Linux Essentials 2
Links 2
Linux distribution 2
Example of Linux Disto 3
Linux embedded system 3
Linux in the Cloud 3
Linux Commands 4
Directories 4
Basic Commands - 1 4
Process Commands - 2 4
Log Command - 3 5
Tar Commands - 4 7
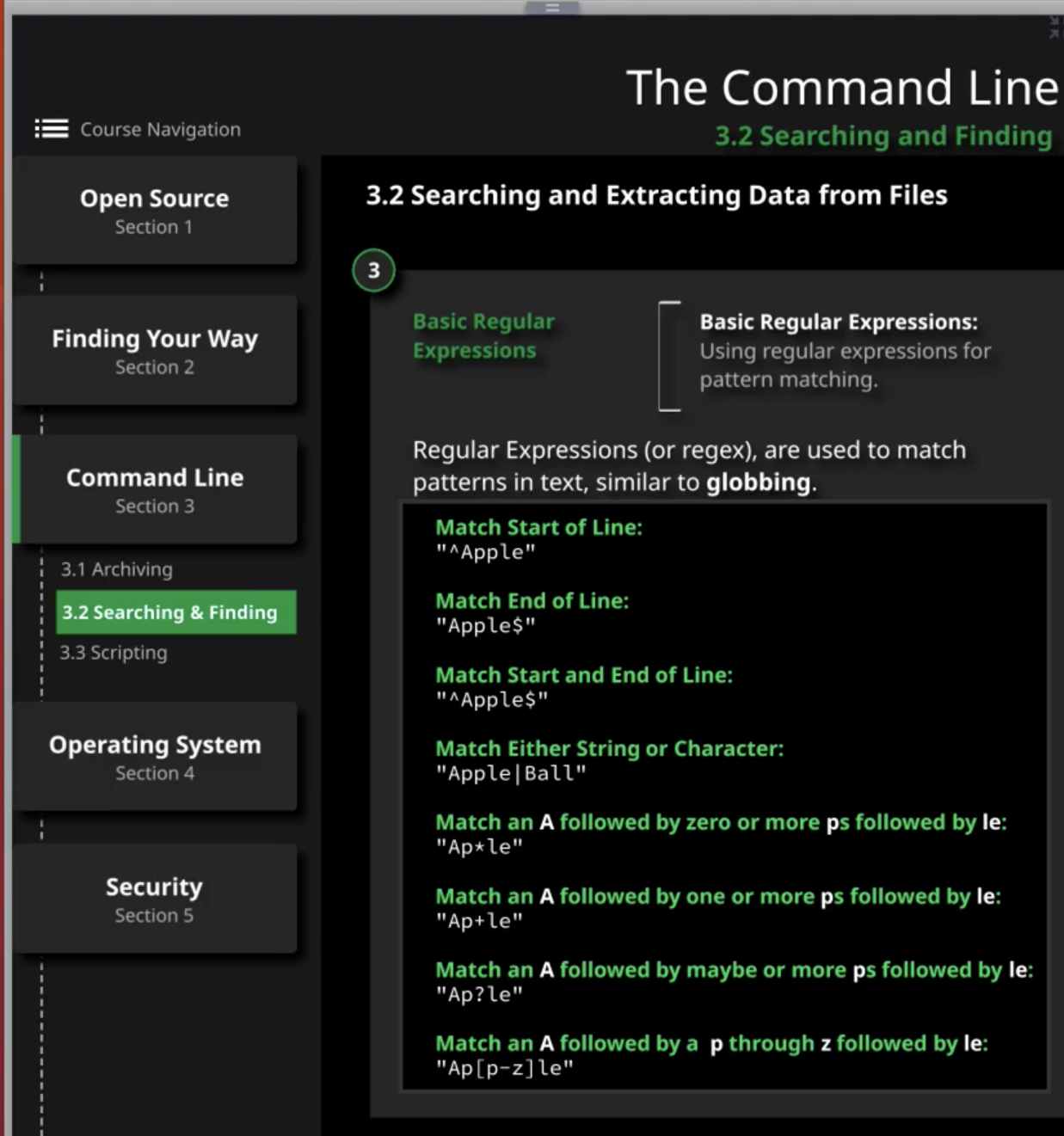
Searching data Commands - 5 8
Hardware Command - 6 10
Network Commands - 7 11
User/Permission Command - 8 12
Applications 13
Desktop application 13
Server applications 13
Chronology of source code to executable file 14
Package management tool 15
CLI 15
How it works 15
CLI Syntax 15
How it works 15
Variables 15
Quoting 16
Man & Info command for Help 17
Linux directories and file system 17
Linux OS 18
Internet, Network and Routers 19
User and Groups 21
Linux - LFCS 23
Essential Command 23
Find/Locate 23
which/whereis/type 23
File Systems 24
Manipulate File Content 25
Redirection operators 26
Regular Expression - Regex 26
Archive/Backup/Compress/Decompress 27
Hard/Soft Links 28
File Permissions 30
Manage access to the root account 31
Tasks 31
1. Backup App via archive by Tar 31
2. Add/Change execute permission to files and view/change attribute 32
3. Finding Files, and Assigning Permissions and Ownership 32
4. Transfer Files Securely Over the Network 33
Operation of Running Systems 33
Boot, Reboot, and Shut Down a System Safely 33
Linux Server Troubleshooting Guide 34
Methods 34
Commands 34
Scenarios 35
Kernel Buffer Commands 35
Virtual Memory Commands 35
PID Status Commands 36
Linux Essentials
Links
LE: https://lucid.app/lucidchart/fc06cd7d-70f2-494a-843b-5d86ffb4331e/view?page=8L66hCFYoXKS#
LFCS: https://lucid.app/lucidchart/e5ec169f-ec73-4171-85e6-79fefdfea848/view?page=0_0#
Linux distribution
- Collection of components that form a system
- Graphical interface // Optional
- GUI to click and go around
- Enable us to use graphical user interface or GUI
- Is the basic OS commands enables us to use Linux in an interactive manner
- Ex: ls, file commands etc
- Foundation of OS
- Permit applications to interact with the hardware and use the hardware as a compute(CPU, RAM, Storage) resource
- Hardware // all above components run on hardware
- Linux dist is installed as an OS on to the hardware
Example of Linux Disto
- Red hat enterprise Linux (webserver choices)
- CentOS (webserver choices)
- Ubuntu (Mint is a fork version of Ubuntu)
- Fedora
- Debian
- Open SUSC
Linux embedded system
It’s a combination of hardware and software for a purpose
- Applications that fulfilling the purpose of the embedded system
- These applications uses library to function
- There are high level OS abstractions or the OS components that applications make use of it
- Networking: to connect to other devices
- File system: for files to live
- Low level interface: needed to support function of the device
- Hardware: everything sits on
Example: android and raspberry pi
Linux in the Cloud
- Fault tolerance: if you have a failure in one place(region), you can move services to another place
- Redundancy:
- Region: region is collection of AZ
- Availability Zone: data centers
- Subnet: local network instance for the compute resource in the cloud
How to SSH/Connect to a remote server
- Ssh User/Host_Name@RemoteHost_IP (public address)
Port used: 22/TCP
Linux Commands
Directories
https://opensource.com/life/16/10/introduction-linux-filesystems
- /etc = stores system configuration
- /boot = linux kernel configs and files
- /sys = where the data is stored;
- sudo file system where kernel gives info about systems
- /proc = sudo file system where kernel gives info about processes
- /dev = device
- /tmp = directory that holds large less important files. Files will be deleted upon booting the system
- var/temp = hold more persistence file. Files will be deleted after 30 days.
