ-900 Microsoft Azure fundamentals
Cloud Concepts
- Core benefits of using Azure such as high availability and scalability
Azure architecture
- How cloud platform is put together to work best for you
Compute
- Use Azure to run your application on a VM
Networking
- How each azure service is talk to each other and ret of the internet
Storage
- Where you put all your data
Database
- Store your data and retrieve it efficiently
Authentication and authorization
- Make sure only the right users get into your services
Solutions
- Complex scenarios azure provides
Security
- Make best security choices for your business functions
Privacy, compliance and trust
- How services ensure privacy for your users and how you stay compliant with regulations and standards
Prices
Support
Ways to create Azure resources in Azure CloudShell(web-based shell)
- Azure CLI: text only(stable/strutured) way to manage resources
- az group list
- az storage account list
- az vm list
- az vm create
- Powershell Commands: supported by azure with modules and cmdlet // for scripting
- Get-AzResourceGroup
- Get-AzStorageAccount
- Get-AzVm
- Get-AzResource | ft
- Remove-AzVm
Best way to create Azure resources
- ARM Template: to automate and replicate tasks, processes
- Idemopotent: applying operations multiple time and the resule is always the same // running the same template again and again to get the same result(variablize the name of the resource to use the template multiple time)
Cloud Concepts
Language of Cloud Computing
High availability:
Traditional | Cloud |
You own the hardware | You don’t own the hardware |
Physical hardware | Add more server with a click |
You can’t just add server | If hardware fails, replace instantly |
| Use clusters to ensure HA |
Fault tolerance:
- Resilience: Fault tolerance is part of the Resilience in CC
- Zero downtime: faults created by azure are also mitigated by azure
Disaster recovery:
- Catastrophic disasters: hurricane, flood, tornado, cyber attack
- Plan to recover: complete plan to recover critical business systems
- Specific points: designated time to recovery (how long does it take to recover) and recovery point(point of time data to recover)
Scalability:
- To scale up/down/out → use autoscaling for critical scenarios
Elasticity:
- Ability to quickly expand and decrease computing resources, not just VMs. elasticity enables scaling
Agility:
- Ability to rapidly develop, test and launch software applications that drive business growth

Pricing
- Capital expenditure(CapEx): is buying hardware outright, paid upfront as a one-time purchase.
- Operational expenditure(OpEx): ongoing cost needed to run your business
- Consumption-based pricing lets you pay only for what you use
Cloud Service Model
Infrastructure as a service
- Actual servers
- Scaling is fast
- No ownership of hardware
- Azure IaaS: ex: VMs & servers, networking, physical building
Platform as a service
- Superset of IaaS
- Middleware and tools
- PaaS support web application life cycle(building, testing, deploying, maintaining, updating)
- Avoid software license hell
Software as a service
- Apps running on IaaS and PaaS
- Providing a managed service
- You don’t own the software, but you pay an access fees to use it(ex: credit card payments, Gmail for emails, office 365)
Serverless
- a single function of code can be hosted, deployed, run and managed without having to maintain full applications

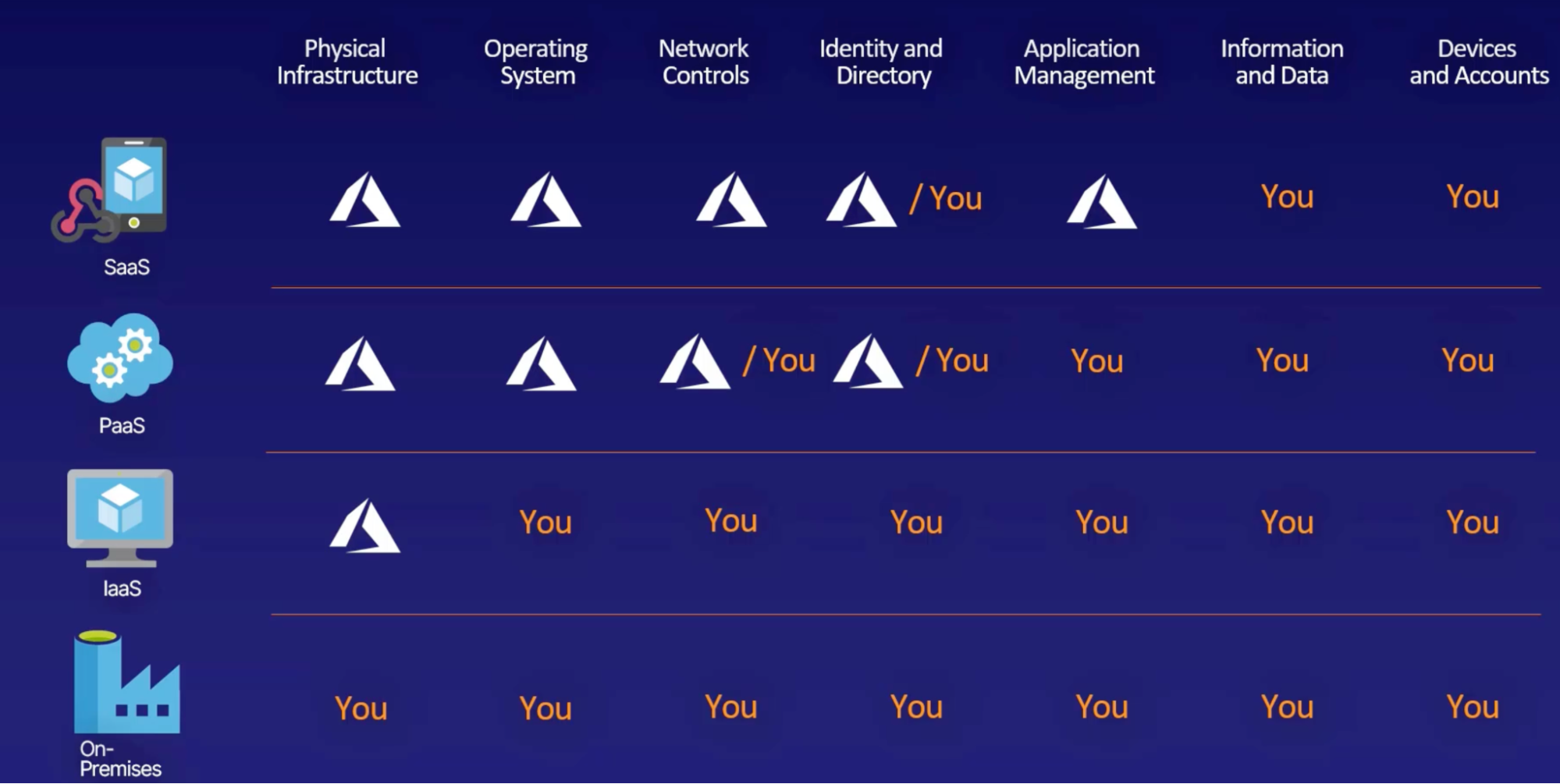
Azure architecture
Regions
Each region has more than 1 data center(physical location)
- How to select the region for your resources
- Where your user location is to minimize latency
- Some features are not in all regions
- Price is different from region to region
Availability zone
- Physical location within a region
- Independent: Each zone has its own power, cooling, and networking
- Zone: each region has a minimum of 3 zones. For data center failures
Callouts
- To protect your data/apps from failures by replicating them bw AZs
- For VMs you have to specify how many AZ do you need your VMs to be in
- Having your VMs in one AZ won’t protect your apps against outages
- You’ll need at least 2 AZ
- Automatically replicate across zones. when you add a bit to one zone, it will get replicated to another zone automatically
Resource group
- Everything(all resources) in azure must be in RG
- RG is like a container to hold your resources as per your azure solutions // CF stack
Callouts
- Can Move resources from one RG to another
- Resources from multiple regions can be in one RG
- RG needs/has a location or region as it stores metadata about the resources in it
Azure resource manager (ARM)
- All interaction with azure resources go through ARM. it’s the main architecture in azure to create, update and manipulate resources
- Deployment and management service for azure
Callouts
- Group resource handling
- Deploy resources in a consistent state
Compute
Virtual machine
- Virtual servers, can be multiple servers running on the same physical hardware // virtualization of hardware
- You manage/control everything(OS, app to install, app maintain) except hardware
- VMs are IaaS: you’re responsible for entire machine
- Prices goes up as you utilize more RAM, CPU and GPU(AI, ML), you pay by the hour
Objectives
- Deploy windows VM
- Basics
- Subscription
- RG
- Region
- AZ
- Image
- Size (cpu and memory)
- User name/password
- Public Inbound ports: allow selected ports
- Disk
- OS Disk Type
- Encryption: Azure or you handle encryption
- Networking
- Connect and login to the server
- Delete the server
Scale set
- Scale set let you create and manage a group of identical, load-balanced VMs
- How?: you provide a single baseline VM and you can create multiple VMs from that instantly
- Benefits: HA, app resiliency
- IaaS part of the Azure compute
- Price: no additional cost using scale set. You only oay for VMs, Storage, Networking you use
App service
- PaaS part of the azure compute
- App service is an easy way to host and manage your apps
