Links 3
Networking 3
Why do we need a network? 3
After Network 3
Led to the modern Internet 3
Caveat 3
Subnet for a solution 3
How subnet can be configured - Protocols 3
OSI Model 3
1. Application 3
2. Presentation 4
3. Session 4
4. Transport 4
5. Network 4
6. Datalink 5
7. Physical 5
IP 6
IP Address 6
TASK 7
Task: convert ip address from binary to decimal(whole number) 8
Public vs Private IP 8
TASK 8
Subnet Mask 9
Network IP/Subnet Mask 9
Network 9
Type of network 10
Subnet 10
Router 10
How to subnet 10
IP Classes 10
7 Steps to subnetting 11
Ways for subnetting 11
Easy way: 6th step excluded 11
Hard way: 6 steps 11
Example 11
Easy way 11
Hard way 12
Azure Networking Concepts 13
Networking Basics 13
Scenarios 13
Architecting VNets 14
Basic Understanding 14
TODO 14
Terminologies 14
Common Questions 14
Architect Components 15
Flow 15
Delivery 16
DNS 16
Azure Traffic Manager 17
Azure Front Door 18
Content Delivery Network 18
Security 19
Network Security Group - NSG 19
Application Security Group - ASG 20
Load Balancer 20
Application Gateway 20
Firewall 21
Connectivity 23
Routing 23
Service Endpoint 24
Private Endpoint 25
VNet peering 25
VPN & VPN Gateway 26
Types 26
2 types of Gateways 27
Architecture 29
Steps 30
Express Route 31
Virtual WAN 32
VNet Strategy 33
VNet/Subnet Strategy 33
Security Strategy 33
Performance Strategy 34
CALLOUTS 34
Architecting VPC in AWS 35
Links
Networking
Why do we need a network?
- Before the internet, computers were isolated; they couldn’t talk to each other, send data.
After Network
- People begin to network their computers together to share data like files, emails, games to computers that were in the same network
Led to the modern Internet
- Part of networking computers together is being able to identify a computer on the network with an address of some sort; so you can connect to it and send data back and forth. Like a mailing address identifies the house, a Network address identifies the computer
Caveat
- It does not necessary for every computer on the internet has to have an address
- You don’t want every computer to be directly accessible from every other computer over the internet
- You still want to get those files and data on your computer
Subnet for a solution
- Computers on a subnet may be able to talk to each other; but they are also shared connections that are a large part of the internet
How subnet can be configured - Protocols
- For the above to work, you need protocols and standards to define how networks work.
- These protocols work in layers, where one set of protocols and standards defines how a given layer works for a given network
- A common model is OSI Model
OSI Model
https://www.imperva.com/learn/application-security/osi-model/
Application
What: This is where the data has meaning and is read and interpreted by something
Protocols: HTTP, FTP, DNS
- HTTP Protocol - website works; operates top of the stacks
Presentation
What: The syntax layer
- standardizes communication between the different operating systems, such as do string end in a null or not, is data compressed before being sent over the wire
- Encryption happens at this layer over the SSL and SSH
Session
What: this allows a computer to open a channel with another computer and keeps that channel open for more continuous communication until it’s closed
Example: this type of connection is more common with live streams such as video conferencing well data is sent continuously from server to client(this avoids the overhead of trying to do an open handshake, authentication and close for every piece of data)
Layer: sockets level
Transport
What: add services on top of the network layer. ex:
- same order delivery: this ensures that packets are received in the same order in which they are sent
- this layer also adds reliability by adding acknowledgments to the communication to let other party know that the message was successfully received
- this layer responsible for ports which allows multiple devices to communicate with the same destination at the same time for different purposes
Protocol: TCP and UDP happen at this layer
- TCP protocol: How data gets from one computer to another computer on the internet
Ports: it allows multiple messages to be sent to the same IP address intended for different receivers
- port 80: web server (connecting to encrypted websites)
- port 443: webserver(unencrypted website)
- port 1433: SQL server
- port 22: SSH server
Network
What: this layer includes the message forwarding feature of networks where data packets are not intended for the device is directly connected to the network, but are to be passed on to the next network in the chain - a fundamental element that makes Internet resilient(withstand and recover quickly)
IP: the concept of IP addresses we can separate them into the network and host parts. This is where we understand how to route a message intended to that address.
Protocol: IP, ICMP, and IPSEC happen at this layer
- IP protocol: How data gets from one computer to another computer on the internet
- How to identify a specific computer in a network with
- IP Address
- Routing
- Subnet
Datalink
https://www.youtube.com/watch?v=pi7mMjiixiY
What:
- establishes and terminates a connection between two physical devices on a network
- does basic error control, ensuring collisions don’t happen over the wire where two devices on the same network. Try talking at the same time.
Why
- In a network scenario, network layer packets don’t have a way to get across a physical medium
- The role of this layer is to formate these (network layer)data packets into frames and send them out over the network
- Frame → header + data packets + trailer
How
- For example, ethernet frame are given header and trailer to create a protocol data unit(PDU)
- Data packet can be taken out from network layer and fit it with header and trailer to transmitted across physical layer → capsulation
Type/Part
- Logical Link Control (LLC): identifies network protocols, performs error checking and synchronizes frames,
- Media Access Control (MAC) which uses MAC
Physical
What:
- Contains networking hardware; the remaining layer can be implemented as a software layer on top of that hardware layer
- Provides a basic communication channel that 2 network devices can use to send and receive data
- transmitting raw bits(rather than logical data packets) between physical machine on the network
How:
- It’s job is to take steam of bits(digital signal) from one device → encode them into a physical signal(analog signal) → send them over a wire over a radio → and then decode those bits from the physical signal in order to extract the steam of bits from the signal
- Most common type of Analog signal is an Electromagnetic wave: travel with the speed of light through other materials
- Type of Electromagnetic wave
- Electrical pulses over the wire
- Radio signals through the air
- Pulses of light through fiber optical cables
- Other type of analog signals are // data transfer is slow on this signal, hence we typically don’t use it
- Sound
- Vibration
- Pneumatic
- The bit stream may be grouped into code words or symbols and converted to a physical signal that is transmitted over a hardware transmission medium.
- The physical layer provides an electrical, mechanical, and procedural interface to the transmission medium
- Hardware on this layer: repeater, hub, plug, cables
IP
IP Address
IPV4
5 classes - A, B, C, D, E
Class A, B, C is for
- Public: public website
- Private: corporate or home network
Class D is for multicasting
- Conference call
- People on a call from a different location at the same time
Class E is for Government or research
IP Address
- It consists of 32 bits
- 4 octets (4-8-bit)
Phone Number
(647) 765 - 5678
647 = area code
- Everyone from Toronto area has the same area code
Rest Digits = Phone number
- Digits after the area code is a unique number assigned to a user
IP address
EX: 198.168.0.0
127.0.0.1 =used to talk to yourself = localhost
- Used for troubleshooting and testing
IP Address consist
- Network part (area code)
- Represents where you at
- Node or Host part (Phone number)
- Represent you located on that network
TASK
- Determine what class an IP belongs to
- Determine other numbers that come between 0 to 255
Class A | 1/126 = 1st Octact = Network ID | Last 3 octacts = Node/Host ID |
Class B | 128/191 = 1st & 2nd Octact = Network ID | Last 2 octacts = Node/Host ID |
Class C | 192/223 = 1st, 2nd & 3rd Octact = Network ID | Last 1 octacts = Node/Host ID |
Task: convert ip address from binary to decimal(whole number)
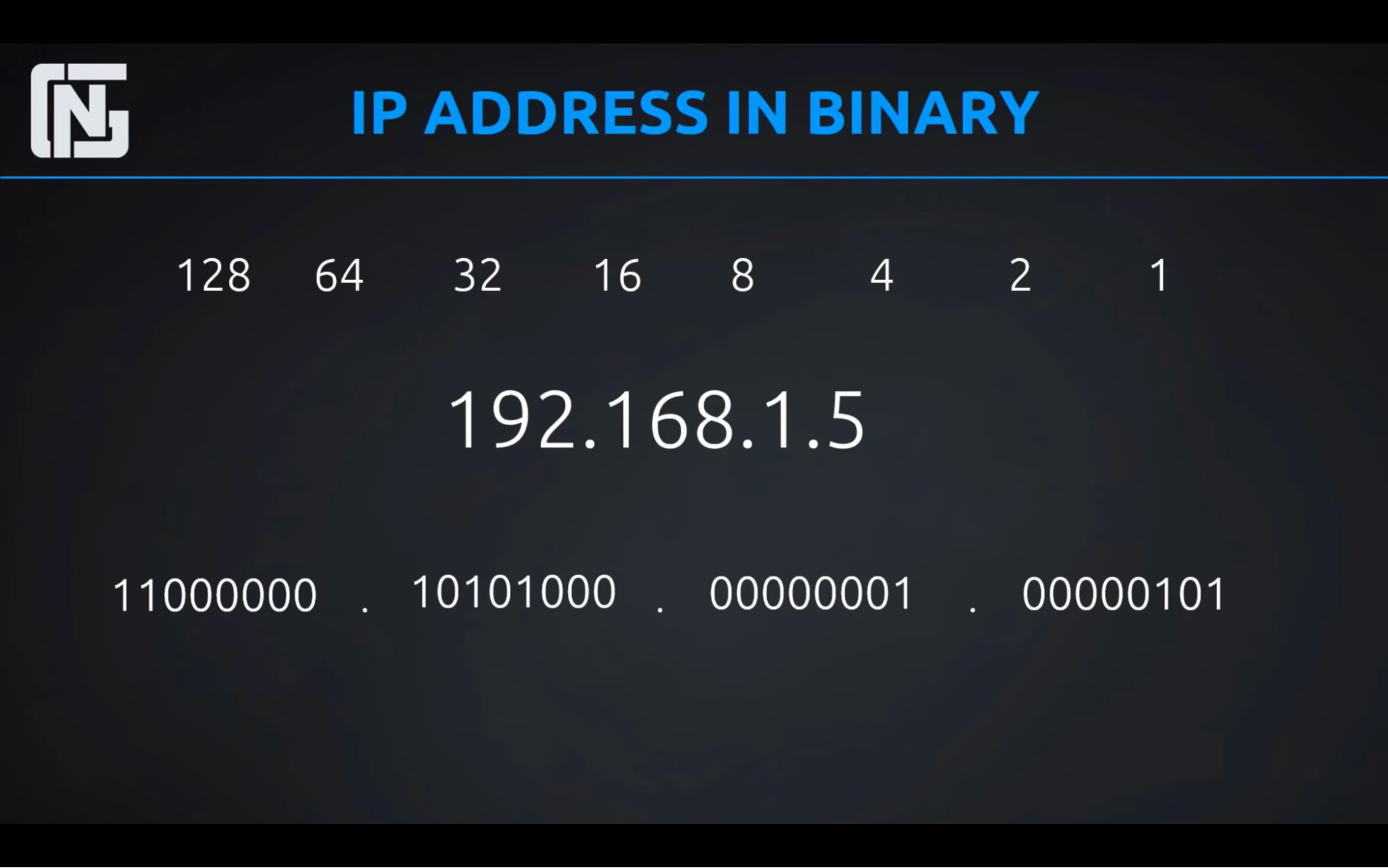
Public vs Private IP
We as an individual were never meant to be on the internet.