Basic Commands - 1
Command | What it does |
whoami | Return user name |
uname -a OR -r | Which Kernel is this |
cat /etc/*release* | Show which distro you are on |
pwd | Print working directory |
cd ~ | Change to home directory |
cd / | Changes to root directory of file system |
ls | List of files Ls -a // prints hidden files(starts with .) |
W > log.txt | Redirect the output into text file |
Last >> log.txt | Append output to the same text file
|
grep -i usb | Prints usb from the file // -i = casing doesn’t matter |
Process Commands - 2
Process and PID: In Linux, when an executable stored on disk is called a program, and a program loaded into memory and running is called a process. A process is given a unique number called process ID (PID) that identifies that process to the system, when it is started
w | Anyone logged in |
last | Shows last person to login and last time system rebooted |
uptime cat /proc/loadavg | Shows howmuch time the server is up - What is the current system load
|
cat /etc/passwd | wc -l | This file has all the users on a linux |
sudo dmesg | sends info about kernel (hardware related info) |
htop | Shows running processes on a host - Gives processes that using the most CPU
- Useful for troubleshooting load issues
|
ps aux
ps aux | grep Gautam | wc -l
ps -eF | grep Gautam | wc -l
ps -U User_Name | wc -l | Dump out all of the processes
To grab howmany your process is running
the Same result as above
Howmany process running as given user name
|
ps aux | grep process_name | Grab process ID(PID) of given process name |
cat /proc/PID/status | grep threads | Grab howmany threads is the process running |
service S_NAME status | Which linux service is running |
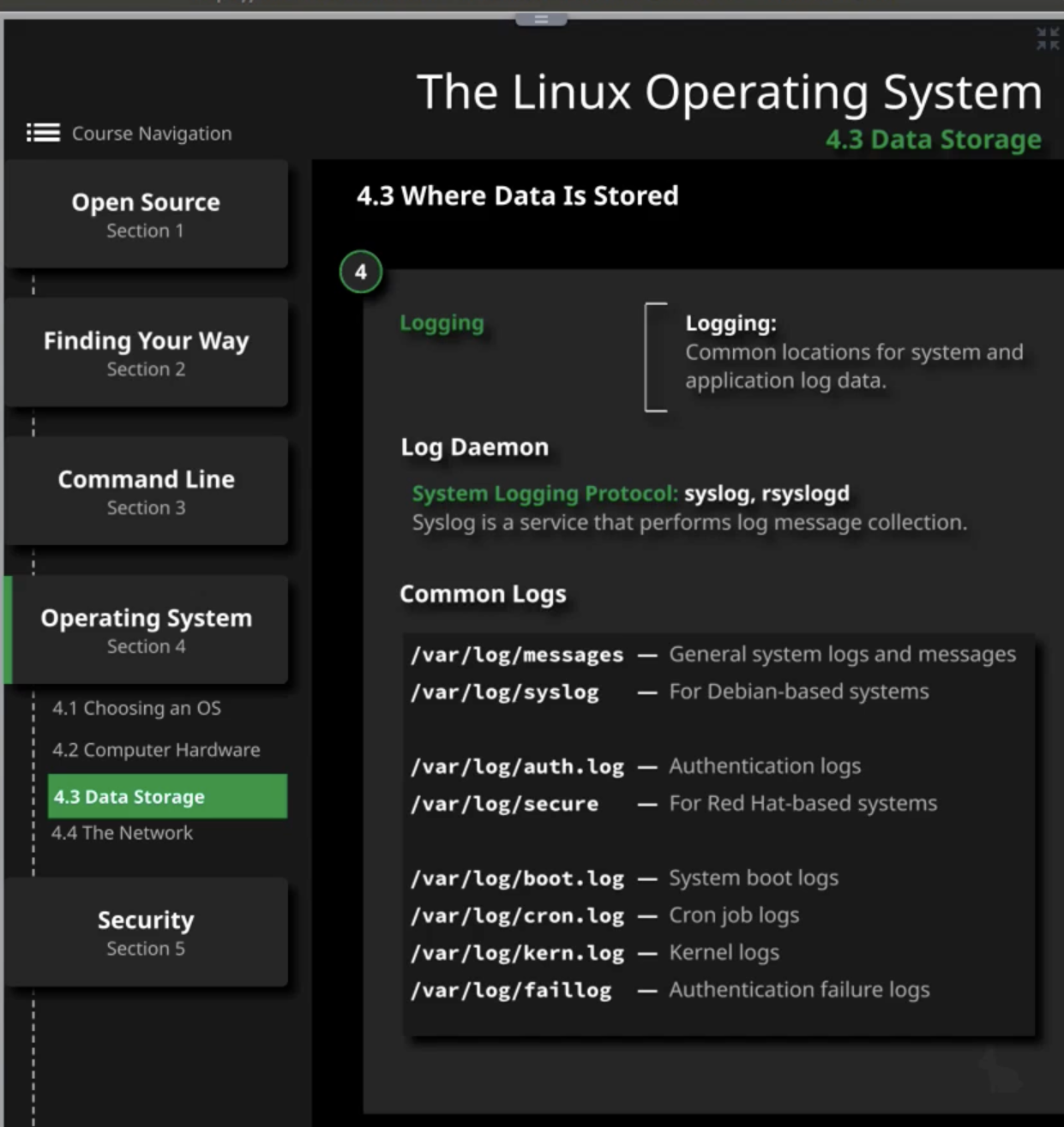
Log Command - 3
/var/log
Examples:
sudo cat /var/log/httpd/access_log | grep -E “^10.0.1.10” | All general logs saved here
Howmany time has 10.0.1.10 has access the site
|
last | Shows last person to login and last time system rebooted |
Tar Commands - 4
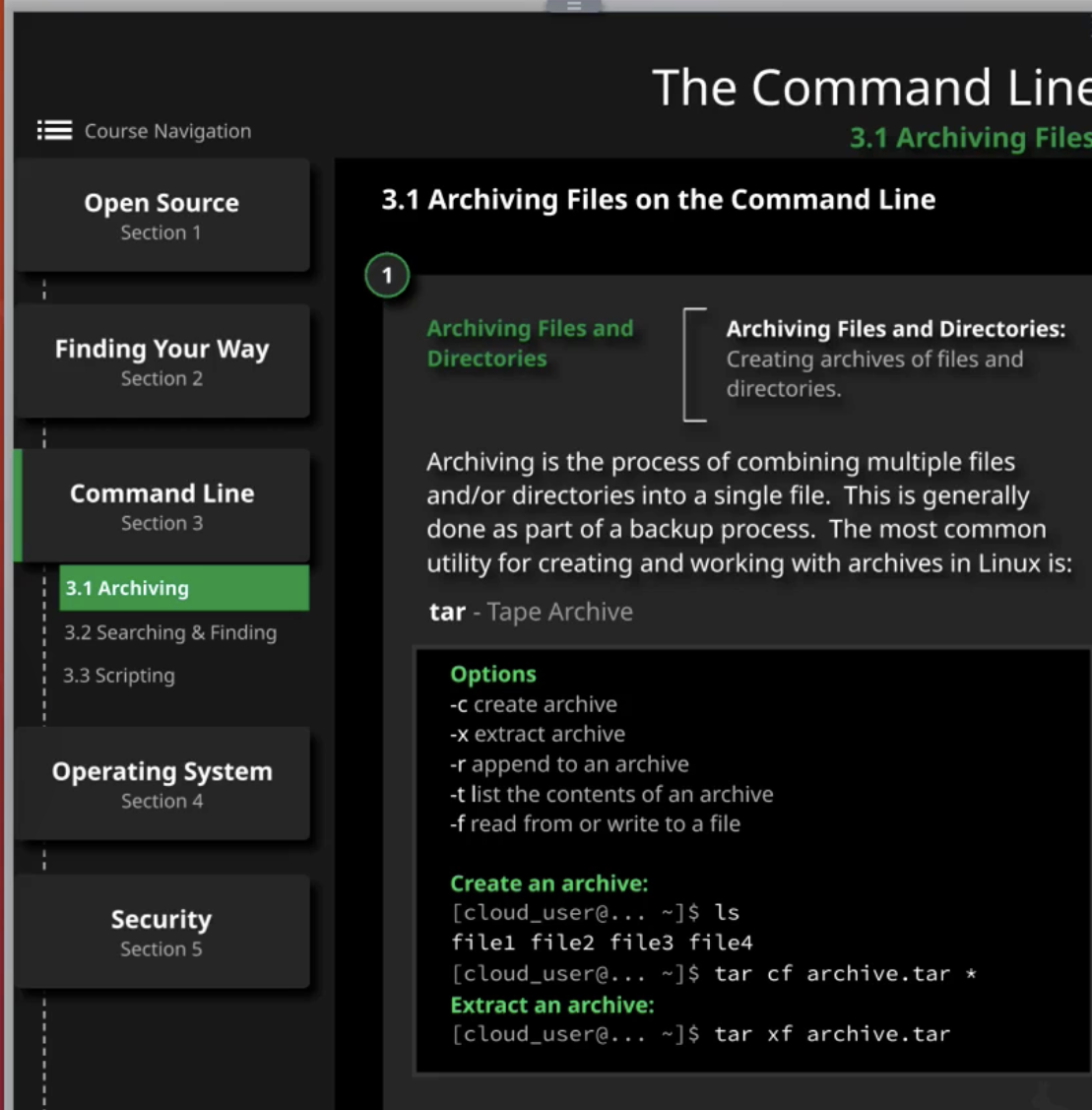
tar cf archive.tar test_file_* | Archive test_file_* into archive.tar |
tar tf archive.tar | Look through/List files in the archive.tar |
tar rf archive.tar file? | Append/add additional files into archive.tar |
tar xf archive.tar file3 tar xf archive.tar // extract everything | Extract specific file from the archive.tar |
tar xf archive.tar –wildcard ‘test_file_?’ | Extract list of files using globbing(?,*) via wildcard |
tar --delete --file=archive.tar file3 | Remove file from archive.tar // edge case |
tar czf archive.tar.gz file_* | Compress(to reduce file size) file via tag czf // gzip algorithm Why?: if you’re running on low disk space |
tar cjf archive.tar.bz2 file_* | Compress(to reduce file size) file via tag cjf // bzip2 algorithm |
zip -r archive.zip file_*
| Compress(to reduce file size) file via option -r // zip algorithm |
Searching data Commands - 5
cat gautam.txt | grep Apple | Prints the total number of word Apple |
cat gautam.txt | grep Apple | wc -l | Prints the total number of line that contains Apple word |
cat /etc/passwd | grep gautam | cut -d: -f6 | Prints the home directory for gautam user How: - Cut the whole line from : (-d is delimiter where do you want to make this cut)