- Fully managed platform: server, network, storage and other infrastructure managed and handled by Azure. You focus on your business value and logic
- 3 Categories
- Web Apps: website/online app hosted on azure’s managed platform
- Run on both windows and linux platforms
- Supported a lot of languages: .net, java, node.js, PHP, ruby, Python
- Support auto scaling and load balancing
- Can host your existing container images
- deploy and run containerized applications in Azure
- API apps: expose and connect your data backend
- API apps: no GUI, Front End,
- It’s a interfact to connect other apps to programmatically
- Ex: company sell their data to clients
Azure container instances
- Primary service for hosting/running your workloads in a container
- With ACI you can run the app inside the container without managing any VMs via CLI or portal
- Build your software → software development lifecycle
- When your app is ready to publish it → app gets warped up in a container image // Application placed in a container
- App then be deployed/published to ACI
Azure Kubernetes services: manage containers
- When you want to manage multiple containers
- PaaS part of the azure compute
- Automatic application deployment
- Automatic scaling
- Replicate container architecture
- Reuse your container architecture by managing it in kubernetes
- Standard Azure service included
- You don’t have to worry about infrastructure in hardware. get identity and access management elastic provisioning and much more
- use Kubernetes with supported Azure regions and on-premises installation using Azure stack
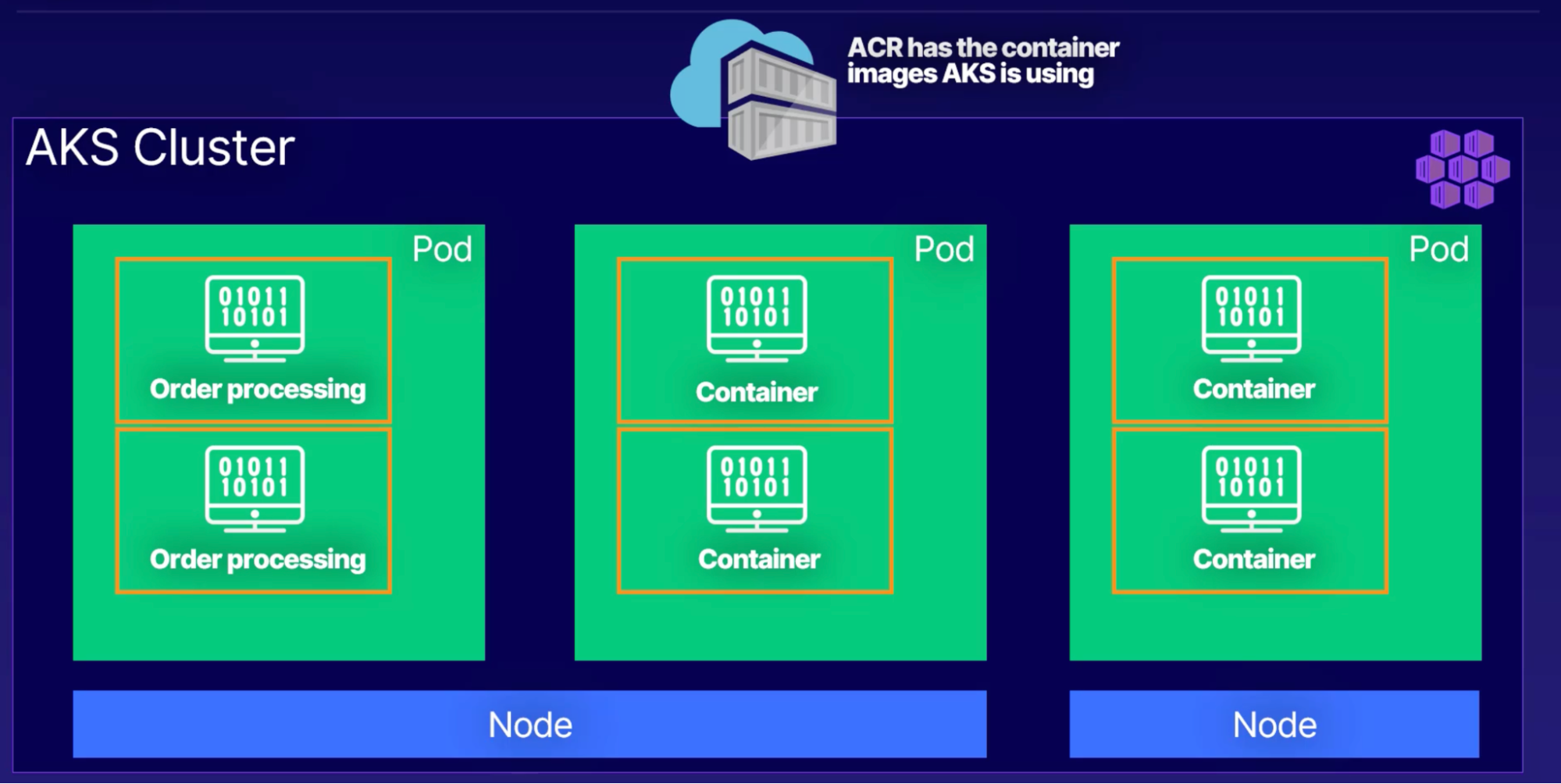
- How? → ACR - Azure container registry
- ACR keep track of current valid container images
- ACR manages files and artifacts for containers
- Feeds container images to ACI & AKS
- Use azure identity and security feature
- An application that processes orders from customers, This app runs inside a container, which is created from an image in ACR,
- AKS manages the containers and has a cluster (cluster is a set of machines called nodes that run containerized applications manage by Kubernetes)
- Pod is a Group of one or more containers with shared storage network and a specification for how to run the containers
- your app for processing orders lives in a pod
- When the number of orders increases and the current pod or pods can’t keep up Kubernetes can automatically provision another pod to take some of the load
Container Architecture
ACR has Image → create container to run app → running app
Kubernetes Architecture
Container/s → pod/s → node/s → cluster
Windows virtual desktop
- Runs on Azure
- PaaS part of the azure compute
- When to use?
- When you have employee work remotely and need to provide a windows environment for them
- Use any VM to host windows 10 instance
- Once deployed you can access from any device
Serverless azure functions
- SaaS part of the azure compute
- Benefits
- No maintenance
- No processes
- No VM
- Just focus on your functionality
- When you have traffic/data to process then only your function gets executed/runs/costs
- No traffic → no cost
- Example of serverless platform
Demo of app service
- Create App Service instance → web app
- Subscription
- RG
- App Name: must be unique to access it via internet
- Publish: Code or Docker Container
- Runtime stack: .net/java/python
- OS: windows/linux
- Region
- App Service Plan: more like a server/VM
- What you’ll get
- URL to access your website
Networking
Virtual network
VNet
- Fundamental part of azure infrastructure
- Allows VMs to securely communicate with each other, internet and on-premises network
- It’s virtual hardware: you don’t own/maintain hardware
IP Address
- Every server(hosting a website) has a IP address to ensure the traffic gets to the right server on the internet
4 category
Adreess space
- Is the range of IP addresses that are available. Ex: 192.168.0.1 - 192.168.0.252
- Every resources(VMs) that connected to VNet gets individual IP address from this range
- This is how services under the same VNet can communicate with each other
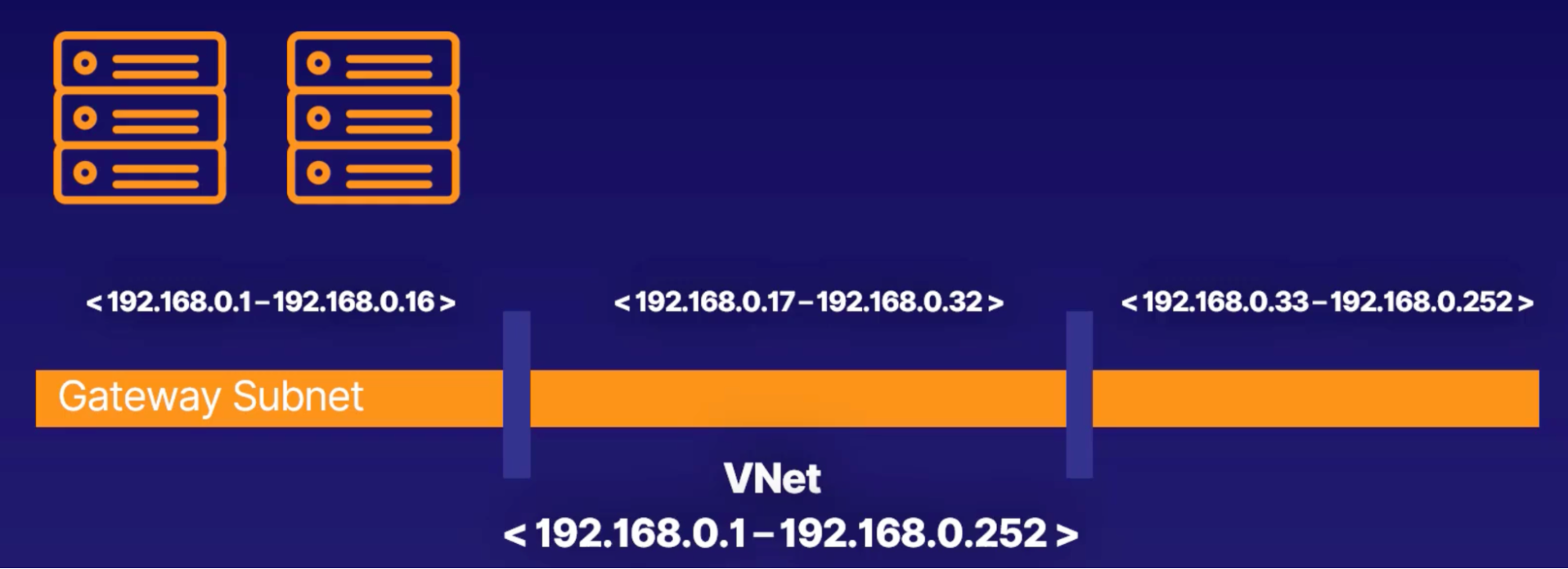
Subnet
- Enabled you to segment the Virtual Network into one or more subnetworks and allocate a portion of VNet’s address space to each subnet
- Example of dividing address space 192.168.0.1 - 192.168.0.252 into 3 subnet
- 192.168.0.1 - 192.168.0.16
- 192.168.0.17 - 192.168.0.32
- 192.168.0.33 - 192.168.0.252
- Resource grouping: group resources onto the same subnet to make it easier to keep an overview
- Address allocation: more efficient to allocate addresses to resources into smaller subnets
- Subnet security: use network security groups to secure individual subnets
Regions & Subscription
- A VNet belongs to a singal region. Every resources on the VNet must be on the same region as the VNet too
- A VNet belongs to just one subscription. But the subscription can have multiple VNet
Benefits
- Scaling: adding more VNets or more addresses to one is simple
- High availability: peering VNets, using a load balancer or using a VPN gateway all increases availability
- Isolation: manage and organize resources with subnets and network security group
VNet Peering
What
- Lets you connect 2 or more VNet in Azure over a private network // no public internet
How?:
- Traffic between VMs in a peered network it uses the private microsofts backbone network and never pass through public internet. Just like if the VMs are on same VNet
Benefits:
- Low-latency, high bandwidth
- Link separate network
- Data transfer
Demo
- Create a VNet with 2 subnet
- Create network security group:
- So that inbound and outbound rules on the NSG will take effect on your subnets and it will act as a firewall
- Associate NSG to subnets
You will need
- IPv4 address space. Ex: 10.0.0.0/24 // meaning how many IP addresses you want within your VNet
- Add howmany subnets you want
- Create NSG(to set up stateful firewall for the subnets)
- Attach subnets to youre NSG
Load balancer
- When to use LB
- Which problem does it solve
LB: When you have more than one VM serving your app; how do you decide which VM gets a particular user?