IP address was designed to be for Government, Schools, and Businesses and not for individual
After 1920 Internet was created and opened to the public
And we as an individual were able to get on the internet
IP address has to be unique and since we open to the public we were running out of the IP Addresses
To avoid this, we set aside some numbers as a private number
- Network admins can use this number any way they see fit and use it however they want
- Tradoff is these private IP can’t use on the internet to extend the use of IP address by being able to use a private IP address within our home/business and then translate those into a public IP address when you try to get on the internet
- This is how a network works
TASK
What IP addresses have been set aside for private use?
Class A | 10.0.0.0 - 10.255.255.255 = private address | Last 3 octacts = Node/Host ID |
Class B | 172.16.0.0 - 172.31.255.255 = private address | Last 2 octacts = Node/Host ID |
Class C | 192.168.0.0 - 192.168.255.255 = private address | Last 1 octacts = Node/Host ID |
Subnet Mask
- Is to tell you what part of the IP address is network part and what part is node/host part
- Wherever you see 255, the number above that is part of the network(see the below table below to understand this)
- IP address and subnet mask must go together (they work in pair)
- If you don’t provide subnet mask you can’t tell about IP address
IP address | 192.168.1.1 |
Subnet mask | 255.255.255.0 |
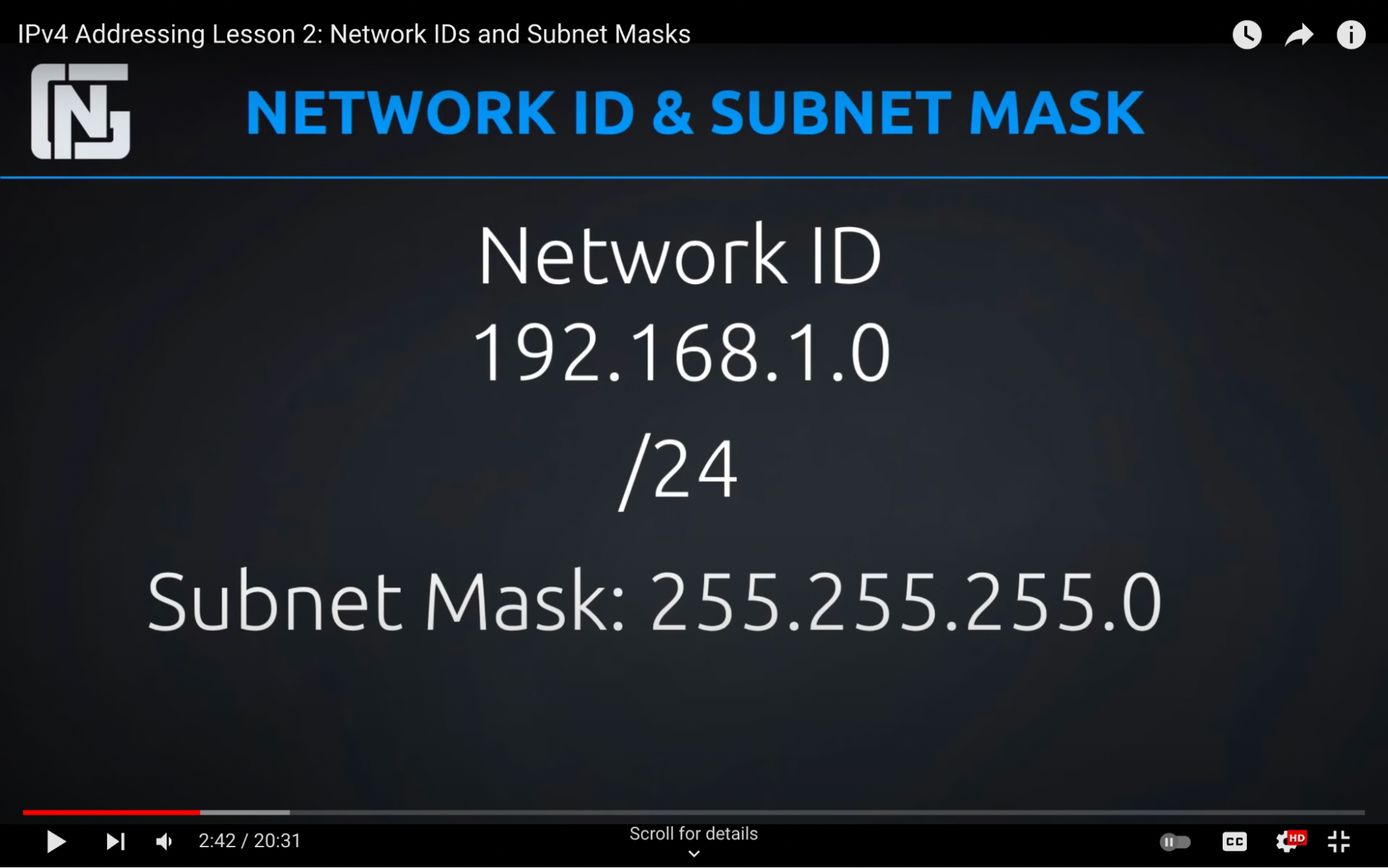
Network IP/Subnet Mask
Network id = 192.168.1.0
Subnet mask = /24 = refers to the number of bits in the subnet mask
Network
Network connects the devices(nodes)
Devices share information
To share info, they must speak the same language
This language is called protocol
Protocol: protocols are a way to format data.
Network
- You have your organization in one network
- You store entire organization data in the network
Type of network
- LAN - devices in Local Area Network
- SOHO: small office work office
- Contains devices —> switch —> router —> internet
- Everything is inside 1 device
- WAN - Wide area network, offices in different countries
- Enterprise Network
Subnet
- You divide your network into smaller pieces
- Why?
- Security: to secure data so that nobody can access your data within your network
- Organization: organizing your divisions by separating them into smaller pieces // HR, IT, Admin
- Performance // because it’s a smaller
Router
- Connects different network together and allow to talk to one another (share data across)
- It takes different network id’s and allows them to connect together
- Network admins can control router; control all access from one network to another
- If you don’t want HR network to access to IT they won’t by blocking it
- Single point of administration
- Every people on a network must go through the router to go to another location \\
How to subnet
Idea is to subnetting your network by identifying how many networks do you want
IP Classes
Class | Range | Used for |
Class A: | 10.0.0.0 to 10.255.255.255 | Private IP address |
Class B: | 172.16.0.0 to 172.31.255.255 | Private IP address |
Class C: | 192.168.0.0 to 192.168.255.255 | Private IP address |
7 Steps to subnetting
- Identify the class - A,B,C
- Identify network and node Id
- Apply default subnet mask
- For class A place 255 for network ID, rest is 0 = 255.0.0.