- Takes the field from 6th position
|
grep -E ^M gautam.txt | Match everything in line that starts with letter M -E = find pattern as an extended regular expression |
grep -E “apple?” gautam.txt | Search anyline that ends with apple $ = match end of line |
grep -E “apple|ball” gautam.txt | Search for either result via | |
grep -E “Ap*le” gautam.txt | In line; Match an A followed by zero or more ps followed by le. // doesn’t have to be line start with a, it searches in line and not from the beginning of the line |
grep -E “Ap+le” gautam.txt | In line; Match an A followed by one or more ps followed by le. // doesn’t have to be line start with a, it searches in line and not from the beginning of the line |
grep -E “Ap?le” gautam.txt | Match an A followed by maybe more ps followed by le. |
grep -E “Ap[p-z]le” gautam.txt | Match an A followed by p through z followed by le. |
Hardware Command - 6
df -h | How much storage is available Disk free -h(human-readable) |
cat /proc/cpuinfo lscpu
sysctl -n hw.ncpu OR sysctl -a | grep machdep.cpu // for mac OS | How many CPUs/cores CPU speed (model name) |
sudo dmidecode sudo lshw | Info about motherboard // under memory device you’ll find size = RAM |
free -m | Howmuch swap is being used // IMP |
sudo lshw | BIOS version Lshw pull infor about montherboard |
du -sh DIR_NAME | To check the size of the directory du = disk usage |
mount ABSOLUTE_PATH /mnt mount downloads/work /mnt | To mount on disk |
Network Commands - 7
Ifconfig | View and change the interface configuration |
sudo ip addr show | To determine the IP address - Loopback device(internal device used by linux)
- eth0(actual NIC)
- return IP address of the host
- Returns MAC address // link/ether
|
ping -c1 www.google.com
curl -I www.google.com | Connect to google server | test connectivity
To make the connection // make sure the DNS is working correctly |
sudo ip route show OR ip r s | Determine the gateway |
cat /etc/resolv.conf OR cat /etc/resolv.conf | grep nameserver | Determine DNS server (Name Server) - This is the host that any DNS query going to go to
|
dig www.nike.com | Translet domain name to IP address with more info (question[give me internet record] section and answer section) |
host www.nike.com | Translet domain name to IP address | DNS lookup using configured DNS - Use Host for Lightweight DNS work
|
dig @1.1.1.1 www.nike.com OR dig www.nike.com 1.1.1.1 | If you can’t ping google.com tell some other (external)DNS address to perform the lookup for you AND this also means your own DNS is borken and that is fixed in /etc/resolv.conf |
netstat AND ss
netstat -tulpn | View listing service and active connections - Destination
- Gateway
- genmask , flags, etc
|
Find and determine network configuration
User/Permission Command - 8
cat /etc/passwd | List of users in linux |
su - User_Name | Change from one user to another |
sudo cat /etc/sudoers | See what permission assigned to all users |
sudo visudo | To edit permission file |
sudo su - | To go to sudo user from your user |
Id gautampambhar OR cat /etc/group OR
Groups | What group a user belong to |
Getent passwd gautampambhar OR cat /etc/passwd | grep gautampambhar | What is user’s home directory |