How: load balancer receives your internet and network traffic and, based on an IP address and a port, it will send that data to one of the VMs in the backend pool.
- Inbound traffic flows: any traffic whether from Internet or local VNet received by LB
- LB’s frontend is a gatekeeper of all traffic to VMs it manages
- Backend pool: the VM instances receives traffic
- Rules & Health prob: check to ensure backend instance can receive the data
VPN Gateway
When
- you want to securely communicate between your azure resources and on-premises network via internet
Virtual network gateway(VNG)
- VNG is composed of 2 or more VM that are deployed to specific subnet which is called gateway subnet
- VMs that are located in the gateway subnet are created when you create the VNG
VPN Gateway
Why to use?
- VPN gateway is a specific type of VNG that is used to send encrypted traffic between an Azure Virtual Network(VNet) and an on-premises location over the public internet
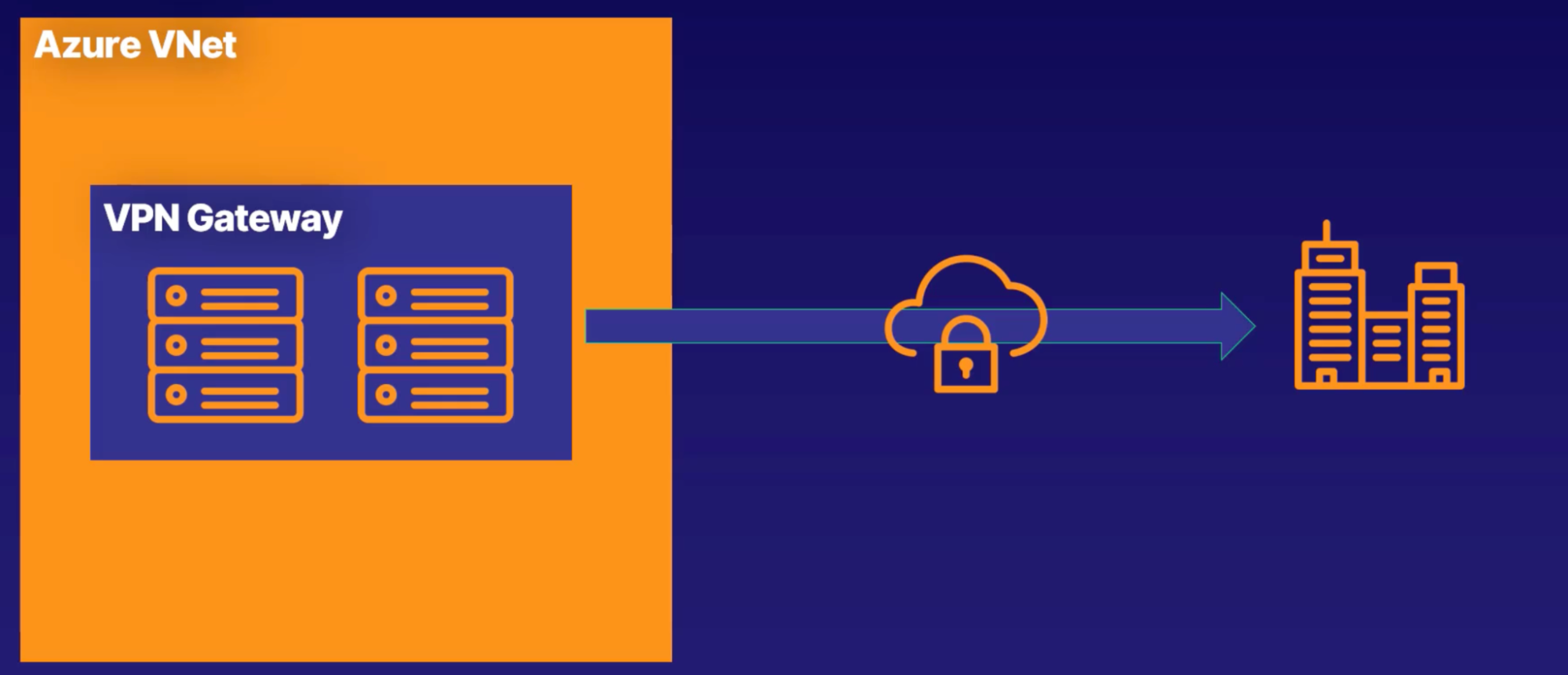
When to use?
- A company wants to move part of their system to cloud (to take an advantage of cloud goodness like HA, scalability and cost reduction)
- Hybrid solution with some of the data on on-premises and some on cloud
How it works?
- In order to communicate securly between the two, you create VPN Gateway which is a specific kind of VNet gateway
- Connect your on-premises server to VPN gateway
Setup
- An azure VNet with VPN gateway attached: this gateway will have it’s own public IP Address
- Tunel: a secure connection to tramit data, which has number of encryption mechanism
- On-premises network with a complimentary gateway that can accept the encrypted data
- Site to site connection vs multi-site connection (1 VPN Gatway connected to multiple on-premises gateway )

Questions answered
- When should you use
Application gateway
- How does it diffrent then LB
- Which application can use one
When: you want to route the traffic based on other parameters(HTTP request) than simply IP address and port number?
- With Application Gateway, you can make routing decisions based on additional attributes of an HTTP request, such as URI path or host headers.
HTTP request = An HTTP request is the data format that is received from any kind of internet traffic.
URI path = the web address for the request
Host headers = is a piece of information that is sent with the request.
HOW:
- this means you can send traffic from a specific web address to a specific machine.
- It works on the HTTP request of the traffic instead of the IP address and port.
Example: if you have a request for a URL that is images, you could send that to a specific pool of machines that are better at handling images. The same can be done for videos.
Benefits:
- Scaling
- Encryption
- Zone redundancy
- Multi-site hosting
Express route
- If you need Private link
WHEN
- you require a super-fast connection, right into the bowels of Azure, that is completely private
- if a company need their data to be both on-premises on Azure, it has to be highly available, and it needs to be periodically migrated, then ExpressRoute is the must-have connection from the company to Azure.
- ExpressRoutes don't go over the public internet // better security
Azure content delivery network
It's a distributed network of servers that can deliver web content close to users. CDNs store cached content on what is called edge servers in locations that are close to end users to minimize latency.
Summery
Storage
Storage account = unique azure namesapce (every object in azure has it’s own web address)
Blob
- Binary large object (made of bits and bytes)
- Data are stored in container inside a storage account
- Level: storage account → container → blob
- Storing: images, all types of file, steaming(audio, video), log files(archiving, backup, restore and disaster recovery)
When:
- long term backup, disaster recovery, and archiving
Blob type:
- Blocks: store text and binary data up to 4.7 TB. made up of individually managed blocks of data
- Append: optimal for append operation. Works well for logging where data is constantly appended
- Page: store random files up to 8 TB. ex: virtual hard drive and serve as a disk on a VM
Price tier:
- Hot: frequently accessed files, lower access times, higher access cost
- Cool: lower storage cost and higher access time. Data remains here at least 30 days
- Archive: lowest cost and higher access time
Disk
Disk storage: disk that you can store data on
Managed disk is attached to VM
- Azure manages: Azure manages physical disk and guarantees its uptime and backup.
- Size and performance: all part of your agreement with Microsoft
- Upgrade: disk size and type
Disk type:
- important when it comes to performance
- choose for your VM
- HDD:
- old school spinning hard drive
- Low cost and suitable for backups
- Data less frequently accessed
- Standard SSD
- The standard for production
- VM with SSD provides lower latency than an HDD, improved reliability, and better scalability.
- Premium SSD
- Super fast and high-performance
- Very low latency
- Use for critical workload
- Ultra disk
- For most demanding, data-intensive workloads
- Disk up to 64TB
File
Issues
- Most companies will have file shares that store all of the company's assets. Having on-premises can have some issues, though
- Constrain: You only have a limited amount of storage
- Backups: Backups need to be configured and maintained.
- Security: Data security can be hard to maintain and requires specialists to enforce.
- File sharing: require more infrastructure to both supply and manage
Resolve
- Sharing
- Managed
- Resilient: network and power outages won’t affect your storage
Scenarios
Hybrid: can have cloud file storage when on-premises space running out of space
Lift and shift: to move all your infrastructure to Azure.