- For class B repeat the above process = 255.255.0.0
- For class C repeat = 255.255.255.0
- Convert subnet mast to binary
- Use 2n-2 to determine custom subnet mask
- Your subnet mask will start with binary 1’s, and it must be continuous until they stopped
- Determine LSB(least significant bit)-IT, Gives you 1st subnet and range
Ways for subnetting
Easy way: 6th step excluded
- Has a CIDR Notation. Ex: 172.16.0.0/20
- /20 tells you how many 1’s are in your custom subnet mask
- The number, at last, is your custom subnet mask
- It represents how many binary 1’s you are going to have in your subnet mask
- TCP/IP Rule:
- Your subnet mask will start with binary 1’s, and it must be continuous until they stopped
- So in our example 1st 20 of the bits are binary 1’s and last 12 will be 0’s (because IP Has 32 bits)
Hard way: 6 steps
Example
Easy way
Example: 172.16.0.0/20
11111111. 11111111. 11110000. 00000000 // because 1st 20 are 1’s
Convert into decimal
255.255.240.0
Example -2 Easy way
178.31.0.0/24
11111111. 11111111. 11111111. 00000000
Convert into decimal
255.255.255.0
Network portion = 24(255,255,255=8+8+8)
Host portion = 8 (32-24) = 256 IP address
Take away
- Higher the CIDR notation/subnet number is, the less IP address you can have
Hard way
TASK: 11 networks is needed
Example: 172.16.0.0
- Class B
- 172.16 | 0.0. // identify network and node Id
- 255.255.0.0 // Apply default subnet mask
- 11111111. 11111111. 00000000. 00000000 // Convert subnet mast to binary
Question is we need 11 network
Rule: 2n-2 >= 11
n = 4, 16-2 = 14 >=11 // you’ll get 3 more networks to play with
Take n = 4 and place it in your host node where all the 1’s stays continues (see the rule)
- 11111111. 11111111. 11110000. 00000000
Customize your subnet mask
Convert binary into decimal
11110000 = calculate 1st 1’s into decimal = it’s 240
Converting binaries to decimal = 255.255.240.0
- Determine LSB
Identify
- subnet(make slices)
- Beginning and ending number of the subnet
- Subnet range
In our example 11110000 = least significant number is 16 (128,64,32,16,8,4,2,1 // 11110000)
- The beginning and ending number of the subnet // one piece of the network
172.16.16.0 // least number is 16 // 1st subnet
172.16.31.255 // range of the first subnet
Next subnet
172.16.32.0 // 2nd subnet
172.16.47.255 // range of the first subnet
Azure Networking Concepts
Networking Basics
- With TCP protocol, 2 VMs talks to each other by sending a series of messages called packets containing data over network
- When you try to go to any website, LinkedIn.com, your request in packets goes through different/multiple networks called Hops. And Responses also get back through multiple networks
- You can see your ISP and LinkedIn’s internal network provided a few times if you trace network details
- Connectivity is accomplished by modems, routers, hubs, and optical cables.
Firewall Types
- Network security group - basic
- Web application firewall (WAF)- industry standard
- Application gateway(layer 7 LB) comes with WAF
- The azure front door comes with WAF
- Azure firewall - managed service
Delivery
- Content delivery network
- Azure traffic manager
Monitoring
- Network watcher: attach to your network to help diagnose issues
- ExpressRoute monitor: if you use express route
Scenarios
- NSG: if your local device on the internet wants to communicate to an Azure VM hosted in a private virtual network, then you need to configure explicit rules in your security group to allow that kind of traffic to come in
- VPN: how can you securely connect your office location to the device on Azure Network?
- Point-to-site VPN(computer to Azure network)
- add a single computer/server/your office device into an azure network, so using a VPN, your desktop can act like it’s on Azure private network and have access to resources normally protected behind the firewall
- Site-to-Site VPN(IT office network to Azure network)
- entire office network connected to Azure network
- This requires a physical VPN device - gateway to be installed on your side - to create an encrypted private channel into the Azure network
Architecting VNets
Basic Understanding
TODO
1. Determine IP CIDR
2. Subnetting requirements
3. Connectivity needs
1. What type of connectivity is needed: internet, resources to resources, resources to service
Terminologies
- VNet
- DHCP server
- Subnet
- Network interface card - NIC: IP configuration
- What: Decide/set whether you want public or private connectivity with your resource that is attached to NIC
- Ex: if you want your VM to be accessible via public internet, then you use NIC and associate Public IP in NIC, NIC is attached to VM. that’s how you can connect to your VM through public internet
- Caviet: you will need to attach NSG with NIC to allow inbound traffic
- Network security group - NSG
- Peering
- Network gateway
- AZ spanned
Common Questions
What happens when you create a resource in VNet
- Network interface Card(NIC) gets created/installed with your resources
- What: where you can see all the resources VNet details:
- which subnet it belongs to, what’s it IP address
- Assign static IP - You can also assign a specific IP address to the resources
- By default intra network traffic (private: subnet to subnet inside Vnet) and outbound traffic(communicate to the internet) are allowed
- Private IP: By default, resources created in this VNet/Subnet gets private IP and they are able to communicate with resources with the same Vnet
- Public IP: resources to talk to the internet
- Basic SKU type: accessible by default and require NSG to restrict traffic, no Zonal supper
- Standard SKU: dynamically assigned IP, not accessible by default. require NSG to allow traffic
Architect Components
What happens when you have VNet
- VNet
- Security
- Bastion host
- DDoS protection standard
- Firewall
- Subnetting
- 5 IPs are reserved
- x.x.x.0-3 and x.x.x.255(last octate)
- Private networking: Resources you put inside VNet(ex: VM) gets a private IP address.
- How: served out from DHCP server, which is built in to VNet
- Public networking: VNet supports public IP addressing(IPV4 IPV6) so that resources can have public connectivity
- Say explicitly whether you want to assign a Public IP to your resource
- Peering: the connection between VNet to VNet
- Peering in the same region and global region
- Network gateway(device): Azure VNet uses Network gateway(device) in gateway subnets to make VPN connection
- Monitoring: view logs of VNet to see where resources are in VNet
- Security: through firewall
- NSG at Subnet and NIC level
- Firewall
- Web application firewall with application gateway(layer 7 LB)
- Azure front door
- Managed firewall
Flow
- Create Vnet with multiple subnets (depending upon your application component)
- Ex: Web server subnet, App server subnet, DB server, backup server
- Each subnet has its own NSG - security settings
- Create/Place resources in a subnet.
- Each resource you put into the subnet will get private IP within that subnet CIDR range
- How: resources are added to the subnet through NIC(installed in them)
- Resources can have multiple NICs to connect multiple subnets at the same time
- NIC also supports NSG - acting as a firewall(same as subnet NSG) - so you get 2 layers of NSG (1 at subnet and 1 as NIC)
- 2 NSG at both of these layers is not recommended because of complexity and troubleshooting reasons
- NSG: the starting point of security. Use advanced features along with NSG
- When you create VNet with a subnet, NSG has 3 default inbound traffic rules
- AllowVnetInBound: traffic between computers running on the same network or connected networks is allowed: Vnet peering and VPN traffic
- AllowAzureLoadBalancerInBound: This is traffic from the load balancer. For example, from health probe is allowed
- DenyAllInBound: all other traffic is denied
- rules are evaluated in order. From the lowest priority number to the highest. The first rule to match the traffic is the rule that wins
- create custom rules with high priority to override the default rule effectively. because the default rule can’t be removed but rather overridden
- rule example: Port80, 443, 3389, 22
Delivery
DNS
Scenario
- A web browser using a domain name wants to connect to a Web server
- Domain name has no clue on where this Web server is located, nor the path required to get there
- Task: find the domain name’s IP so that user can reach to it’s web server
- so the first step of connecting to the web server is to look up the domain name in the domain name system DNS
- The global domain name system DNS will return an IP address to the browser for that domain name
- from that point on the browser will use the IP address to connect to the server
- it will cache the address for a limited period of time so doesn’t have to look it up all the time
- Web brower → Domain name → DNS(will return IP of the server to web browser) → Web server
Azure DNS
Scenario:
- so when browser uses your domain name, browser will first go to a DNS server to find out the IP of the domain and use it to access your website
- DNS is complicated because not only does it contain the IP address for Web server. It also contains other type of records.
What: Is a managed domain name hosting service inside Azure
- if you already have a domain name, you can delegate that to Azure using your domain registrar
- within Azure you can manage all of the various records that you need to
- Azure DNS allows mapping between domain name and IP address - so we don’t have to memorize IP address and you can directly use domain name instead
Type of DNS zone
- Public: accessible on your public internet
- Private: accessible on your private network
Type of DNS Records
- A records: The IP address associated with the domain.
- This is the one that primarily translate a domain name into its IP address.
- Record set: you can assign same website map to different IPs. ex: Indian and US version of website
- Alias record: map Resource instead of IP. ex: Map domain name with dynamic Azure VM. so we don;t have to update IP regularly
- CNAME record: is used to indicate when one host or a subdomain is an alias for another
- MX record: The server that handles email
TODO:
- Say you have domain name bought from AWS
- In Azure, create DNS zone
- Name: gautampambhar.com
- See the info on your name server(4 entries) and DNS zone with name server records and SOA record
- Take and add the name server(4 entries) to your AWS registrar for your domain
- Add record set to attach your domain to your Azure VM
- Name: www.gautampambhar.com
- Type: alias record
Azure Traffic Manager
What:
- Avoid Region level failure
- If you have everything setup(LB, VMs) setup in one region, it can cause failure if the entire region is down
- ATM: Load balancing happens at global scale - global region
- Operates at DNS level
- Intelligent DNS server
- It’s not the true load balancer
How:
- You have solution running on multi region with one domain name
- Have servers running in multi region for the same website
- So users will connected to server close to them with the fastest response time
- This is done through reverse IP lookup. It knows you are requesting answer from Asia, US. so it will tell your browser to go the solution that performance best for you
Benefit
- Perform failover
- If one region is down then another region will serve your traffic
Azure Front Door
What:
- actual layer 7 load balancing between region
- Azure traffic manager is not load balancing solution at a global level, AFD is
- True load balancer: provides more robust load, balancing service at a global level
- AFD is a scalable and secure entry point for fast delivery of your global applications.