sudo /etc/shadow | To see the password hash of the users |
|
|
sudo useradd gautam2
sudo passwd gautam2 | To add a new user - Asked for the current user password
Set a password of a new user |
sudo useradd -m gautam3 | Ideal way to create a user with having following |
sudo groupadd admins
sudo usermod -a -G admins gautam3 | Add a group
Add user to a group
You have to logout and log back in to see yourself into this group or reload profile( . /etc/profile) |
sudo passwd -l User_Name | Blocking user account password |
sudo userdel User_Name | Delete user |
sudo chown -R user:group /home/deletedUser | Replace new user to the group with the deleted user’s group |
When you create user
- Set his home directory // sudo mkhomedir_helper gautam2
- Set his password
- Specify the login shell // sudo usermod -s /bin/bash gautam2
When you create group
- You can set it’s own permission(by vim sudo visudo) without adding this group into root group
- Add user to this groups
Applications
Desktop application
Server applications
Server provides client services
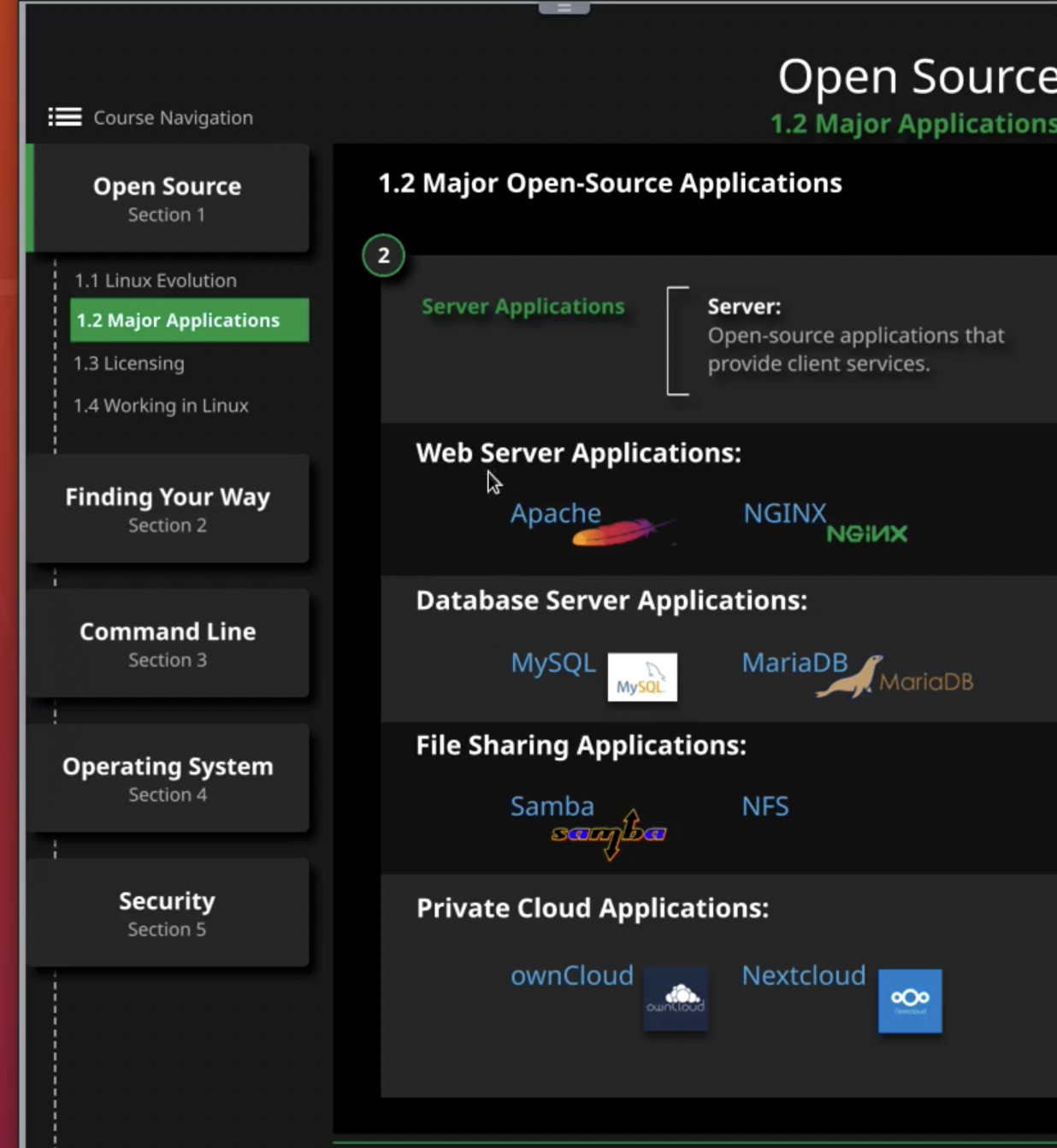
Ex: apache, nginx (free open source web server)
- Your computer connects to the internet
- Apache/another computer having applications connects to internet serve content to your PC
- Apache listens on a port ex: 40, 443
- Listening for incoming connections
- Listen to request through a web browser and serve content
- Developers will host theirs files on apache; apache host will host these files and serve them as web content for incoming request
Nginx
- Reverse Proxy: proxy request for something else
- Load balancing: balance incoming request
- Mail proxy
- HTTP caching
Programming language, For example, C#, Bash, Python, etc
Chronology of source code to executable file
- You write code in C; your source code in C
- You then use a compiler to compile that code into binaries
- Binary then is executable ex: firefox
Package management tool
- How installation packages are tracked and managed
Issue: application needs to install dependencies which also depend on other dependencies
Resolve: package manager like apt-get and yum, which installs the complete dependencies/applications that applications need
How?: It downloads the library and packages from the software repository and installs on the host machine
Ex:
- dpkg: debian package
- Apt-get: allows automated update and package dependency management to solve problem of dependencies hell for debian linux distro
- rpm
- Yum: allows automated update and package dependency management to solve problem of dependencies hell for redhat linux distro
CLI
How it works
- It reads the input from your CLI
- Process input by interpreter
- Executed via application
$ stands for ready to take user input
CLI Syntax
Command [option] [file]
Ex: ls -l
How it works
- Read the input
- Divide the input with ignoring comments
- Apply quoting
- Parse into commands
- Apply redirection (by piping)
- Wait for exit status
- Display output (read output)
Variables
To store value (number, character, string) and reference it later
Use case
- a=”hi”
- Use variables to store output from certain commands
- a=$(ls)
Quoting
Methods of quoting
- Escape character: preserves the literal value of the next following character