Archive
Lowest price
Features: durable, encrypted and stable. Suitable for data less frequently accessed
Blob: archive storage is blob storage. So the same tool will work for both when retrieving the data
Database
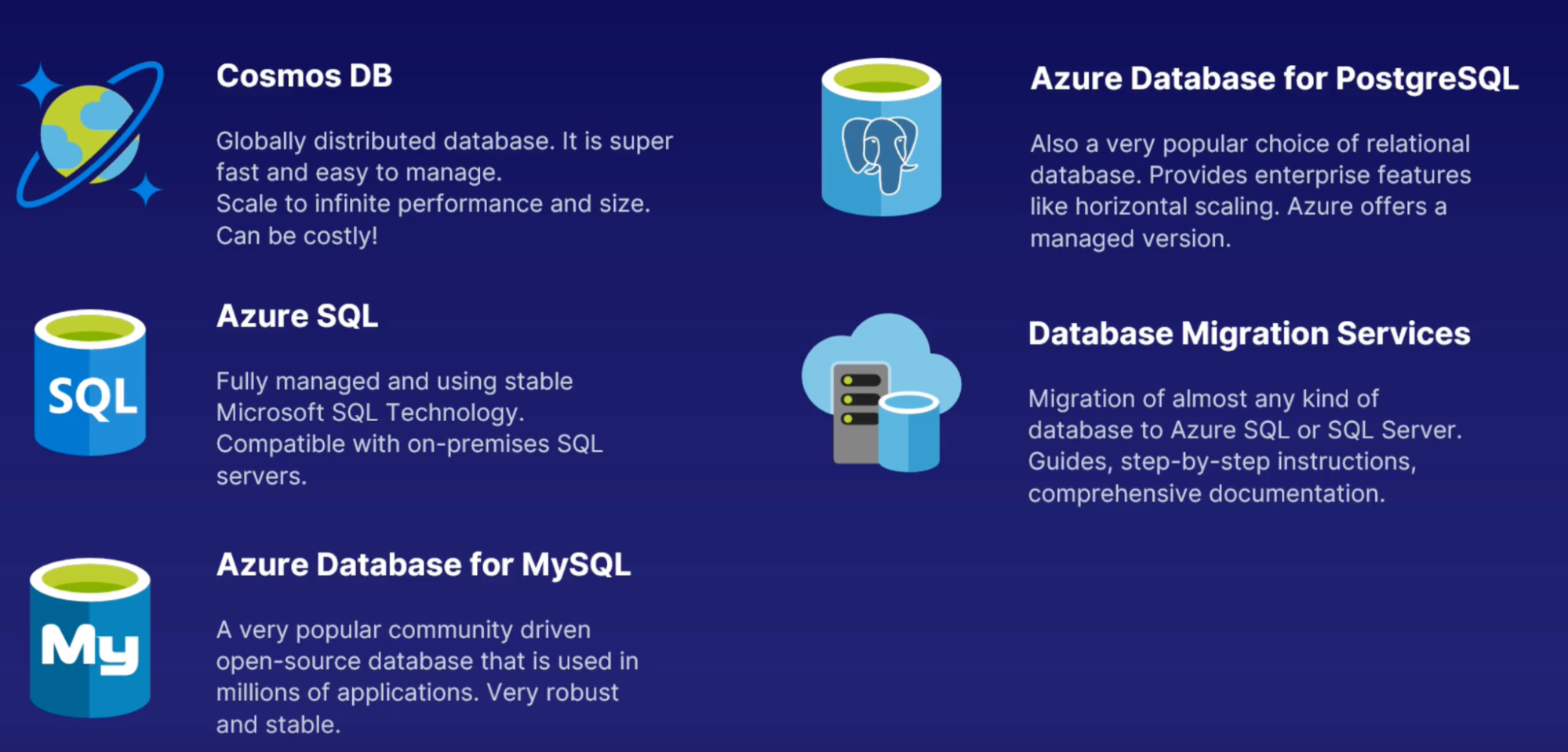
Cosmos DB
is a Globally scaled and fully managed database service. Fast read-writes
Issue
having data near your users is a key in providing the best experience for your users.
Old databases were difficult to set up across multiple locations and keep in sync.
Resolve
With Cosmos DB, the entire headache of the global distribution of your data is taken care of by Azure.
For example, if you have the data in the region of US East, West Europe, and South Africa and want to expand to Australia, all you have to do is click on that region in the Azure portal to enable it.
Features
Global from the start
- Synchronization
- Easy with cosmos: solve the issue of traditional database setup
- One-click to add region: easy to expand region and have the data in sync
- Continued Synchronization: stays on top of all read and writes to your data and make sure your data is moved between regions to stay in sync.
- Latency: is the time it takes for data to travel
- single-digit millisecond latency
- Scalability: scale Cosmos DB to infinity and beyond.
- Automated: when demand goes up, set Cosmos to scale with demand for each region and instance automatically.
- Infinite resources: any number of users to your application can be supported
- Low price: pay for what you use
- Connectivity
- Developer: SDK and API to connect
- Languages: C#, java
- Platform: data platform to integrate with, SQL, MongoDB
- Expensive
Azure SQL
Azure SQL is a fully-fledged database solution, where Azure manages all the parts (Azure will take care of your hardware and infrastructural level needs. Which include servers, storage, network, and everything else infrastructure-related) with managing the data in the database.
Usecase
- migrate your on-premises SQL server instances directly to Azure, and get all the benefits of managed instances
- No changes required on you on-premises database → migration is frictionless
- Cost saving
- The lower total cost of ownership- TCO
- Built-in machine learning
- Optimization: database performance and optimization suggestions are provided based on your usage, patents, and other metrics.
- Warnings: when bad things happening to your database → give warnings
Benefits
- Scalability
- Space: manage huge databases up to 100 TB
- Security
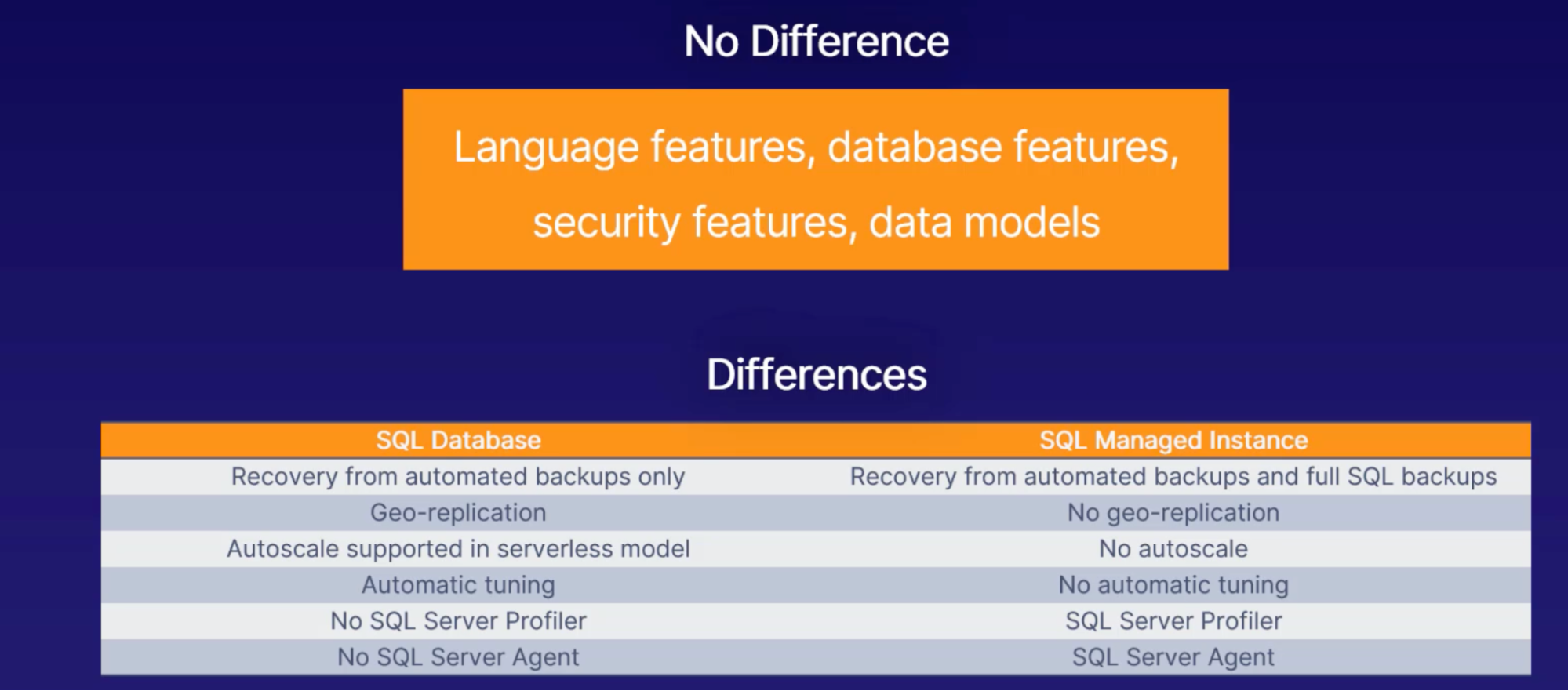
Azure SQL database vs. Azure SQL managed instance
Azure SQL: most like traditional SQL server
Azure SQL managed instance: aimed at migrating from on-prem
MySQL
What
Azure SQL is Microsoft product
MySQL is built and maintained by the community
- Relational database
- Mature and stable
Benefits
- PaaS: infra is managed by Microsoft
- Dev focus
- Choice of language
- HA
- Azure security feature: advance threat protection, monitoring, identity management
- Cloud PaaS capability: automatic backup, monitoring, patching
Usecases
- Web apps
- E-commerce
- Mobile apps
- Digital marketing
- Finance management
- Gaming
Postgre SQL
What
- Open-souce
- Free and stable
Features
- Extensions: JSONB, Visual code, indexing
- Horizontal scale: scale easily with no application rewrite
- Performance recommendation
- Fully managed: automatic backup, patching, monitoring
Usecases
- Financial apps
- Government
- Manufacturing
Database migration service
Tool to migrate your database from on-prem to azure
Authentication AND Authorization
Right users and processes are let in
Identity service
- How does azure authenticate you authorize you
- What is access management
- Different bw authentication and authorization
Authentication: conforming you’re you. Can be done username/password, face on smartphone
Authorization: let you access of service
Authentication | Authorization |
Making sure you are you | Comes after authentication |
Confirming identity | Do you get access? |
First test for access | Granular control |
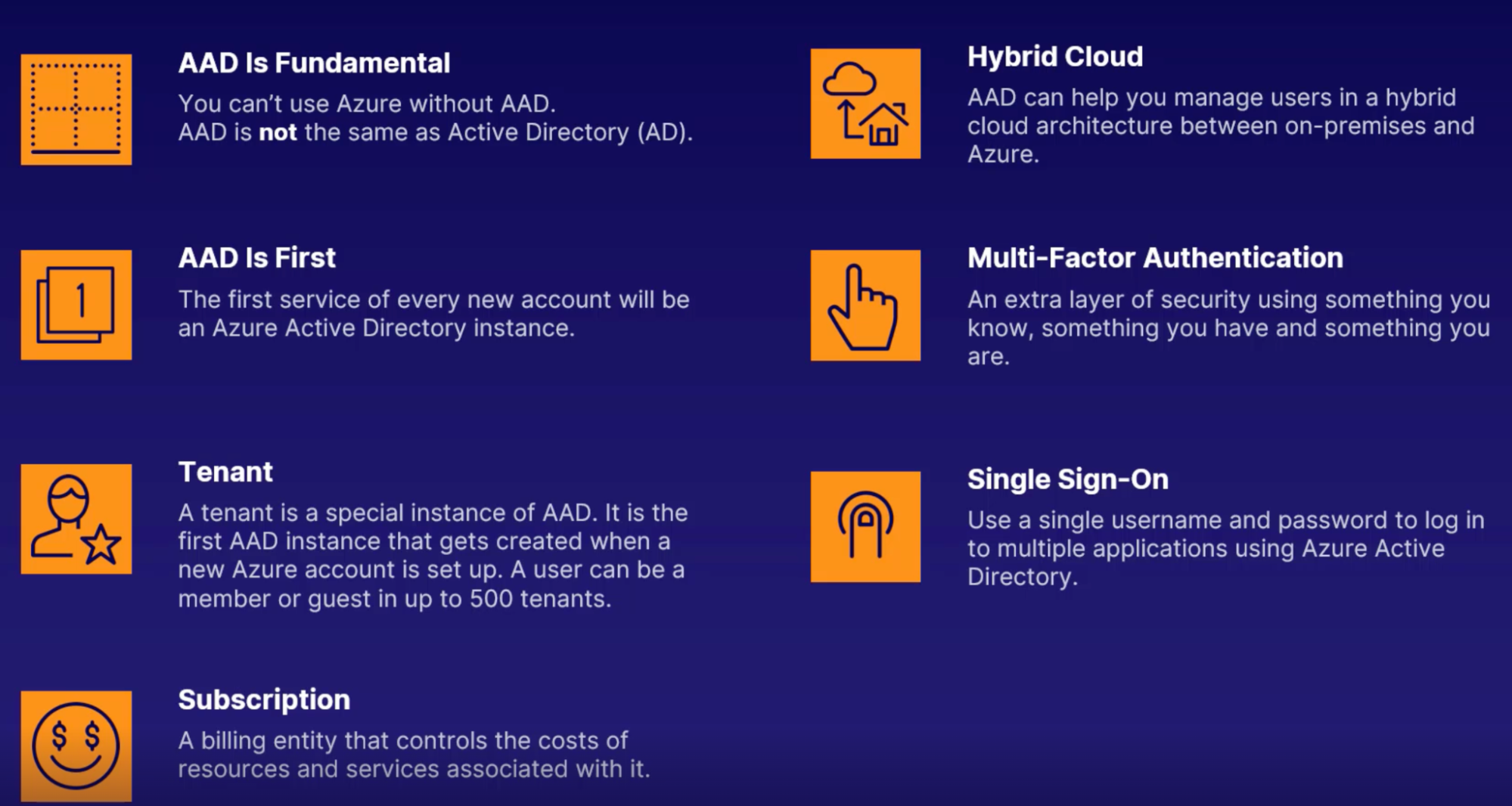
Azure Active Directory
- To manage users and permissions in Azure
- It’s a service like everything else in Azure
Active directory != Azure active directory
They are different products
Active directory | Azure active directory |
Azure’s product which companies host themselves | You can’t have an Azure account without AAD |
| Every Azure account needs a user and this user needs to be in the initial AAD |
| First service you get when you create an Azure account |
Tenant
- Represent the organization
- Dedicated instance of AAD that an organization receives when signing up for azure
- Each AAD tenant is distinct and separate from other AAD tenants
- A single user can belong to max of 500 tenants as a guest or member. Evey user is a member of at least one tenant
- It’s common for a User to be a member of single tenant and be a guest of multiple
Subscription
Billing entry: all resources within a single subscription bullied together
Cost separation: can have multiple subscriptions within a single tenant to separate cost. ex: dev,prod
Hybrid cloud architecture
AAD lets you manage users from on-prem to Azure
Multi-factor authentication
SSO
Lets you use one username/password to signin to different applications
Azure Solutions
Internet of Things
what
The Internet of Things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet without human interaction. These devices range from ordinary household objects to sophisticated industrial tools.
Example:
Imagine a water network for a big city. The water comes from far, far away, and having it running smoothly is critical to ensure people in the city can open the tap and get fresh water. This makes the water network critical.