How:
- They provide performance benefits by having the service placed at edge locations closer to users.
- It provides global scale, layer 7 load, balancing similar to the application gateway. allowing you to distribute traffic to different region intelligently based on the domain name and the path information
- Ex: /en traffic goes to certain region, /fr traffic goes to certain region
- Also support caching just like CDN
Benefit
- Provide WAF and DDoS protection
Practical Usage
- Your solution hosted in multipl region. One acting as a active, other is standby
- If one fails, standby becomes active
Comparison
Azure Traffic Manager | Azure Front Door |
Avoid region failure | Avoid region failure |
Requires your solution to run in multiple region at the same time | Requires your solution run in one region. If that region fails, it failover to another region |
Operates at DNS level | Layer 7 LB |
Content Delivery Network
Scenario:
- when you request a website index.html page, you are not just requesting one html page request, but you’re also requesting hundreds of requests. for example each image on that page, CSS or JavaScript has it’s own additional request
- so you are requesting 200 requests with the single index.html page of that server/website
- to improve performance, your web browser might actually cache many of these files. so, second time you’re requesting that page it doesn’t have to go through that server
- server tells the browser how long it should remember the content of that file
- this is cute for one person based scenario, but what if you have thousands of user accessing the same content across the globe
What:
- is a service that can reduce the number of files that your Web server needs to serve to any client and can also improve the performance perceived by your end user
Option
- Akamai
- Verizon
- Microsoft CDN
How
- It has edge location servers all around the globe
- store your static files on dozens of edge servers around the world
- when end-user request to file, the file is served from those servers and not actual server
- The actual server will see drastically fewer request overall
Azure Front Door | Content Delivery Network |
Requires your solution run in one region. If that region fails, it failover to another region | It doesn’t require you to have solution deployed in multi-region |
Layer 7 LB | Its a caching mechanism using edge servers |
Security
Network Security Group - NSG
What:
- The starting point of security. Use advanced features along with NSG
- Controls traffic flowing through a VNet/Subnet, secure the routing pathways
- Create rules that’d define what is allowed/denied
- When you create VNet with a subnet, NSG has 3 default inbound traffic rules
- AllowVnetInBound: traffic between computers running on the same network or connected networks is allowed: Vnet peering and VPN traffic
- AllowAzureLoadBalancerInBound: This is traffic from the load balancer. For example, from health probe is allowed
- DenyAllInBound: all other traffic is denied
- Rules are evaluated in order. From the lowest priority number to the highest. The first rule to match the traffic is the rule that wins
- Create custom rules with high priority to override the default rule effectively. Because the default rule can’t be removed but rather overridden
- Rule example: Port80, 443, 3389, 22
- NSG is stateful, if you create an inbound rule for traffic, the outbound rule gets created automatically.
How: associate with a subnet or NIC
Practical:
- Say you have a standard public IP assigned to VM, and you can’t access to VM through SSH, With NSG you can create a rule for SSH to connect to a VM, now associate this NSG with NIC or Subnet
- Say you have 2 VMs in subnet. Each has their own NIC. you create 1 NSG and attach with subnet that allows SSH to VM. you have 2nd VM’s NIC and you attach 2nd NSG to it with deny inbound traffic.
- Result: you can SSH into 1st VM but can’t in 2nd.
- First NSG rule evaluate at subnet level. Then at NIC level
- The starting point of your security
Application Security Group - ASG
What: Allows you to define certain ranges of IP addresses into certain categories in labels so you can group related resources together
Practical:
- VM comes with NIC
- NIC can associated with NSG
Load Balancer
What: layer 4 LB(transport layer) - so it only understands IP, ports, and networking at the level. It doesn’t understand internet URL
- Route traffic to identical VMs
- Public Proxy: public reach to LB first and not the VM
- VM can have private IP address given from Subnet
- So no hacker can be connected to VM as they don’t have an IP address
How
- LB uses round robin algorithm.
- Send 1 request to 1 server and a second request to the 2nd server
- It has a health probe that frequently checks if the VMs is in good condition. If not, then distribute traffic on available VMs
Application Gateway