- Single quotes: preserve the literal value of variable
- Ex: echo “this is $a” // “this is $a” // It won't print the value of $a
- Double quotes: preserves the literal value of most characters contained within quotes, exception includes $, ‘,\
- Ex: echo “this is $a” // “this is gautam” // It will print the value of $a
- Ex: echo “this is a \”quotes\”” // this is a ”quotes” // preserves “”
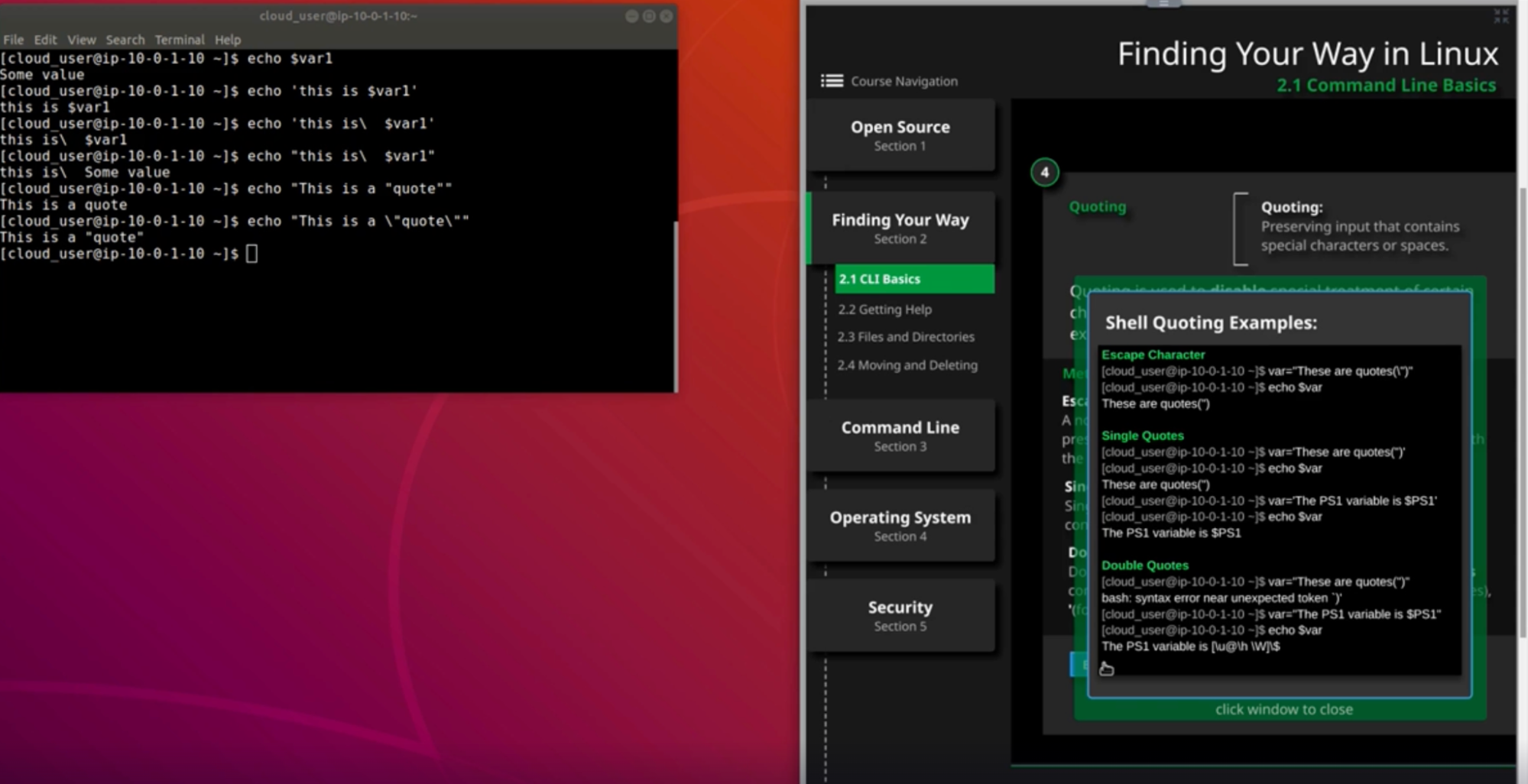
Path environment variable
Example for quoting in Bash
- This is ‘just’ a “text”
- Echo “This is ‘just’ a \”test\”” // escape “” by putting \ in front of “
- this is a backslash "\" and this is a single quote'
- Echo “this is a backslash \”\\\” and this is a single quote'” // escape “ and \ by putting \ in front of “ and \
- 3 double quotes “””, and 3 single quotes ‘’’, and three backslashes \\\
- Echo “3 double quotes \“\”\”, and 3 single quotes ‘’’, and three backslashes \\\\\\\\\”
- Escape “ by putting \ in front of “
- Escape \ by putting \\ in front of \
- Because if you put \ → that will be \\ for each \ → \\ return single \\ → therefor add \\ in front of \
In a nutshell if you want to use \ just the way it is; use \\ for escapting it
- This is a newline character \n, it will create a new line
- Echo “This is a newline character \\\n, it will create a new line”
Man & Info command for Help
To get more info about command use Man and Info command
Ex:
- man ls
- /lines // to search a keyword in the man page use /word
Linux directories and file system
We have a hard drive in our computer
When we install linux OS, it will put a file system on a hard drive and place file on that file system
It will put a file system in a specific hierarchy
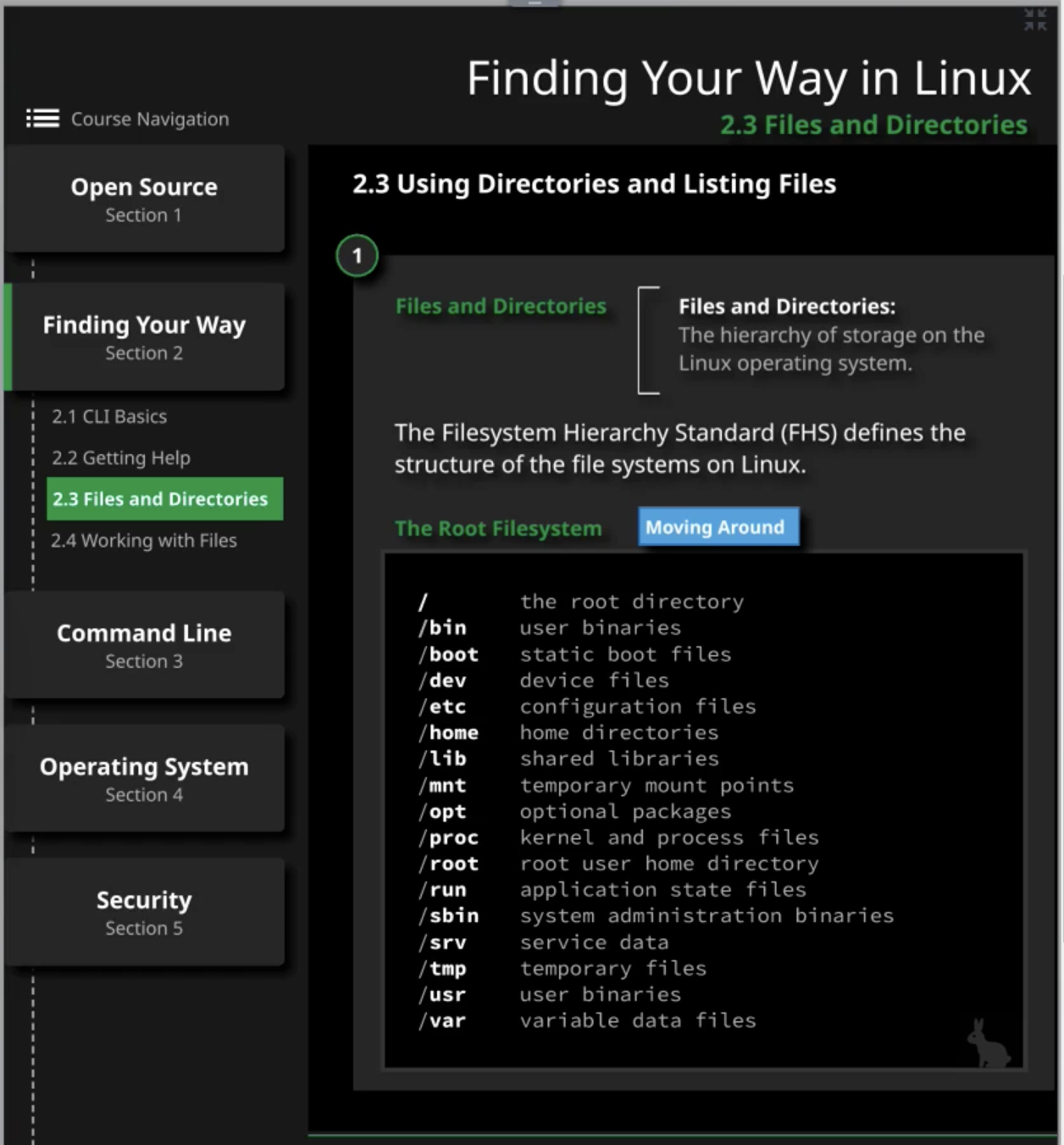
Linux OS
It’s hardware(a physical component used for computing) and a Linux kernel fitted on hardware
Computing hardware
- CPU: processes computer function and performs calculation
- RAM: high performance and volatile storage
- Secondary storage: SSD/HDD/CVD - persistent storage for data not currently in use
- Network interface card: permits connection to a network
- Input device: Mouse/Keyboard - send data into the computer via human interaction
- Output device: monitor - send info from computer to the user
Drivers:
- Drivers needed for application to use hardware
Cron
- Is a daemon that runs in the background and it can execute things on an interval as you like it
Internet, Network and Routers
- In local network, multiple devices are connected with each other via either wire or wireless to communicate and transfer the data/packets
- Switch is carrying data/packets and unable devices to talk with eachother via local network // switches forwards packas on the same network
- Switch is then connected to a router
- Router(Gateway) is then connected to ISP // router forwards packets between networks
Idea
- If you have a server and needs to access to an internet or other networks, it needs to be connected through a router
Command
- Ping -c l google.com or dig www.nike.com
- Step pings is saying like give as a host name google.com
- Next turn that into IP address through DNS query
DNS
- Translate domain name to IP address