There will be thousands of valves, pumps, gates, locks, and much, much more.
And if any of these things fail, it could be disastrous for the water supply to the city.
If every single thing was connected to the internet, then if any of them failed, you see it instantly. It would create a much more stable and, over time, much more cost-effective network.
You wouldn't have to spend time and money checking the network constantly in the
field.
2 azure service for IOT
- IoT hub:
- hub to collect data feeds from all your things
- Backend system that receives the data and manages it // can receive data from billions of devices
- These devices are autonomous and do the task without any human interaction, you could have lot of them // billions even
- Managed and secure
- Ease of deployment(devices)
- PaaS
- Scaling and authenitcation
- When to use: when you want more control of the IoT data collection and processing
- IoT central
- SaaS
- Speed up th implementation of your IoT solution
- No coding needed to connect all your things // tool with ready made component
- Pre-made connectors
Azure speare: all in one solution for IoT devices
- Use specific hardware
- Security
- OS
Big Data
Why BigData
- Data is everywhere
- Getting value out of the data to provide better service, product and more profite is great business
- Achieve this through big data
How data collected
- Data from million devices - IoT
- Data keeps changing as we process them
Azure BigData services
- Data lake analytics
- Large amount of data: that you can perform analytical procedures on
- Parallel processing: two or more processes/computers process the same data at the same time paralelly
- Ready to go: don’t need to worry about VM, server or cluster of computer
- HDInsight
- Similar to data lack analytics
- Open source and community supported
- Includes apache hadoop, apache spark, apache kafka
- DataBricks
- Based on apache spark, a distributed cluster-computing framework
- Run and process a dataset on many computers simultaneously
- Provides computing power: You don’t need to buy computers and maintain it
- Integrates with azure storages
- Synapse analytics
- Azure’s data wherehouse offering
- Used to be azure SQL data warehouse
- Used for reporting and data analysis
- Use synapse language to manipulate data
Outcomes
- Speed: processing large amount of data
- Cost reduction: when it comes to store large amount of data
- Better decision making: immediate data processing and analysis in memory
- New products and services: understand customer needs
Machine Learning
Azure service
- Azure bot service
- PaaS offering let you build bots for Q/A, virtual assistant and more
- Language
- Integration: twilio, FB, Teams
- Branding
- Azure cognitive service
- Vision
- Decision
- Speech
- Machine learning studio
- Tool
- Pre-made modules for your project
Serverless
Services
- Functions
- Logic apps
- Event grid

DevOps
Services
- Azure DevOps
- Azure DevTest Labs
- Github & GitHub Action
Security
Defense in depth
What
- Microsoft is giving you multiple layers of security for your cloud infrastructur
Why
- To secure cloud infrastructur
Security leval
- Physical
- This is data center. Only authorized person has access
- Identity and access
- Relates to Azure Active Directory which controls all access to Azure and identity of all users, apps and connections
- Perimeter
- Protection against DDoS Attack, volumetric attack, protocol attacks and more
- Network
- is the filter of traffic to and from Azure using virtual networks and applying security standards.
- Compute
- protects against intruders trying to get into your virtual machines or databases.
- Application gateways and firewalls
- Provides Azure app security
- Data
- is encrypted and protected against anyone unauthorized reading it or making sense of it
Securing network connectivity
Why
- Because network is what gives access to everything. All your services on Azure are connected to a network in order to communicate with users, processors, and other Azure services. // hence protect your network VNet
Azure services
- Firewall
- Rules: decides whether network traffic is allowed to access the service or device attached to the network.
- Variations: firewall come in many versions and sizes. Both in software and hardware incarnations. And for small, big, and huge networks.
- Critical part: network that take security seriously will have firewall
- DDoS (distributed denial of service attack - histroty)
- This is one of the most common attacks on services attached to the internet.
- Attacks
- U.S Banks were flooded with 60 GB of traffic every second in 2012
- CloudFlare was attacked in 2014 with 400GB of traffic per second
- GitHub in 2018 with 1.35TB traffic per second // new record for DDoS attack
- What is DDoS
- server can only serve, or handle, a certain number of requests every second. Let's say, 1,000 requests. If too many users come into the site at the same time (let's say 10,000), at some point, not everyone would get through.
- The server would try to serve all the requests for its content until it would fall over. At some point, the server hasn't got enough resources and it simply stops.
- If this is done on purpose to take the server out,it is called denial-of-service attack.
- How DDos
- Many internet connected devices: lots of computers targeting a single server or website with the aim of making it stop.
- Azure DDoS protection service: detects the DDoS attack and deflects it
- No downtime: no interruption of service at all
- Network security group
- Resource firewall: personal firewalls for your resources.
- You can attach an NSG to any virtual network, subnet, or network interface which is attached to a virtual machine.
- Rules: rules for who and what can access any resource attached to the NSG.