What: Layer 7 LB(application layer)
- Configure complex rules
- recognize domain name being used and make routing decision based on that or you can look at the URL path and make decision off of that
- recognize an attempt SQL injection attack and block it in the application gateway using a web application firewall- WAF
WAF
- The application gateway has options to have WAF, Which is a more sophisticated firewall
- this can detect common attacks, such as cross-site scripting in SQL injection, and stop this requests from even making it to the server
AG integrates with Azure monitor
Firewall
What: create a firewall with routing rules.
- PaaS service
- You get fully qualified domain name(FQDN)
Diagram: request comes to the firewall and then redirects to the respective server based on the routing rule you setup
How:
- You’ll need a subnet(must have /26 or lower IP range) specifically for firewall and then deploy firewall into this subnet
- Once firewall created, control traffic using NAT rules, application rules, and network rules in the rull collection inside of firewall or inside the Azurte policy
Implementation
Task: route traffic to VM using firewall
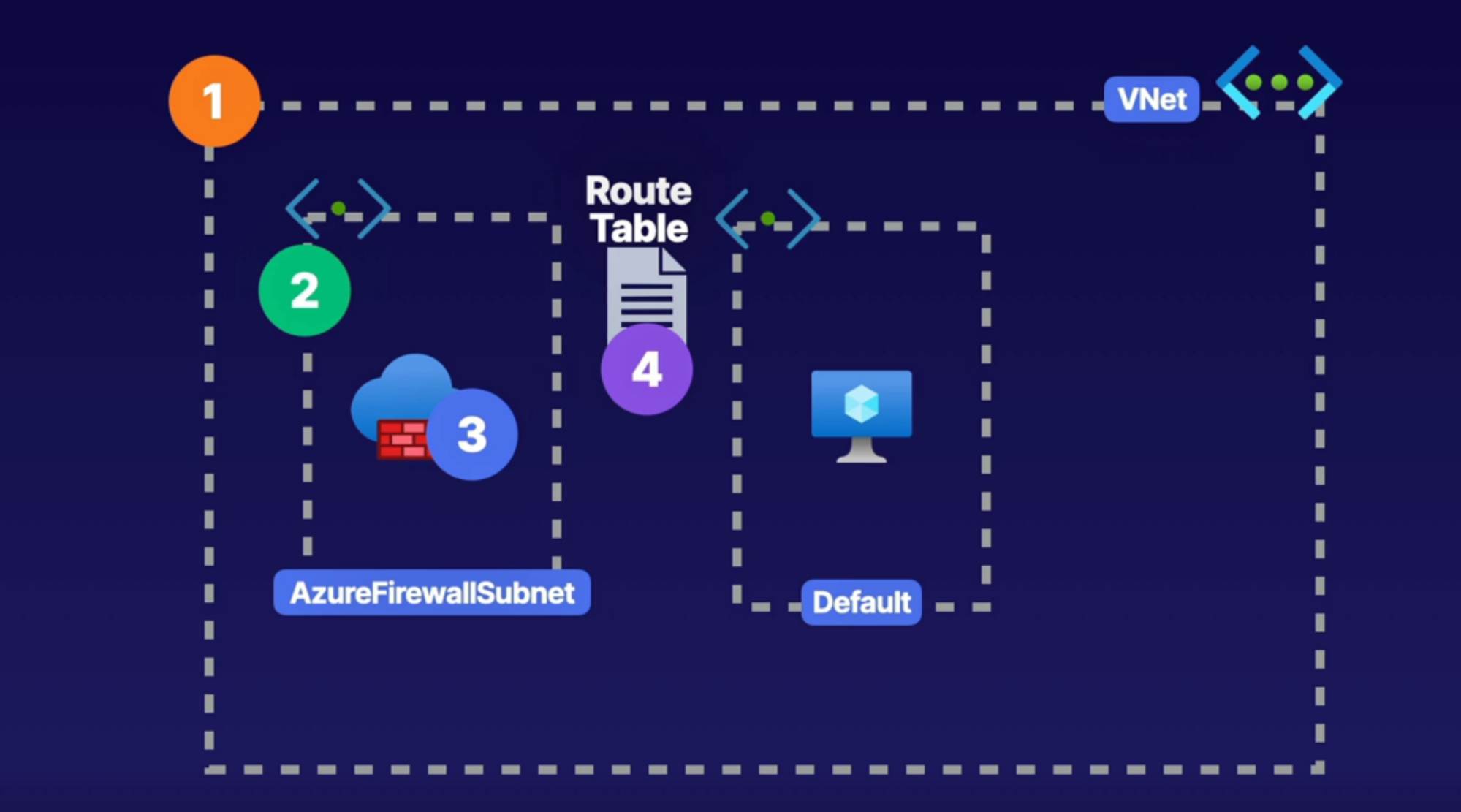
Features
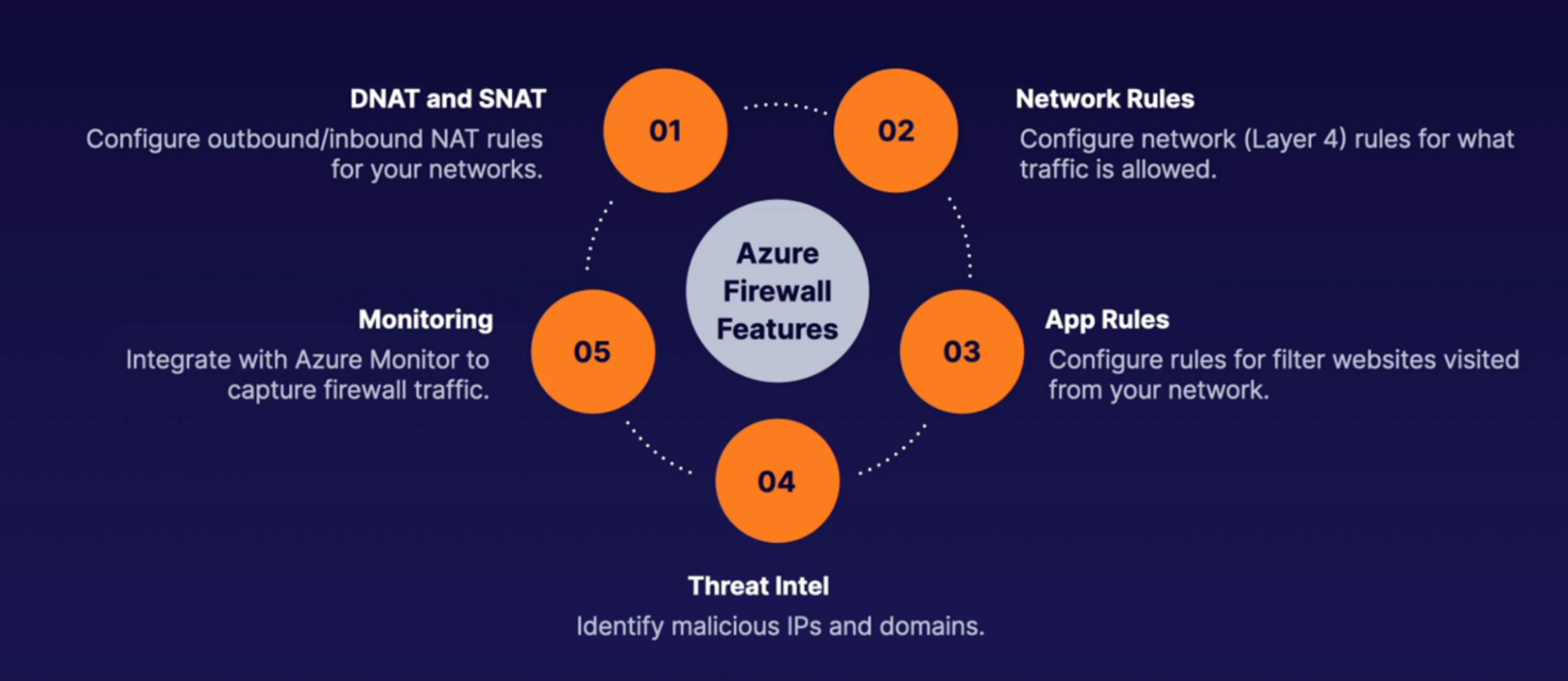
Steps:
- Create VNet with default subnet
- Create firewall subnet
- Create firewall into its subnet: this will create firewall IP
- Create a route table: to define route rules
- Create a route: route all traffic to firewall IP
- Route name and address: 0.0.0.0/0, next hope type, hope add: firewall private IP
- Associate route table with subnet
- In firewall configure firewall rule
- rules: NAT rules
- Configure it route traffic to VM
- Rule ex: allow RDP to firewall, which then translated to VM public IP // access RDP to VM via firewall
Connectivity
Routing
What: path for connectivity(for traffic)
- You define inbound and outbound route for traffic to communicate with VM
- Traffic scenarios
- Resources to Resources within same Vnet
- Resources to Resources with peer VNet
- Traffic with Internet
- Traffic with on-prem Network
- Type of route
- System route: default route built in to VNet, can’t modify
- Custom route: override system route,
- User defined route: firewall
- Broader gateway protocol(BGP): hybrid and Vnet peering
- Flow of overriding: Custom > BGP > System
When:
- You want to direct specific traffic to specific endpoints instead of default through route table
Examples:
- Block outbound internet traffic
- Why: because by-default in NIC’s effective route for system routes allows public connectivity via outbound traffic to internet - so there’s a need to block outbound internet traffic via route table
- With system round you have outbound internet access via a route, but with custom route block ththe outbound traffic
- How: give outbound traffic, next hop to none // cancel out that route
- User define route - firewall example
- If we want to route outbound internet traffic through firewall only
- How: give outbound traffic, next hop to firewall
- BGP route for integrated network - peering, VPN
- In VNet peering or hybrid scenario(on-prem to vnet), set up route between these network, override system route we have in VNet
Example Demo
- Block outbound internet connection
- Create route table
- Inside routes, add route
- Name
- Address prefix: destine traffic: 0.0.0.0/0
- Next hop type: None - kill the traffic
- Inside subnet, associate this route to your subnet
How:
- Rule: Any traffic destines to 220.20.2.0/22 range of IP address(can use any IP address) send them to followings
- VNet gateway
- VNet
- Internet
- Virtual appliances // firewall
- None: kill the traffic
- Associate rule to your NSG/subnet
Example - block internet access
- Create VM: you’ll get VM, Disk, NSG under subnet, NIC, Public IP
- Create route table and block internet access
- Associate subnet to this route table
Service Endpoint
Scenario
- PaaS service like Azure storage, app service as a public endpoint. To access it through your laptop/VM you need to use this public endpoint. And this happens over the public internet. It’s not a private connection
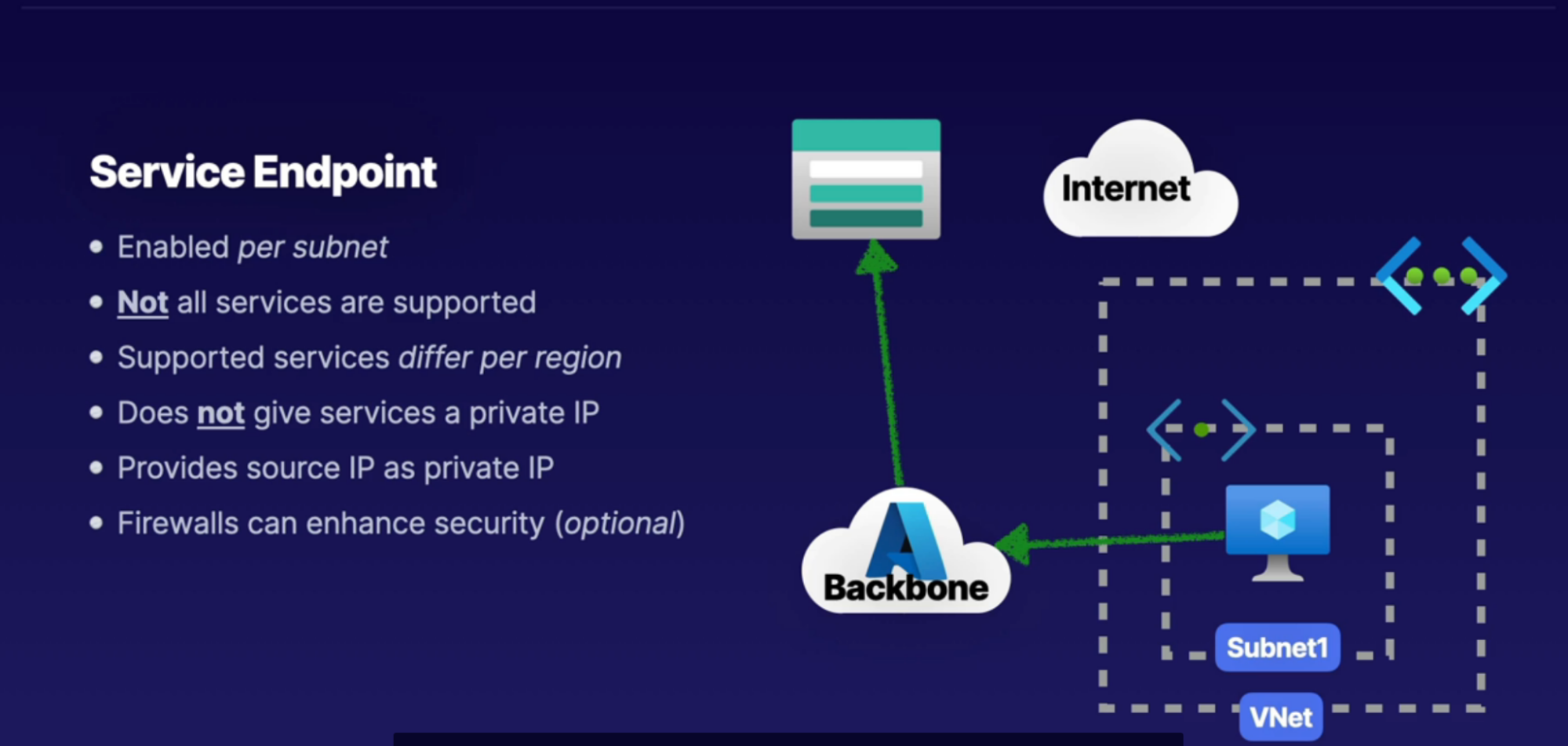
What:
- it enables services(storage) to be accessible over the Microsoft backbone for private connectivity from resources inside of a subnet
- Only resources inside the VNet can access to resource through microsoft backbone to PaaS service
- Although the connection is private, service won’t get private IP aadress. It provides source IP as private IP
- Not all service supported to use service endpoint with
- Enabled per subnet
When
- When you want to access service privately. Ex: Storage account file share
How:
- Inside your subnet, create service endpoint(can also create service endpoint policy - for specific storage account) specifically for this subnet - Microsoft.storage
- See the service endpoint blade under subnet setting.