It’s going to tell your Name Server that(we asked to perform a query) please translate nike.com into IP address
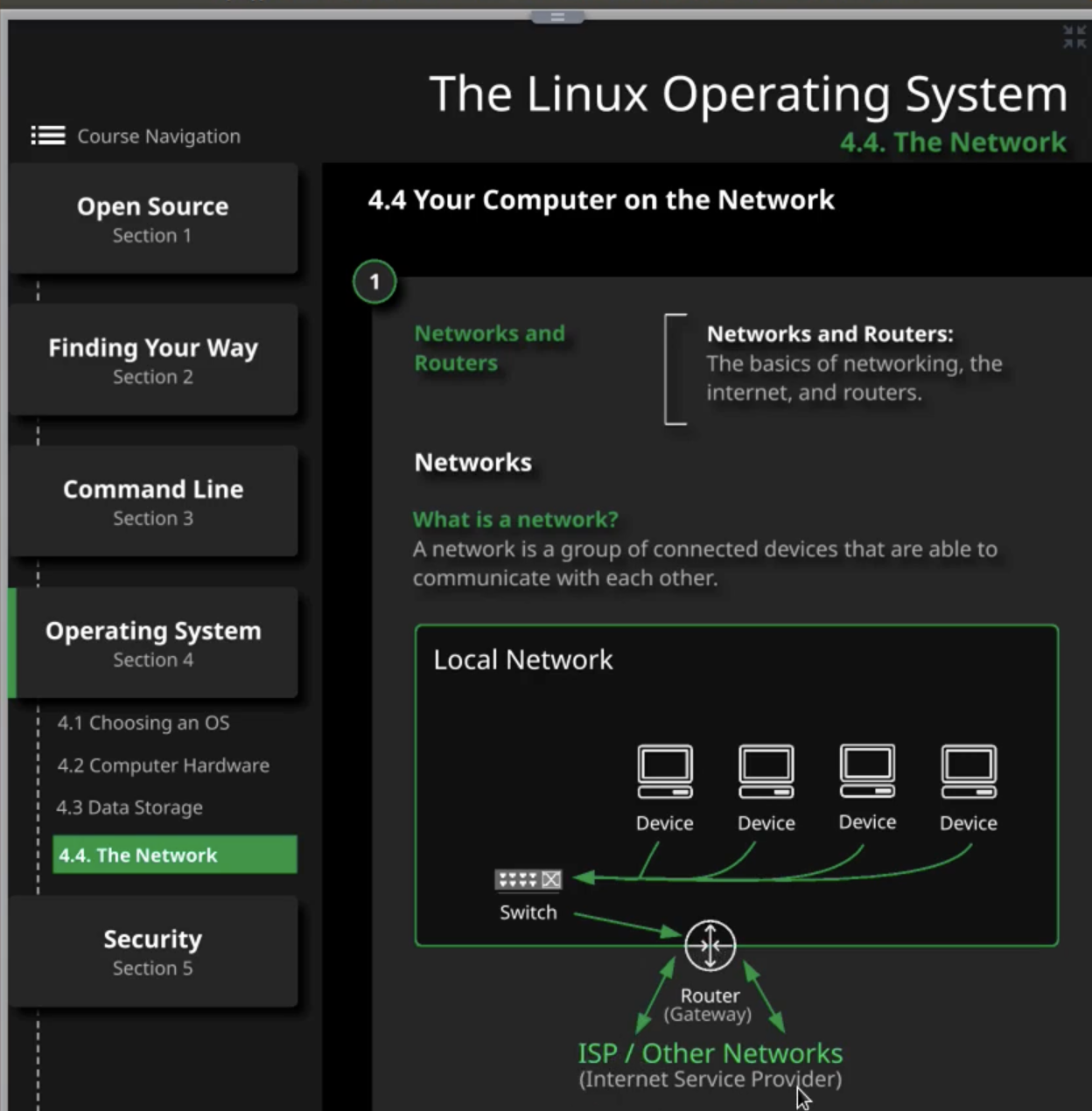
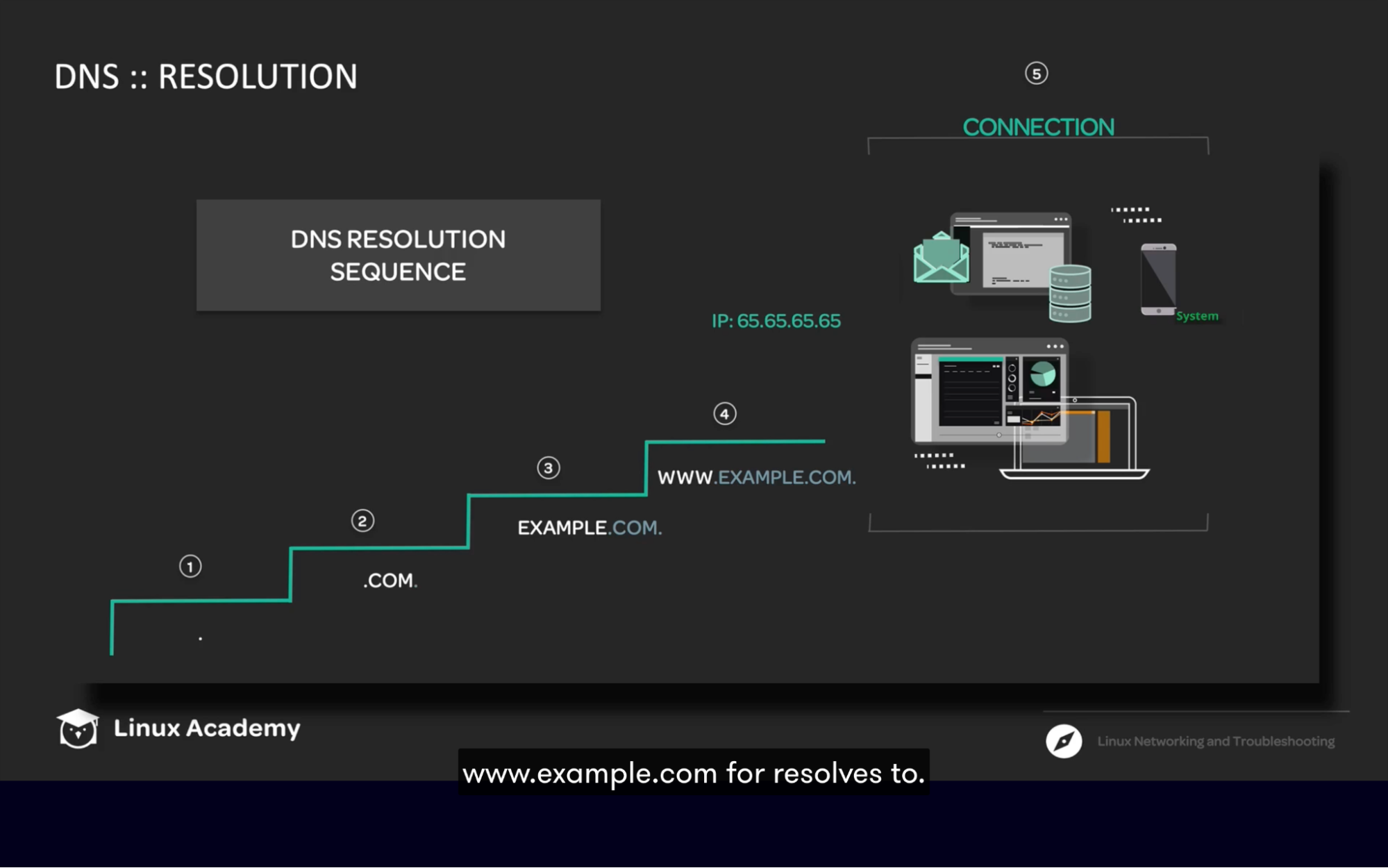
Network configuration
Scenario
- If you are on a local network on some device and want to talk to device in the same network, that request doesn’t has to be go through gateway, you can talk directly through the local network (via switch)
User and Groups
3 types of user
- Root user
- Standard user
- System user(service account)
- Deployed when applications are installed
- Do not have a login shell
Permissions
chown: it lets us change the user & group that owns the file
- You can change the file group by using this command and put it onto another group
- sudo chwon :Group_Name filename
- You can change the file user by using command and assign file to another user
- sudo chwon User_Name filename
- Change ownership of user and group together
- sudo chwon User_Name:Group_Name filename
chmod: let us change the mode read, write & execute across user, groups and everyone
- You can change the file mode from read to execute/write
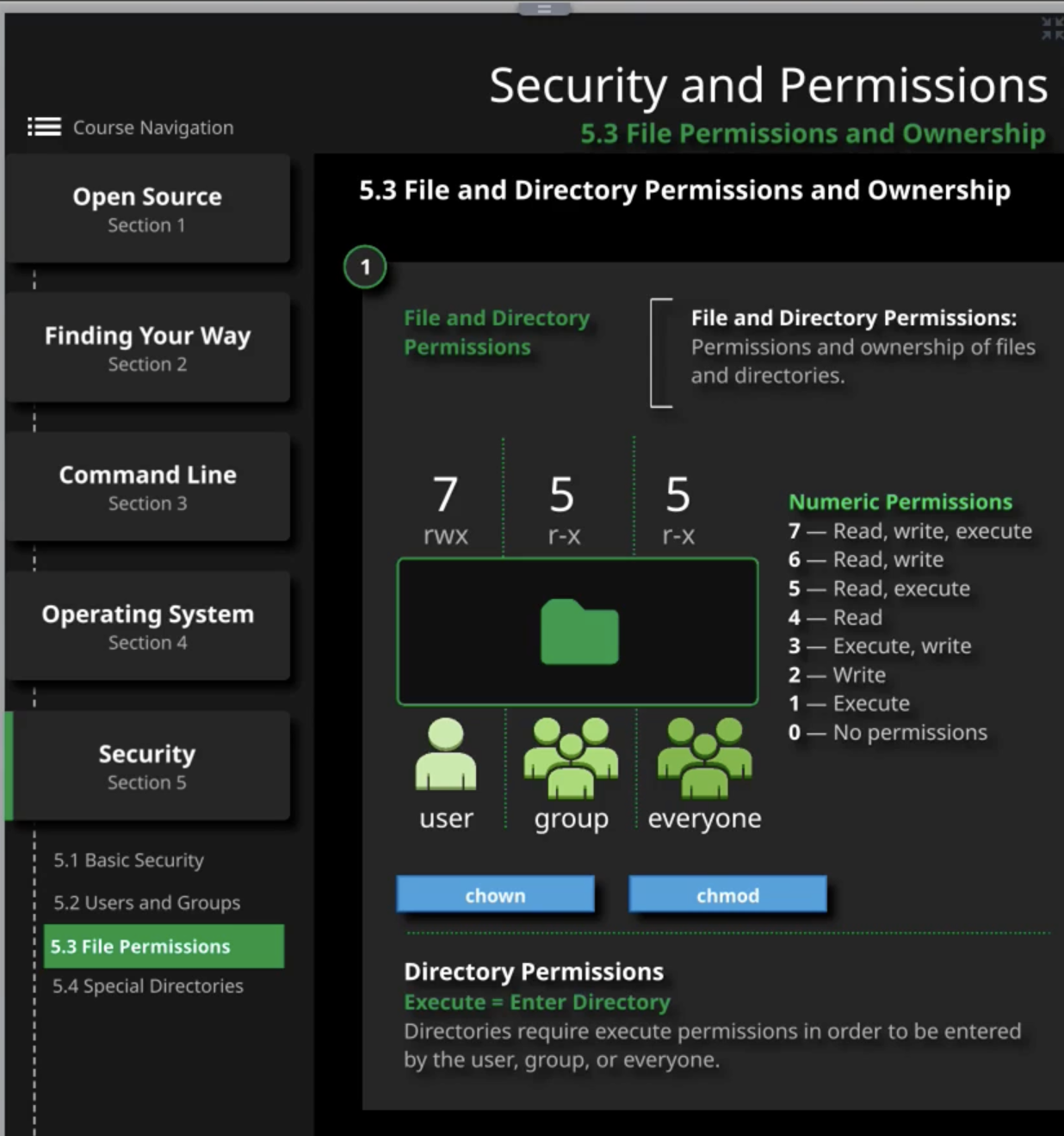
Linux - LFCS
Essential Command
Find/Locate
What: search for files and directories.
How
- Find:
- Search files and directories
- Can search by file name, type, timestamp, and other attribute
- Searching in realtime, so it can be slow on machine
find -name “file.txt” | Will search for a file in a current directory |
find / -name “file.txt” | Will search for a file in root directory |
find /users/hustler -name “file.txt” | Will search for a file in specified directory |
find / -iname “file.txt” | To make search case insensitive |
find / -type f -name “*.log”
type c type d type l type f | Search type of different files
C = find input devices D= directories L = Links F = files |
find /etc -type f -user “hustler” | Find type by users // which user contains what files in the /etc directory |
- locate:
- Faster search then find
- Limited search option; can’t search by attributes or metadata
- Relies on a database for the search, which must be refreshed regularly
locate “file.txt” | Will search for a file and will return file with address |
locate -i “file.txt” | To make search case insensitive |
which/whereis/type
Which
- Returns the location of a command based on the PATH settings,
Whereis
- Returns the location of the binary, source file(s) and man pages
- will return multiole versions of a he it thev exist
Type
- Returns information about the command type.
- Details are based on how command relates to the shell configuration
which python
which nano | Will return the python location
Will return the nano location |
whereis python
whereis python | tr “ ” ‘\n’ | Will return the python location with more details Print all entry in a new line tr = transmit into new line |
type python | Where is python located = same as which |
File Systems
Block device: media used to store data(SSD, Hard disk, floppy disk)
File system: method of allowing OS to interact with data on a block device
- It sits on top of the block device and where actual computer system and information resides
FS with journaling
What: it helps prevent data loss and file corruption when you lose power.