- Example: if you have a virtual machine that is on a virtual network, the network can be behind a firewall protecting everything on the network, and then the VM can have its own network security group to define specific rules for just that machine. // two security level, firewall and NSG, provides extra layer of security to VM
- Application security group
- Protects app infrastructure: focus the security on the app rather than IP endpoint
- Natural extension: group VMs and VNet into logical application groups and apply an application security group
Public and private endpoint
What for
- Secure access to azure managed services like PaaS

- Service endpoint
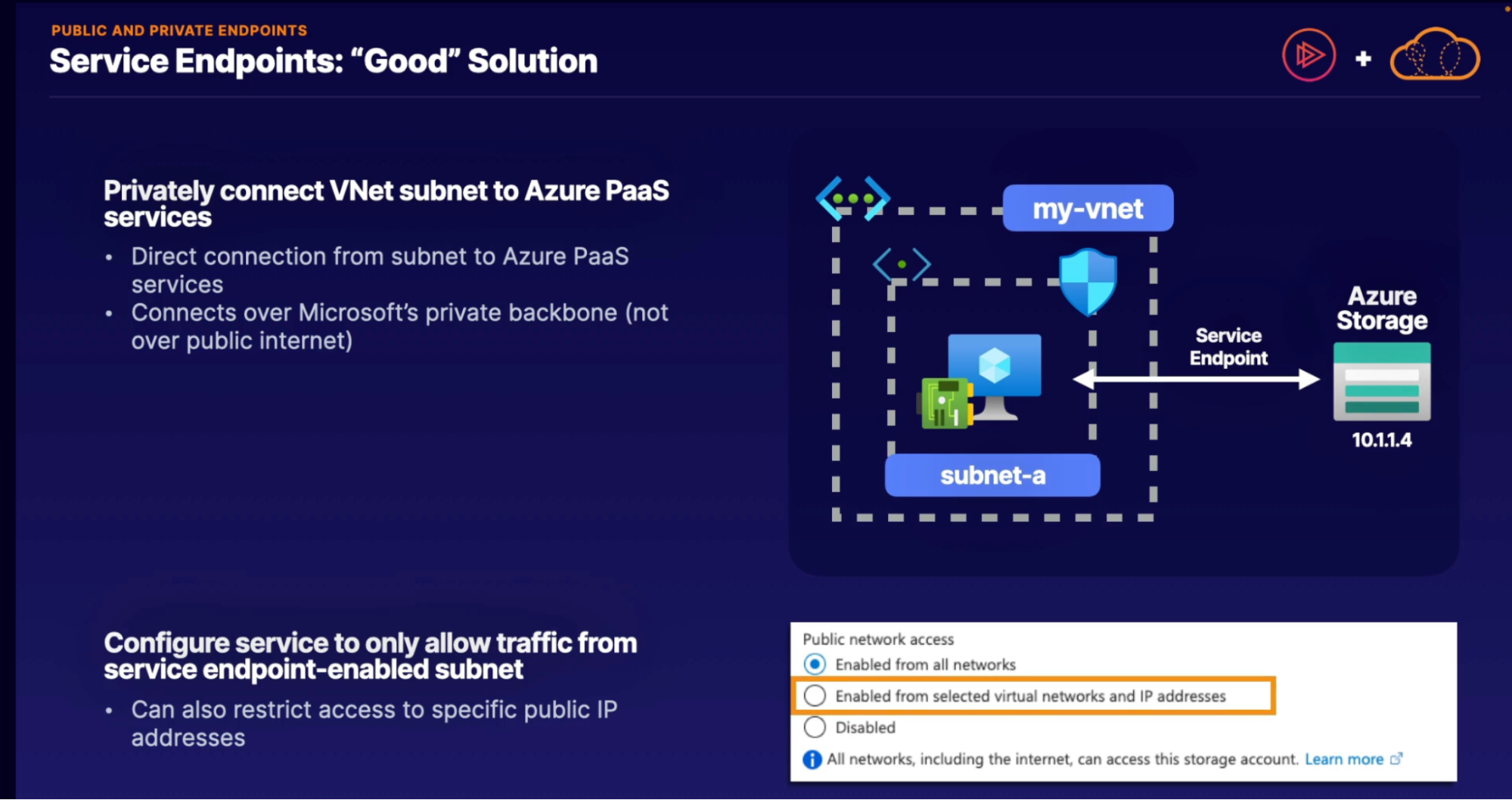
Limitations:
- Secure access to VNet only:
- no private, on-premises access
- Must allow on-premises access over public IP
- PaaS public endpoint still exists
- Connection is still not private
- Service endpoint provide access to an entrie service
- Provides private access to all of storage accounts, not just a single storage account
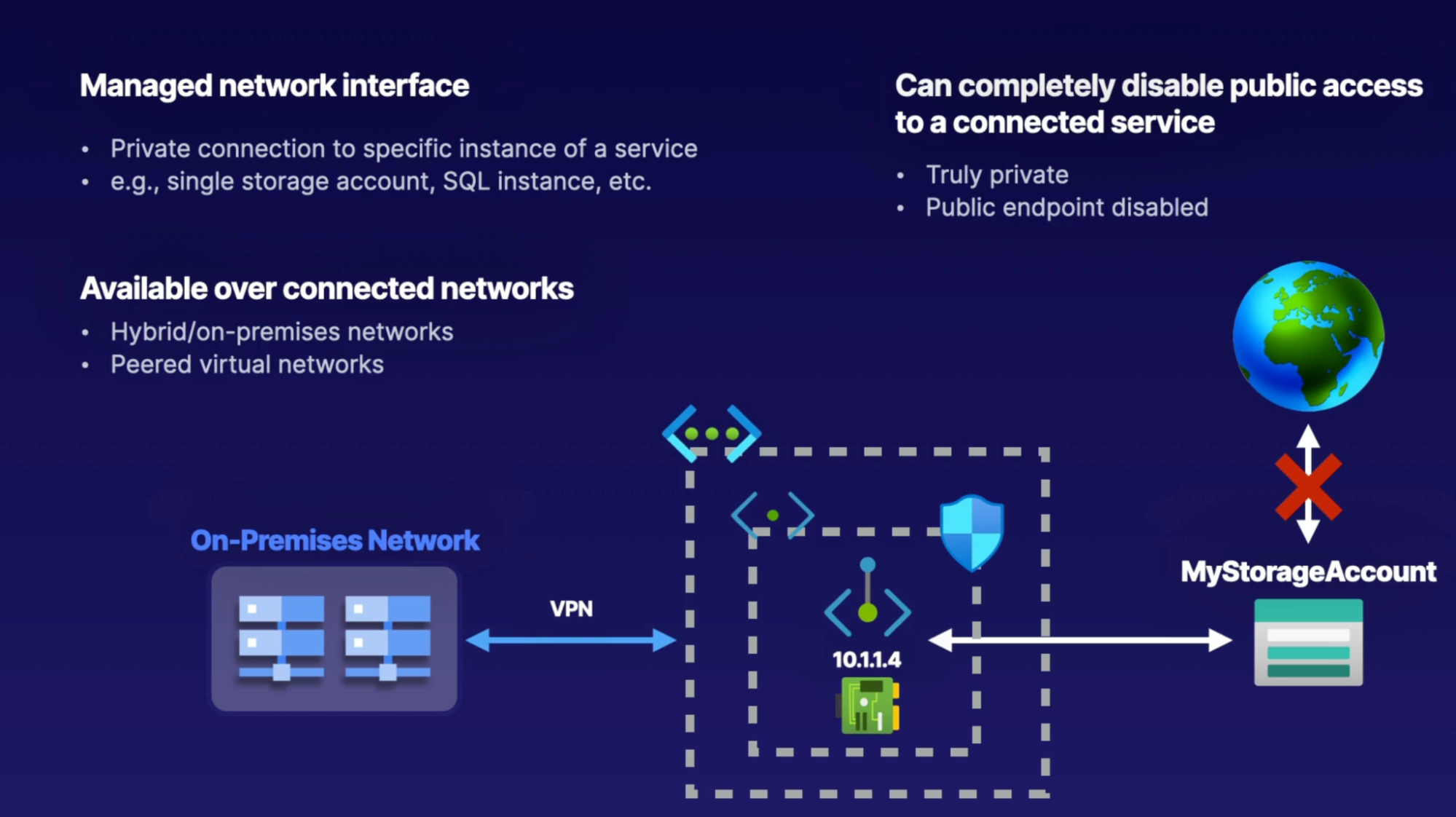
- Private endpoint

Microsoft defender for cloud (formerly azure security center)
The Azure Security Center is a portal within the Azure portal
What
- Threat alert: It alerts you to threats that Azure detects
- Ready for hybrid architecture
- Each VMs has an agent installed that send data to azure
- Azure analyze the data and send alerts if necessary
Highlights
- Policy and complience metrics: are monitored by Azure, and the result is shown in the Security portal
- Secure score to entice great security hygiene: to make your Azure implementation as secure as possible.
- Integrate with other cloud providers: AWS, GCP using SEIM tool // provide single point for any muti-cloud security information
- Alerts for resources that arn’t secure
How to use
- Define polices: A security policy is a set of rules that Azure can use to evaluate if your configuration of a service is valid. Security Center comes with some predefined policies, but you will need to set up your own
- Protect resources
- Response
Azure key vault
- Secure hardware: not ven microsoft can access keys
- Application isolation: app can’t pass on secrets, nor access another app’s secret
- Global scaling: scale globally like any other services
Azure information protection
Why
- Secure documents, email, and data outsite the company network
When
- To help an organization classify and (optionally) protect its documents and emails by applying labels
- Classify data: on how sensitive it is wither using policies or manually
- Track activities: track what is happening with shared data and revoke access if needed
- Share data: safely share data s you can control who edits, views, print and forwards it
- Integration: microsoft office
How to use
if Melanie has to send an email with a sensitive attachment to Tony, then she can use Azure Information Protection to secure that attachment.
Melanie uses a label that is defined in Azure to tag the document and create a link to Information Protection. Every time a user opens it, the user is validated and the document is protected.