- So any connected devices connected to subnet has a route that allows private connectivity from subnet to storage through microsoft backbone
Example:
- Secure storage account access from internet traffic
Private Endpoint
What: using Azure private link, you can connect your services as connected resources in your network with a private IP known as a private and point
- provide private endpoint via private IP for that service(azure service, customer service) that we are connecting as a resource inside of our virtual network
- it’s a direct mapping with the service you’re connecting to. Ex: you can connect to Azure blob, file directly inside the Storage account
How
- NIC inside your VNet, act as the private IP that is going to provide the connection for private connectivity over an IP to that service so that we can access that service inside of a virtual network via that private IP
Steps
Task: Create private endpoint for Azure file inside VNet
- In Azure, create private link
- Resource type: microsoft.storage
- Resource: your storage account
- Target sub resource: azure file on your storage account
Callouts
- if you have a NSG enabled for the subnet above it, it will be disabled for private and points on this subnet only. other resources on the subnet will still have NSG enforcement
VNet peering
Scenario:
- Say you have multiple VNets and resources inside these VNets need to be able to communicate.
- By-default these VNets are isolated and thus can’t communicate
What: Connection bw VNet to VNent in Azure
- Non-reciprocal: connection must be established in both direction
- Peering can be same region or cross-region(global)
- Non-transitive: if you have three Vnets, where V2 connected to V1 and V3, doesn’t mean that V1 can talk to V3
Steps:
- Under Vnet1, settings → peering
- Add peering
- Link name: VNet1toVNet2
- Peering link name: VNet2toVnet1
- VNet: VNet2
- Repeat step 1,2 in the VNe3 (conneting to VNet2)
Design: Hub and Spoke Topology
How: This has 1 VNet in the middle and all of the satellite VNet connect to it