- You have your OS that writes data into your disk
- If power went down on your machine, the system would have no idea whether the file was properly written to the drive or what state the data's in.
How
- With journaling, when you start to write a file, the operating system will note that the file is being written to disk.
- Once the file has been written, the operating system will remove the entry from the journal.
- with journaling, when the computer comes back online, Linux would check the journal and resume any partially completed jobs.
Type of file systems
- EXT1/2/3: extended file system created for Linux in 1992
- Ext4: increased filesytem size, journal checksum
- BTRFS: BetterFS or ButterFS created by oracle in 2007
- Includes FS expansion and reduction
- Replacement of EXT2/3/4
- ReiserFS
- Founded in 2001
- Dev killed his wife and development stalled
- ZFS: created by sun microsystem for solaris now owned by oracle
- Supports drive pooling, FS snapshots, FS stripping
- Each file has a checksum, making it easy to tell if the file has been corrupted
- XFS
- Can be extended dynamically on the fly. However it can’t be reduced dynamically
- FS has to be unmounted before you reduce its size
- Handles large file well
- JFS
- SWAP: this is not a file system
- Used to format a drive, but not technically a filesystem.
- Used for virtual memory (memory swapping) and doesn't have a viewable structure
- Temporary place for items in memory to be stored in low RAM situations
- FAT/32/exFAT
Manipulate File Content
cat file.txt | Print the file content |
cat file.txt | more/less/sort | Cat with More: advance the output one screen at a time Less: advance the output one screen at a time; - scroll up-down one line at a time,
- can find keyword from the text(by /type keyword),
- monitor file in a real time(monitor log file at the time of being written) // sudo less +F var/log/syslog
|
cat file.txt | sort
sort -r file.txt | Sort file content alphabetically // will not modify file content Sort file in reverse oerder |
sort file.txt > file.txt | Write output to the file |
touch file.txt | Create a new file |
nano file.txt | Create and open a new file |
diff file1.txt file2.txt
diff -c file1.txt file2.txt | View difference between file content C = change A = add D = delete -c = context // will give more output on the file content to review |
dif ../shopping ../data/shopping | To perform directory comparison It performed file comparison in one directory to matching files in the second directory and generate report on differences |
comm file1.txt file2.txt | Compare two sored files line by line Output will be in 3 colmuln |
cmp file1.txt file2.txt | Compares 2 files, byte by byte, returns the position of first difference |
Redirection operators
- If we want to save the output of a command, or manipulate the output for immediate review, what should we do? Let's look at what redirection offers.
stdin (0) - standard input
stdout (1) - standard output
Stderr (2) - standard error | How data is entered or presented for processing Typically the keyboard or mouse, but could also be a file The data returned from a command
Error messages that are returned, kept separate from stdout |
pipe Ex: cat file.txt | sort | head -10
| Output of the cat will be sent to sort and that will forwarded to head // displays first 10 lines |
> (create/overwrite) | Used to write command output to the file will create a file if it doesn't exist, or will overwrite an existing file: |
>> (create/append) | Used to append command output to a file will create a file if it doesn't exist, or add output to an existing file |
< (input)
Ex: less < file.txt | Used to direct the contents of a file to a command Often used to send data to a script for processing but works with commands too:
|
Regular Expression - Regex
What: A regular expression, often referred to as regex or regexp, is a specific series of characters which are used to define a search pattern.
Why: A regex is most often used for "find all" or "find and replace" activity. It is also used when you only know part of a search string, or if you are using a wildcard search.
Regex basic
^ | The start of a string or line |
$ | The end of a string or line |
. | Wildcard which can match any character, except newline (\n) |
| | Matches a specific character or group of characters on either side (e.g. alb corresponds to a or b) |
\ | Used to escape a special character |
t | The character "t" |
az | The string "az" |
Regex Examples
grep ‘^The’ file.txt
grep ‘^T[a-z]^e’ file.txt grep ‘^T[a-z][^e]’ file.txt
grep ‘\<[tT]he\>’ file.txt | Print line that starts with “The”
Print line that starts with “T”, followed by a lower case from a to z, and does not end with “e”
Return every The in the file, doesn’t matter the letter(can be uppercase or lowercase) |
grep -E -o "\b[A-Za-z0-9._%+-]+@[A-Za-zo-9.-]+\[A-Za-z]{2,6} \b" file.tx | print out email address in the file |
Archive/Backup/Compress/Decompress
sudo tar cvf mybackup.tar DirPath
sudo tar cvf mybackup.tar /home/work/toarhive | backup files; FilePath should be full path c=create v=verbose f=file - This tar will have same amount of space those files contains.
|
sudo tar cvfz mybackup.tar.gz DirPath | Compress files z=zip - This will be smaller in size
|
Tar tf archive.tar | Look through/List files in the archive.tar |
Tar xvf archive.tar file3 Tar xvf archive.tar // extract everything | Extract specific file from the archive.tar |
touch file.txt nano file.txt ls -lhF > file.txt | Create a file. Create and open file Create a file. |
- cp -v demo(file) folder(folderName)
- cp demo demo2
- cp demo demo2 demo3 folder(folderName)
- cp -i demo folder(folderName)
- cp -iv demo folder
- cp -iv demo ..
| - Copy the file into the given directory/folder at last. -v stands for verbose, it prints copied file into mentioned folder on the command line
- Copy the the existing file(demo) and give a new name at last of copied file // rename and create a new file
- Copy multiple files inside folder name you provide at last
- If you copy an existing file inside a foldr, -i will ask you to overwrite the file. -i stands for interactive option
- Use multiple option together (overwrite & verbose)
- Copy file to previous directory
|
mv -v play/demo.txt . | Moves the file from play folder into current directory |
mv demo NewName.txt | Rename file from demo to NewName.txt |
- rm -v demo
- rm -v -r folder
- rm -i demo
| - Remove file // remove means it is deleted forever, can’t find in the trash
- Remove folder
- Remove with interactive mode
|
Hard/Soft Links
Task: As an admin, how can you handle the need for a file to be accessible in two places at the same time? Let's look at hard and soft links as an option.
Hard Link
- Direct pointer to file
- Can only be a file
- Shares the same inode as source
- Must be on the same filesystem
- As long as hard link exists, the data exists
Soft Link (Symbolic Link)
- A redirect to file (think shortcut or alias)
- Can be a file or directory
- Has a unique inode
- Can be on a different filesystem or mounted share
- If the source file is deleted, the soft link is broken
ln info.txt infohardlink | Create a hard link - This will create a hardlink file(which is copy of the info.txt file)
- ls -li = hardlink shares same inode value as source file
- So if you update hardlink file, it will automatically update the source file
- If you delete source file, you will still has HL file
|
ln -s info.txt infosoftlink | Create a soft link |
File Permissions
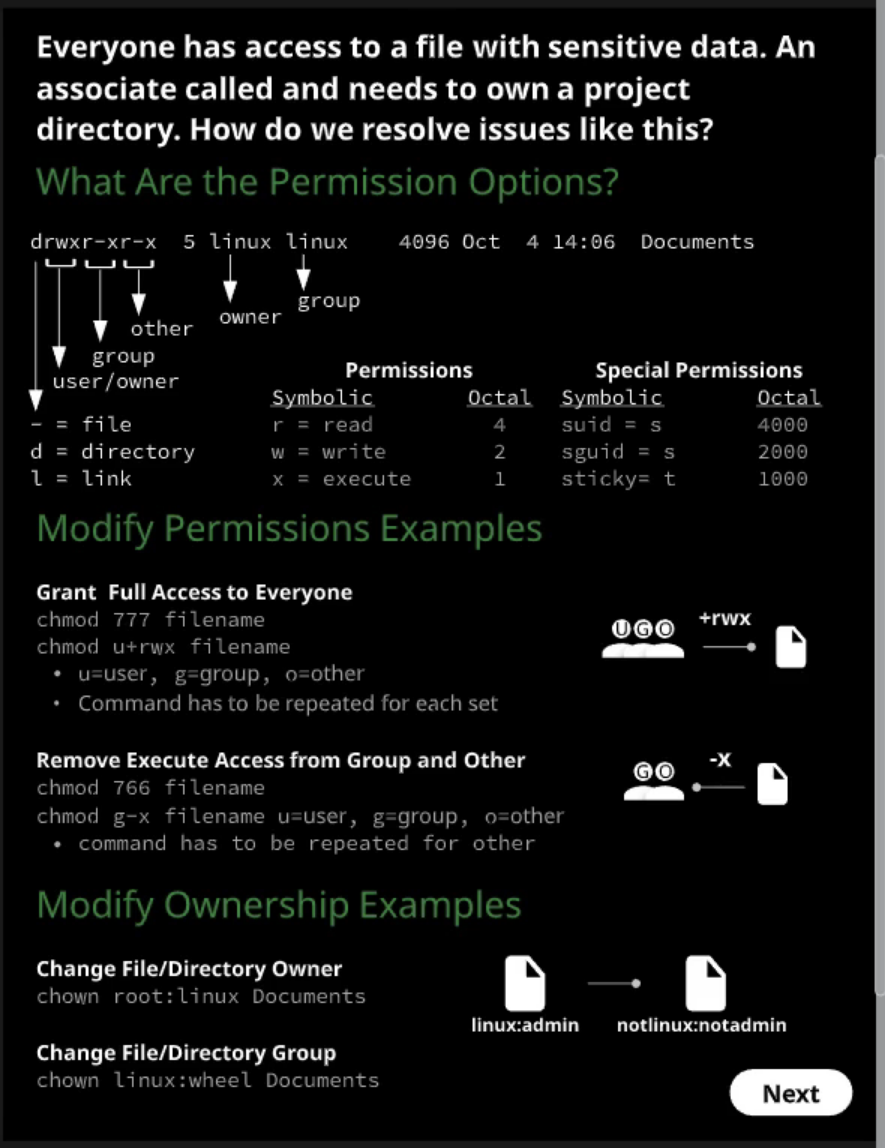
Manage access to the root account
Task: The root account has access to manage and modify the entire system. To secure and protect the system, how to we restrict access to root?