Azure sentinel
What
Sentinel is a security information and event management tool, often just called S-I-E-M or SIEM
When
- There is a potential threat to your Azure infrastructure from an outside attacker. Which service is best for detecting the threat and taking action
How
- Data is collected from range of sources. Ex: DNS, VM, Network
- Aggregation and normalize data // more usable
- Analysis and threat detection
- Things happen (mostly magic)
- Take action
Features
- Bahaviour analytics
- AWS integration
- Cloud scale
- Netflix uses it
Azure dedicated host
When
- When you don;t trust hardware your VMs runs on
- You want to run VM on a hardware you control
What
- Hardware control
- Maintenance: reduce impact on your system by choosing when to install updates to your dedicated host
Benefits
- Compliance
- Global infrastructure
- OS of your choice
It’s Expensive
Microsoft defender for identity (formerly Advance threat protection)
What
- Monitor users: helps you monitor users in your on-premises environment and their behavior. It analyzes user activity and information across your network, including permissions and membership for each user.
- Baseline behaviour: record what a user’s normal behaviour and routine is. Any activity outside of the routine will be logged as suspicious
- Suggest changes: to meet best security practices
- Cyber attack kill chain
- Reconnaissance
- Brute force
- Increase priviledges
When
- Helps you monitor user behavior in your on-premises and cloud environments
Privacy, Compliance And Trust
Azure allows you to apply consistent management and policies across your Azure resources,
use Azure Monitor to gain greater visibility into the performance of your Azure environment, and some supplemental lessons on Azure compliance
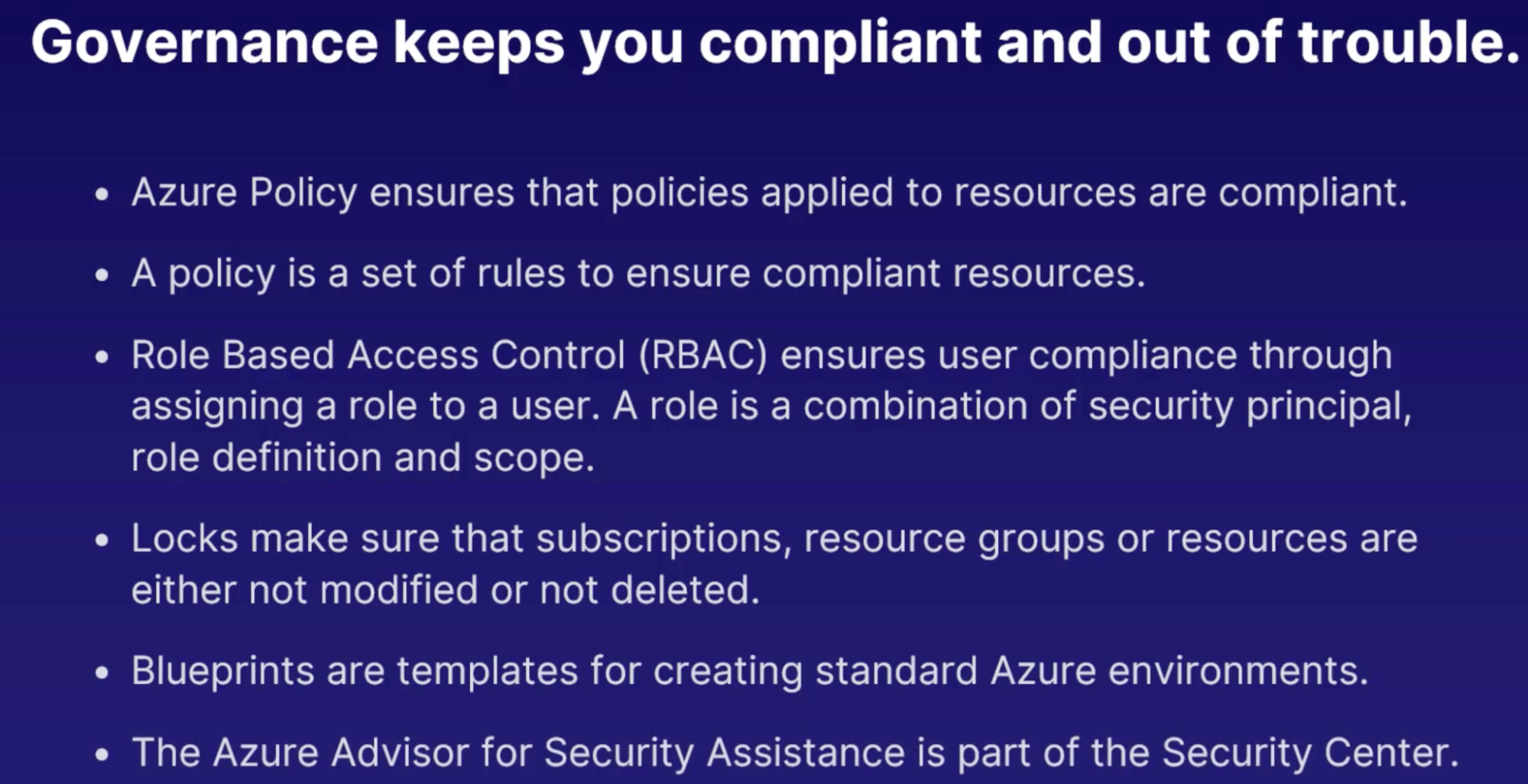
Governance
Tools & service
To implement adequate governance of your azure resources
- Policies: Azure Policy documentation states, governance validates that your organization can achieve its goals through effective and efficient use of IT. In other words, use Azure Policy to make sure users don't make a mess of it.
- What: set of rules. Rules to make sure that standards and agreements within your corporation are followed and that resources are compliant with these policies
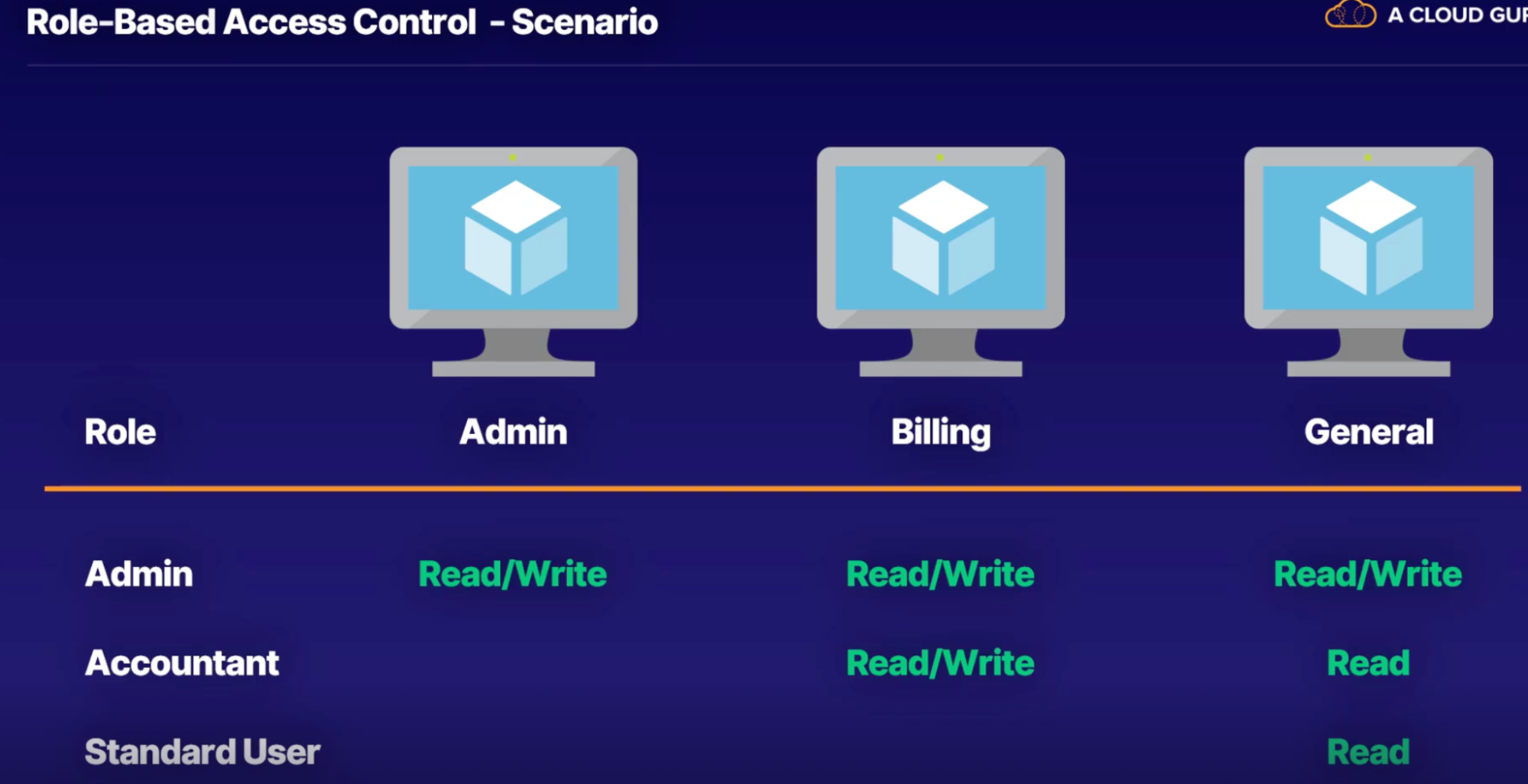
- Role based access control(RBAC): lets you define which users have access to specific Azure resources, what they can do with those resources, and what areas they have access to.
- Define user access
- Minimum access
- Target specific use cases
How RBAC works:
- Security principal: is an object that represents what type of entity can get access to the Azure resource. This can be user or group of users, for example. A role definition is a collection of permissions.
- Role definition: lists the operations that can be performed, such as read, write, and delete.
- Scope: is the set of resources that the access applies to. This is useful when you want a specific role assignment to have only access to a specific resource group
- Locks: efficient tool to manage changes and removal of resources are
- Assigning: assign a lock to a subscription, RG, resource
- Types: delete(can’t delete locked object), read-only(where you can’t make any changes to object)
- Blueprint: are templates for creating Azure resources
- Cloud adoption framework
- Collections of document
- Guidance
- Governance
- Azure advice for security assistance
Azure monitor
- Helps you find resources tha are not performing 100%
- Telemetry: info on how services are performing and this info pass to central point for further analysis
- In azure, most services feed telemetry data into azure monitor.