- if you want the spokes to be able to talk to each other, you can set up a route that allows traffic to flow from one spoke across the hub into another Spock
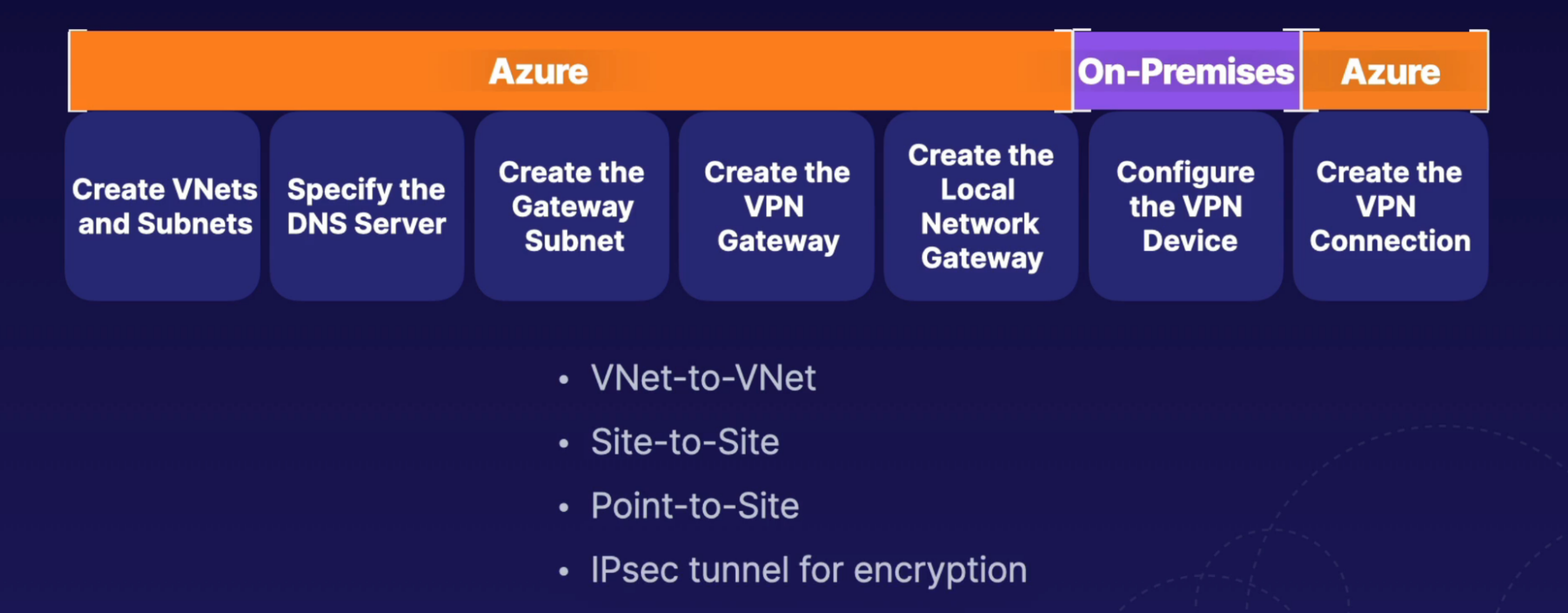
VPN & VPN Gateway
What: Connection bw Azure VNet to On-prem network over public internet
- Same as peering connection using Vnet peering
- Transitive: say you have VPN connection between On-Prem and Azure VNet1, now VNet1 is peered with VNet2. Connection from On-prem to VNet2 is allowed
Practical Example: connect your home device/entire office network to Azure network so that you can have access to Azure resources
How in Practical:
- It creates the encrypted channel between single machine/network and another network
- Access resources protected behind the firewall
- You have to install special software on your home computer or use reconfigured work laptop to connect to your office files from home. This happens over a VPN.
How:
- Create Gateway subnet required in VNet // small subnet that only contains the gateway device
- Add VNet Gateway device(in Azure, in Gateway Subnet) for VPN gateway // VNet gateway establish VPN gateway
- VNet gateway is the device that connects to the network on the Azure side and also performs the encryption and decryption of the traffic between it and the device connected to it on the other side
- Public IP per VNet gateway // because it’s internet connection
- IPSec tunnel for encryption
Types
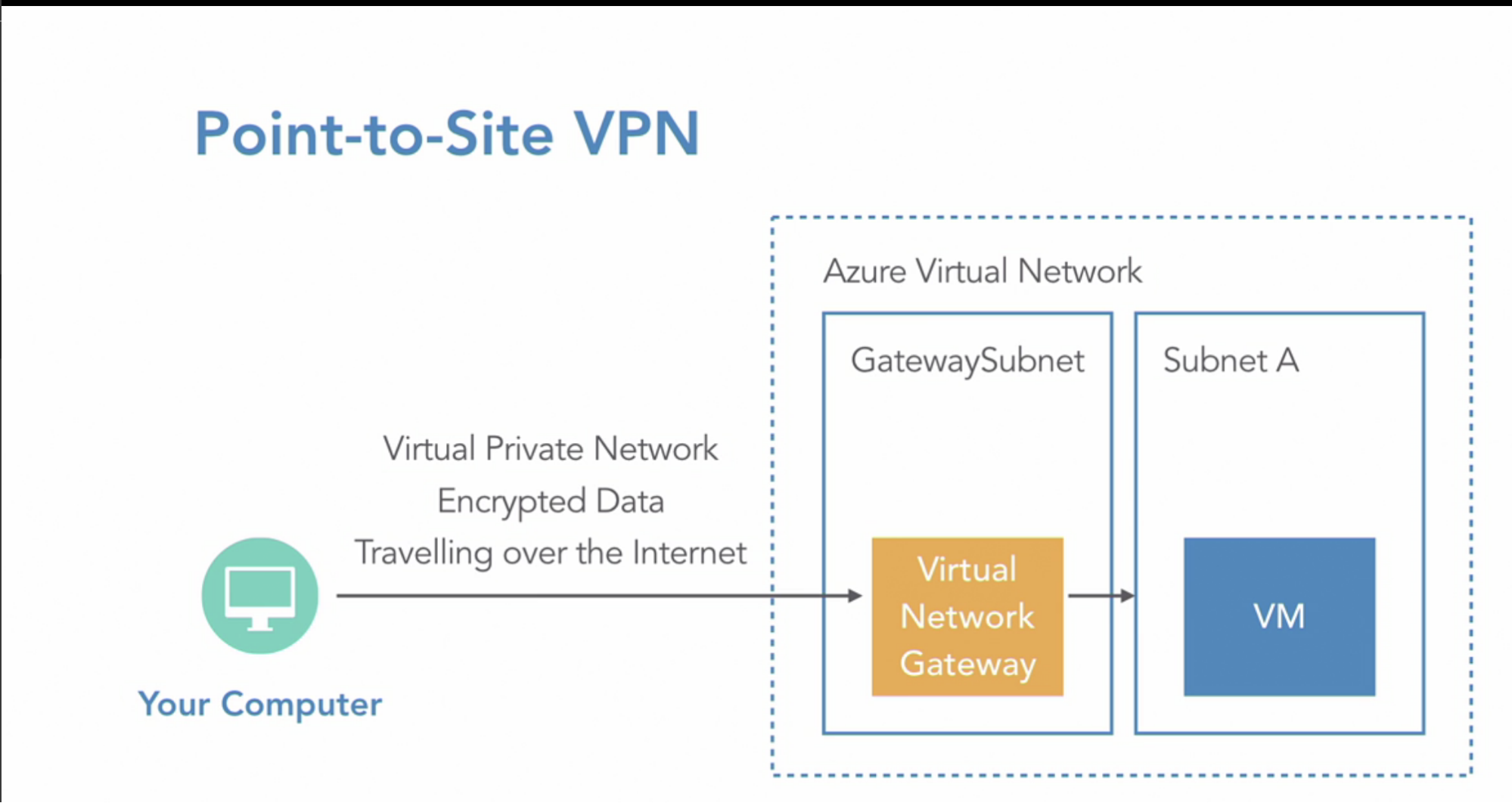
- Point-to-site VPN(computer to Azure network)
- add a single computer/server/your office device into an azure network, so using a VPN, your desktop can act like it’s on Azure private network and have access to resources normally protected behind the firewall
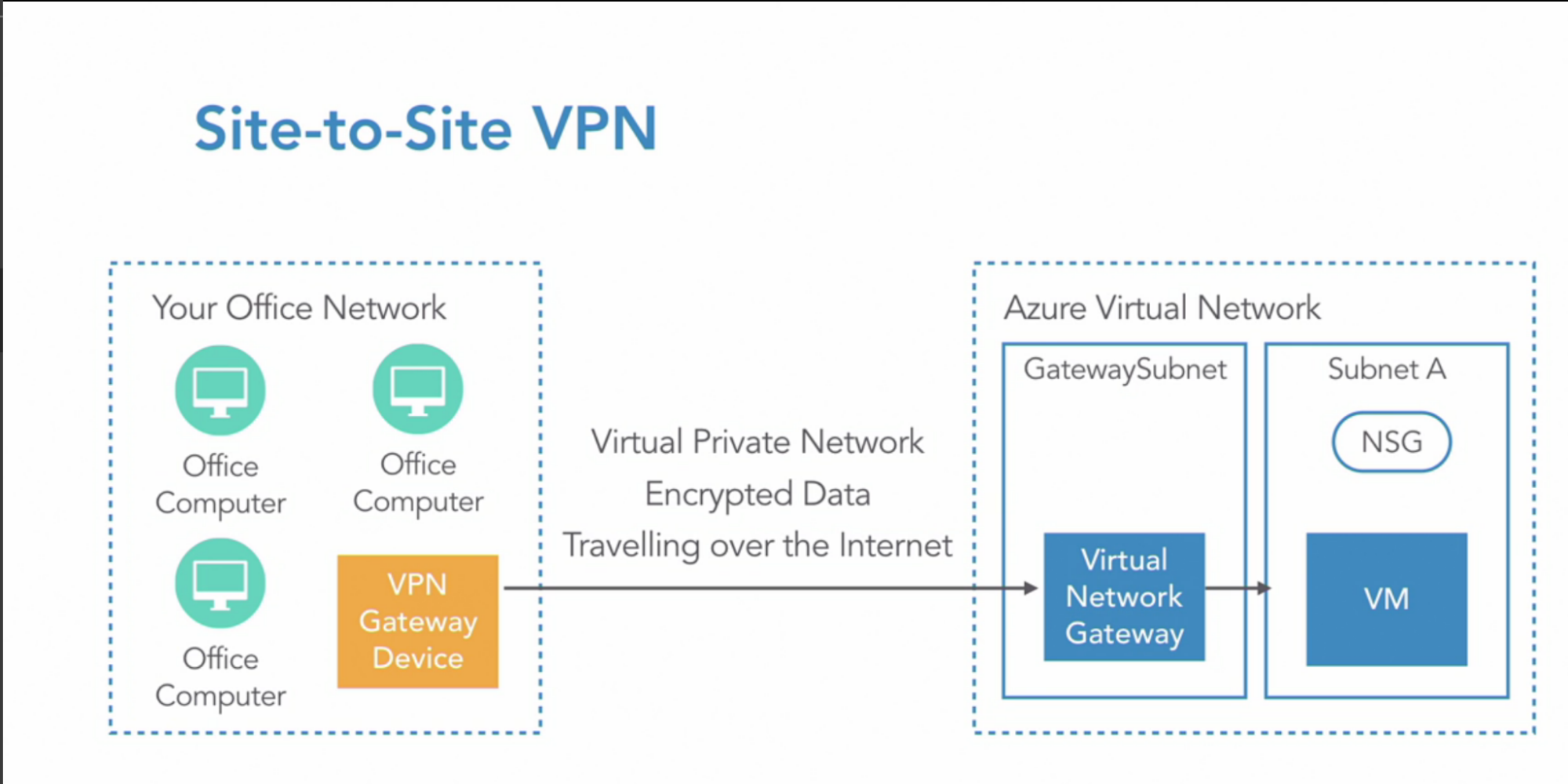
- Site-to-Site VPN(IT office network to Azure network)
- Entire office network connected to Azure network
- This requires a physical VPN gateway device - gateway to be installed on your side - to create an encrypted private channel into the Azure network