Why not root?
- The root account has the most access of any account on a Linux system.
- Most modern Linux systems do not allow you to log in or change over to root.
- root access is not necessary for most daily tasks.
How to avoid root
- Always log in as yourself or another non-privileged account!
- sudo - superuser do
- Grants temporary elevated privileges to run a command
- Su
- Substitute user
- Changes to the root account until logout
How to manage sudo access
- Access is granted via entries in the /etc/sudoers file
- Access can be managed by account or by group
Taks
- Add a new user into /etc/sudoers
- Add a user to the existing group in the /etc/sudoers → sudo gpasswd -a username groupname
- To open /etc/sudoers file use “sudo visudo”
- Delete a user from group in /etc/sudoers → sudo gpasswd -d username groupname
sudo -i | Login as a root user |
su UserName | Switch to different user |
Tasks
Backup App via archive by Tar
What: Team wants to take a full backup of the custom application in the /opt/myapp/ directory. back will need to be compressed. We need to create a file called myapp.tar.gz in the /home/cloud_user/archive directory.
mkdir archive
cd archive
# Archive the /opt/myapp Directory as myapp.tar.gz
tar -czvf myapp.tar.gz /opt/myapp
# List the Contents of myapp.tar.gz and Redirect It to app.list
tar -tf myapp.tar.gz
# redirect the output to an app.list file:
tar -tf myapp.tar.gz > app.list |
Add/Change execute permission to files and view/change attribute
Task: Correct the permissions and attributes of /opt/myapp/start.sh on the system, so the custom application located under /opt/myapp has the permission to execute. In order to prevent problems with this program, /opt/myapp/start.sh, we are also asked to set the attribute of the file, so that the file cannot be altered or removed accidentally.
# View the Current Permissions of /opt/myapp/start.sh
cd /opt/myapp
ls -l start.sh
stat start.sh
# Change Permissions on /opt/myapp/start.sh to Allow Full Privileges for User and Group Only
chmod u=rwx,g+wx,o-r start.sh
chmod 770 start.sh
# Verify That /opt/myapp/start.sh Is Executable
stat start.sh
./start.sh
# Make the /opt/myapp/start.sh Immutable Using a File Attribute
lsattr start.sh
sudo chattr +i start.sh
lsattr start.sh |
Finding Files, and Assigning Permissions and Ownership
Task: We need to give any members of the DevOps group write access to /opt/myapp, so that they can work on the application. We also need to give the user cloud_user ownership of the directory. DevOps members and cloud_user need to be able to execute the application, start.sh as well. Finally, we need to make sure that anyone who is not cloud_user or in the DevOps group has absolutely no access to /opt/myapp whatsoever.
# Find Custom Application Files under /opt/myapp and Display a Detailed
find /opt
find /opt/myapp -ls
# Change the /opt/myapp Directory to be Owned by the cloud_user and the Group devop
find /opt/myapp -exec sudo chown cloud_user:devop {} \;
# Set Permissions for /opt/myapp Files
find /opt/myapp -name "d*" -ok chmod 660 {} \;
# Next we'll change permissions on anything that does not start with d (the directory itself and the start.sh script). We're going to also prompt ourselves to confirm each change with the -ok switch:
find /opt/myapp '!' -name "d*" -ok chmod 770 {} \;
# Find a Directory under /home Which Is Not Owned by a User or Group
find /home -nouser -nogroup -ls
# Execute the chown Command with the find Command
find /home -ls
find /home -nouser -a -nogroup -ls
find /home -nouser -nogroup -exec sudo chown cloud_user:cloud_user {} \; |
Transfer Files Securely Over the Network
Tasks:
# Push copy of directory from server to server
scp -rp /opt/myapp root@server2:/opt
# Pull copy of directory from server to server
scp -rp root@server:/opt/myapp /opt
# Push copy of directory from server1 to server
rsync -aP /opt/myapi server2:/opt
# Pull copy of directory from server to server1
rsync -aP server2:/opt/myapi /opt |
Operation of Running Systems
Boot, Reboot, and Shut Down a System Safely
What: A Linux machine requires maintenance for hardware and OS updates. How should you shut down or reboot the machine?
- shutdown: This is the go-to command for shutting down, powering off, or rebooting a machine. It works on system 5 and system-based operating systems
- Shutdown -r <TIME>: Reboots the server at the time specified.
- shutdown -H <TIME>: Halts all CPU activities at the time specifier
- Shutdown: -P <TIME>: Shuts down the OS and sends a command to power off the machine at the time specified
- Reboot: It performs the same function as shutdown -r, but can also be used to halt or power off the server when the correct parameters are sent.
- Halt: This performs the same function as shutdown -H. And can also be used to reboot or power off the server when the correct parameters are sent
- Poweroff: It performs the same function as shutdown -P, and can also be used to reboot or halt the server when the correct parameters are sent
Linux Server Troubleshooting Guide
Methods
- USE: Utilization - Saturation - Error
- KAVBG: Knowledge - Ask Question - Visualize - Break it to replace it - Google
Commands
Load and CPU Usage
Load: uptime
- Find the amount of load on the system
- Load average should always be equated to the number of CPU cores. If the ratio of load average to the number of cores > 1, then the system is under load and requires attention.
CPU Usage: top/ps
- provides load averages, CPUs, and their percentage utilization breakup in terms of usage with respect to user processes, system processes (executing kernel code), waiting for IO operations to complete, interrupt handling, and CPU time stolen from a virtual machine
Java Thread dumps: jstack
- Thread dumps contain a great amount of information about the current state of the application.
- These can be extremely useful in ascertaining a range of possible issues such as high CPU consumption, thread deadlocks, application slowdown, etc.
uptime | Know whether our system is overloaded - to find the load average values for the last 1, 5, and 15 minutes
|
cat /proc/cpuinfo | grep processor | wc -l | To know the number of cores we can use /proc file system: |
top | provides load averages, CPUs, and their percentage utilization |
ps | To know the process ID of our Java process - will list process IDs of those Java processes for which the tool has access permissions.
|
jstack | prints the stack traces of all threads that are attached to the JVM. These include application threads, VM internal threads, and optionally native stack frames. Using jstack, it is also possible to force (using –F flag) a thread dump of a hung process or when its output has been redirected such that the dumps are not available through kill –QUIT command |
Scenarios
Task: To understand that our application is suffering from high CPU usage
- Top: note whether CPU is constantly above 85-90% CPU utilization or not. we need to isolate the root cause(s).
- Initiate a few thread dumps: In thread dumps, we are only interested in those threads which are keeping the CPU busy - threads which are in RUNNABLE state.
- Once we have isolated those threads in thread dump, we can analyze their stack dumps and focus on those code paths.
- how: top or ps
- Inspect the threat dump status
- we focus only on those whose state shows up as ‘R’
- notice threads which consumes high CPU%
To, summarize, we took thread dumps and made a note of RUNNABLE threads. In parallel, we
also took output from ps command. We filtered out a great number of RUNNABLE threads from
thread dump for our analysis because we were able to find those threads which are consuming
maximum CPU.
Kernel Buffer Commands
free -m | Check RAM |
top | See running processes |
dmesg dmesg | less dmesg -T | Check kernel message if it’s printing any logs |
Virtual Memory Commands
vmstate | How many resources are in queue, buffer size, swap, free memory and more |
PID Status Commands
ps | How many resources are in queue, buffer size, swap, free memory and more |