Why
- Maximize performance
- Maximize availability
- Identify issues
Monitoring tools
Log analytics
- Lets you analyze logs/telemetry data
- what?
- It allows a storage location for large logs/data and let you query and anayze data to gain valuable insight.
- Ex: disk size of VM, VPN connection logs, long term analysis, combine metrics for complex queries
- Prebuilt and custom query // Kusto query
Application insight
- Tool for Performance insight for your web application
- Answers
- How are users using the app?
- Where are our performance bottlenecks?
- Why are we getting website error?
- For what
- Works only for web based application
- Available for App service, azure VM, non-azure resources
- How
- VM required agent install
Azure Alerts
- When something breaks, send alert to someone
- Example:
- VM Unresponsive
- VM using excessive CPU
- Application latency over 500 ms
- How?
- Alert rule
- Monitored resources // VM
- Monitored telemetry // CPU Utilization
- Condition to trigger alert // 90% CPU for 5 mins
- Assigned severity // 2 - warning
- Action group - action take when rule is triggered
- Notification target -
- SMS/Email to support people
- Send to automation workflows(logic apps, functions)
Azure service health
What
- Notify about any planned or unplanned incidents on the platform
Features
- Dashboards
- Custom Alerts
- Real time tracking
- Free service
Scenarios
- To track incidents with your services in real time and get a report afterwards
- To set up custom alerts to notify you of any outages, planned or otherwise
Compliance
What
- GDPR - general data protection regulation
- Why: to protect individual and processing of their data
- Gives control of personal data, instead of the company owning it
- Companies need to implement lots of tool for consumers to control their data
- ISO standard
- Compliance with quality and customer satisfaction
- Covers industry(food safety, environment management) and standards for range of professions
- NIST - national institute of standards and technology
- Focus purly on tech industry
- Developed primarily for US federal agencies
- Compliance with NIST means compliance with multiple federal US regulation
When
- Companies of any country must adhere to GDPR if their users and customers are located in the European Union.
Tool
Azure compliance manager
Benefits
- Recommandations: get recommandation for ensuring compliance with NIST, ISO, GDPR
- Tasks: assign compliance task to team member nd track progress
- Compliance score
- Secure storage: upload documents to prove complience and store them securely
- Reports: get report of compliance data to provide to manages and auditors
Azure government cloud
- Dedicated region
- Exclusivity
- Compliance
- Azure benefits
China region
- Located in china
- Data is kept in china
- Compliant
Why compliance
- Non-complience cause heavy charges and hence not negotiable

Privacy
- Azure info protection: classify, label, nd protect data based on data sensitivity
- Azure policy: define and enforce rules to ensure privacy nd external regulation
- Guids: use guids on azure to respond and comply with GDPR privacy request
- Compliance manager: make sure you’re following privacy guidelines, GDPR, ISO
Trust
Services
- Trust center:
- How Microsoft’s efforts on security, privacy, GDPR, data location, compliance and more
- a hub for more information about trust in each product and service
- Service trust portal:
- review all the independent reports and audits performed on Microsoft products and services
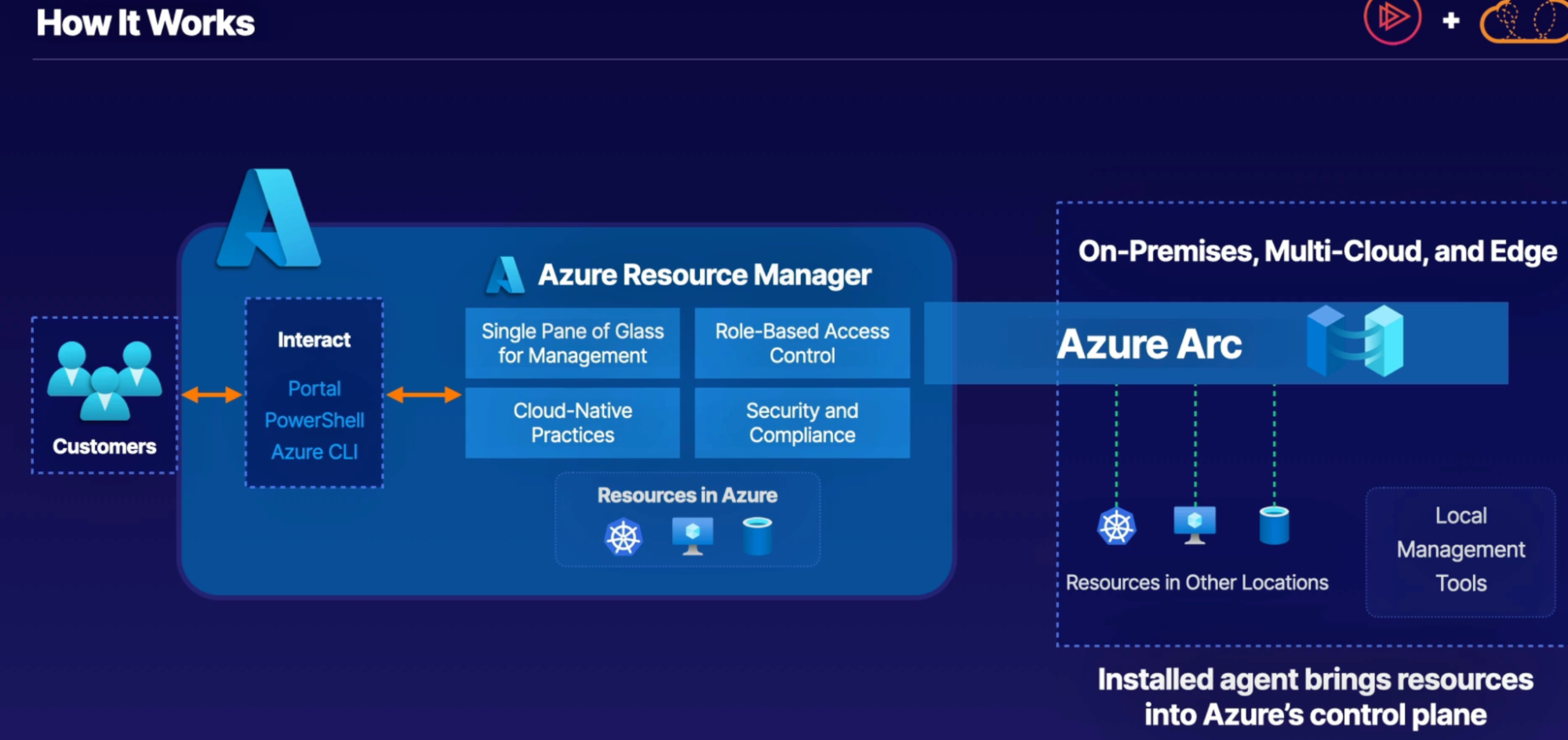
azure Arc
what
- centralized governance and management for on premises and multi cloud computing resources
- manage non-azure resources as if they were in Azure
- extend Azure cloud management and services to non-Azure locations
How
Benefits

Scenarios
- you maintain servers in both azure and on premises data centre
- you want to apply Azure management services (azure blueprint, azure policy, RBAC) to the servers.
- solution is Arc: To extend azure control plane to your non-azure sources in a single place
Price
Subscriptions
- Multiple Subscriptions: useful for organization for who pays for what. Dev, prod
- Billing admin: one or more more user can be a billing admin which manages anything to do with billing and invoicing on azure. Ensures separation of responsibility
- Billing cycle: billing cycle is either 30 or 60 days
Management groups
- Group subscription
What: Tool for managing azure subscriptions
- Allows taking actions in bulk across subscription
When your organization has lots of subscriptions
- Organize
- Manage access, policies and complience in bulk
- Ex: have a management group per country or department
- Billing logic
- Maintain billing associated with right budget
- Nest management groups to indicated hierarchy and relationships
Cost management
To Visuslize your spending
Get reports and recommandations
Optimizations: to save money
Spot VM
- Save money by sing unused capacity
- VM can be evicted by any time
- Use for interrutible non-critical workloads
- Use with azure scale set
- Set a max price for spot VM
Pricing factors
Factors
- Resource size
- Resource type: and complexity
- Location: prices comes different with different location
- Bandwidth: howmuch data is coming to in and out to azure
Billing zones
Azure has three billing zones in the world as well. Each of these zones include many Azure regions.
Any data transfer between Azure services located in the same zone is free.
Any data transfer between two different billing zones is charged.
Ingress → data in, egress → data out.
Ingress data is always free, but egress data has a cost with it when it is transmitted between two different billing zones.
Azure pricing calculator
- To calculate service usage price
Total cost of ownership calculator
- Estimate total saving over a period of time by using azure
- Comprehensive reports to share with stakeholder
Best practices
- Spending limits
- Default limit:
- No increase spending limit
- No spending limit on pay-as-you-go accounts
- Quotas
- Property limit
- quota is a limit on a certain property off in Azure services. for example a minimum of 100 name spaces for Event Hubs
- Ensure service level
- The quotas are necessary to ensure as you can maintain their high service level
- Quota change
- if you need to increase the quota for a particular service you can ask Microsoft to increase them
- Tags
- Labels that you can attach with your resources, RG
- Identify roles
- Related resources
- Filter
- Unambiguous
- Pay-As-You-Go account
- Reserved instance
- Can save a lot of cash
- Use for small azure services and products. Especially VMs
- Reserved capacity
- 1-3 year commitment
- Ex: database: SQL(80%), Cosmos DB(65%), Synapses Anaytics(65%), redis cache(55%)
- Azure hybrid benefits
- Saves on VMs and SQL server if you already have licence for them
- Azure lets you use your existing licences instead of purchasing new one with every new VM,SQL server
- Advisor
- Give you best practices and recommendations

Credits