- Microsoft Azure only support certain type of gateways, so please check the device you have is on the list of supported ones
2 types of Gateways
- Static routing - policy based
- old style of VPN routing: fixed routing table
- you have a router table that has hard-to-find IP addresses that tell traffic where to go.
- so for a particular range of IP addresses, send traffic over this VPN connection to the other side
- Dynamic routing - route based
- BGP: It allows 2 gateway devices to exchange information with each other
- each device tells the other what network ranges it supports. So device A tells device B that it wants traffic from this range so that device B Will send it that traffic.
- no table contains a static list of addresses.
VPN Availability
- Redundant connection: if the connection between your office network, and Azure network fails, this will act as a single point of failure. So networks can’t talk to each other
- Azure gives two connections between the two devices. So if one connection fails, you could have it fall over to the other. few seconds of downtime at the time of failover happens
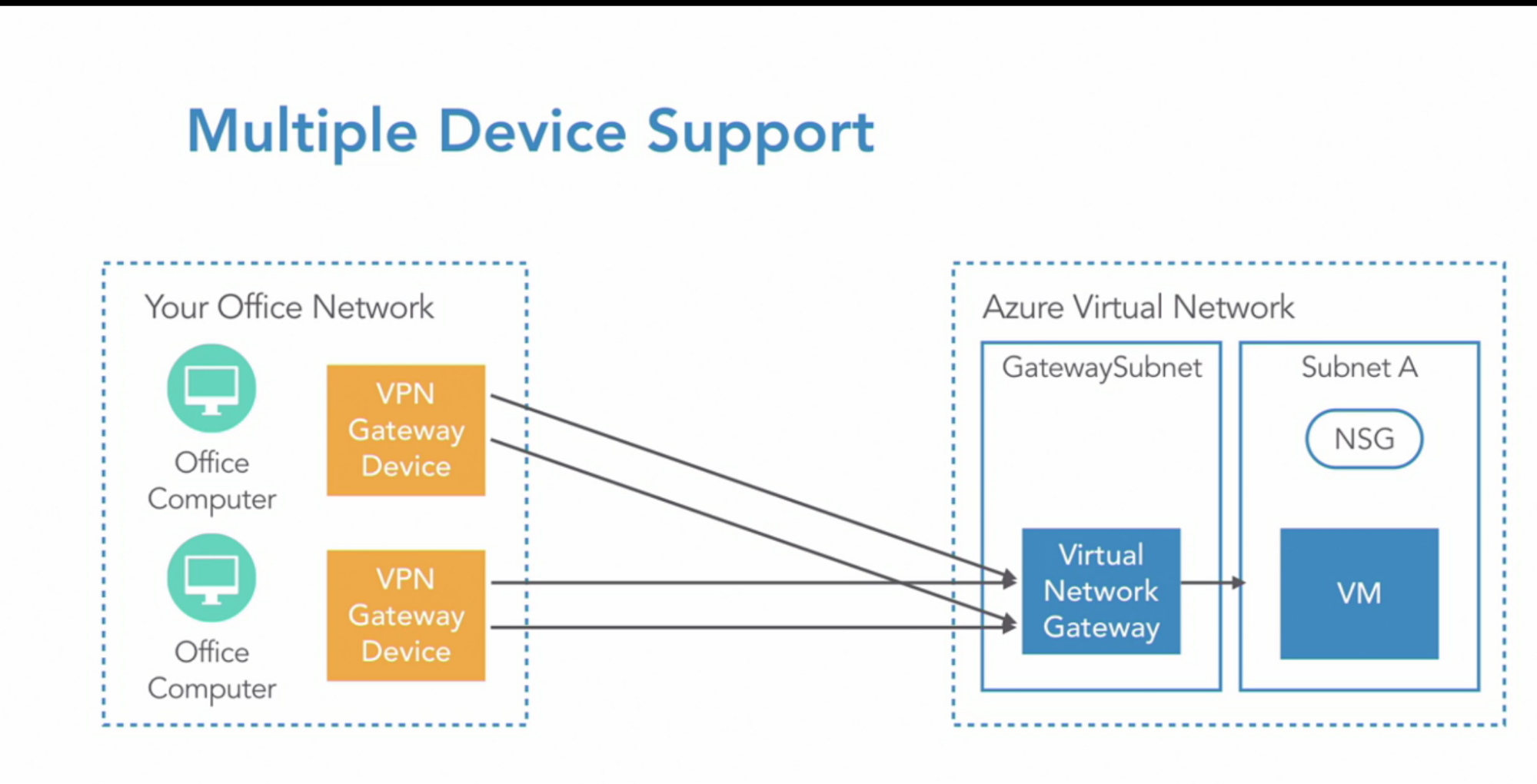
- Multiple Device support: if the gateway device itself failed in your office network
- you can have multiple VPN gateway device at your office network connecting to the same VNet gateway in Azure
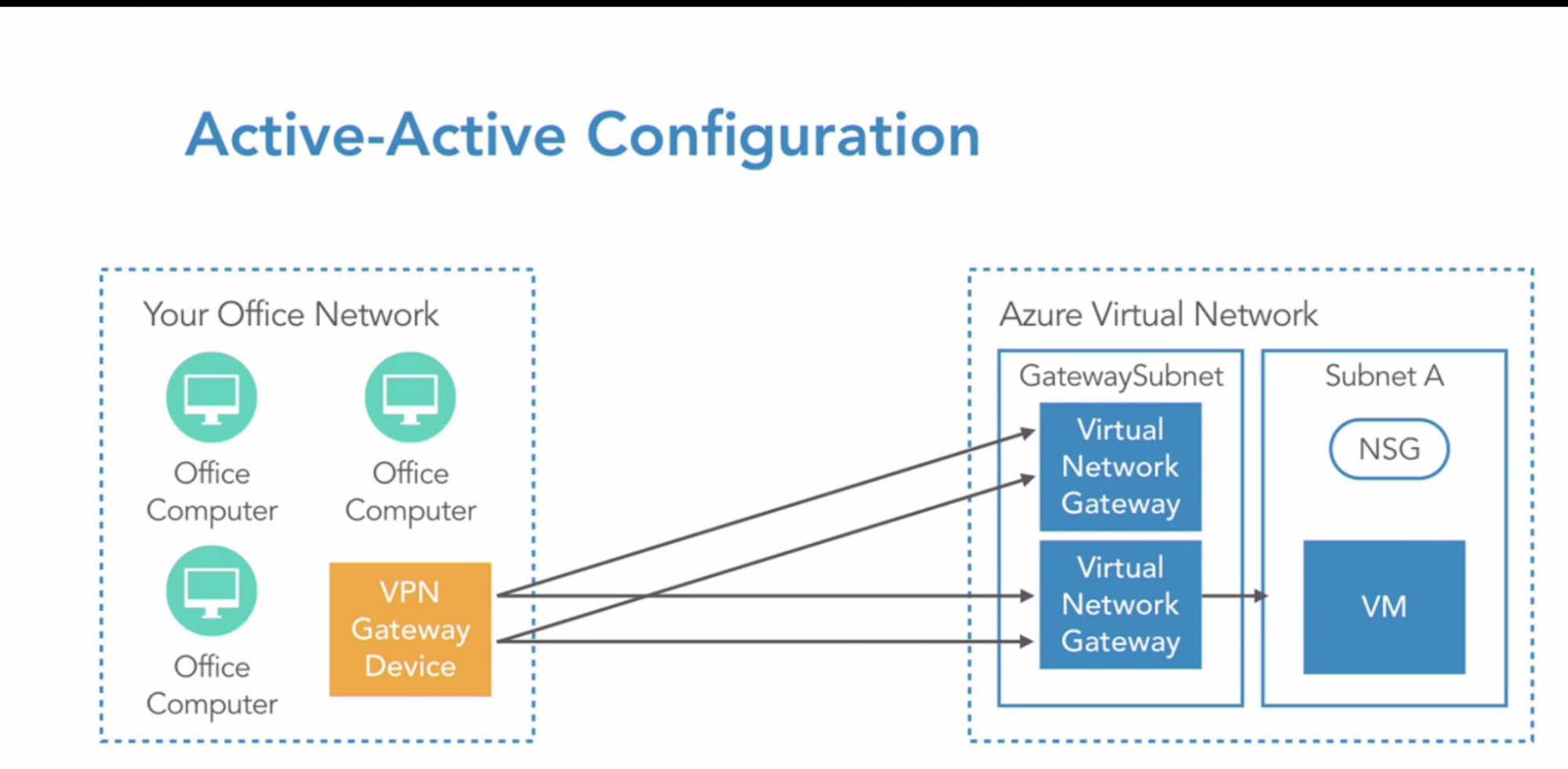
- Active-Active configuration:
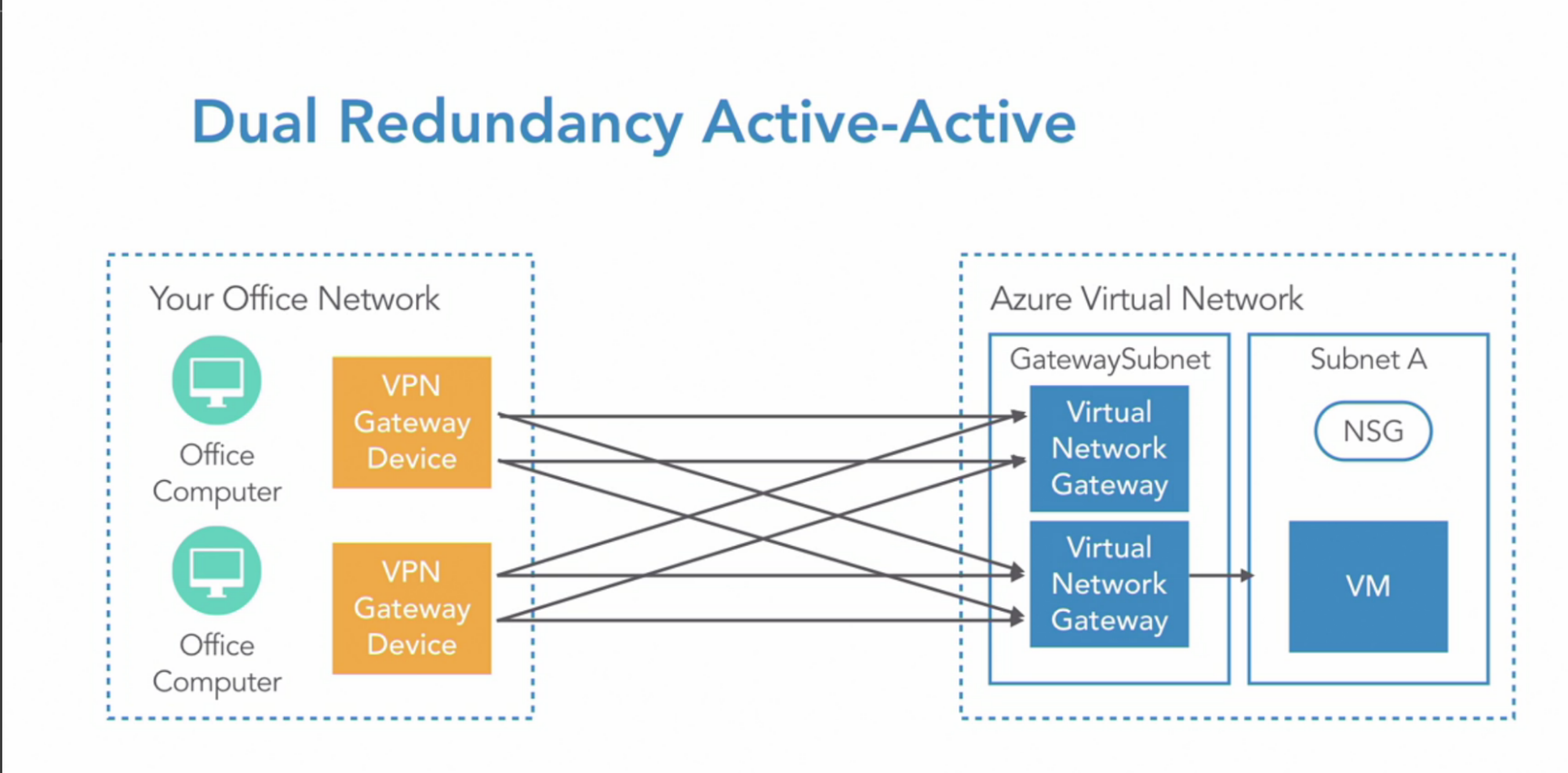
- Dual redundancy Active-Active
Architecture
- Setup VPN gateway
- Create a gateway subnet in Azure
- Create HQ local network gateway in Azure
- Create with the configuration details of the connection we have with on-prem network
- Setup VNet gateway in gateway subnet
- This will allows to communicate
- Create a connection from VNet gateway to HQ local network gateway
- Create gateway subnet in on-prem
- Create azure side local network gateway in on-prem
- HQ side VNet gateway
- Create connection from VNet gateway to Azure local network gateway
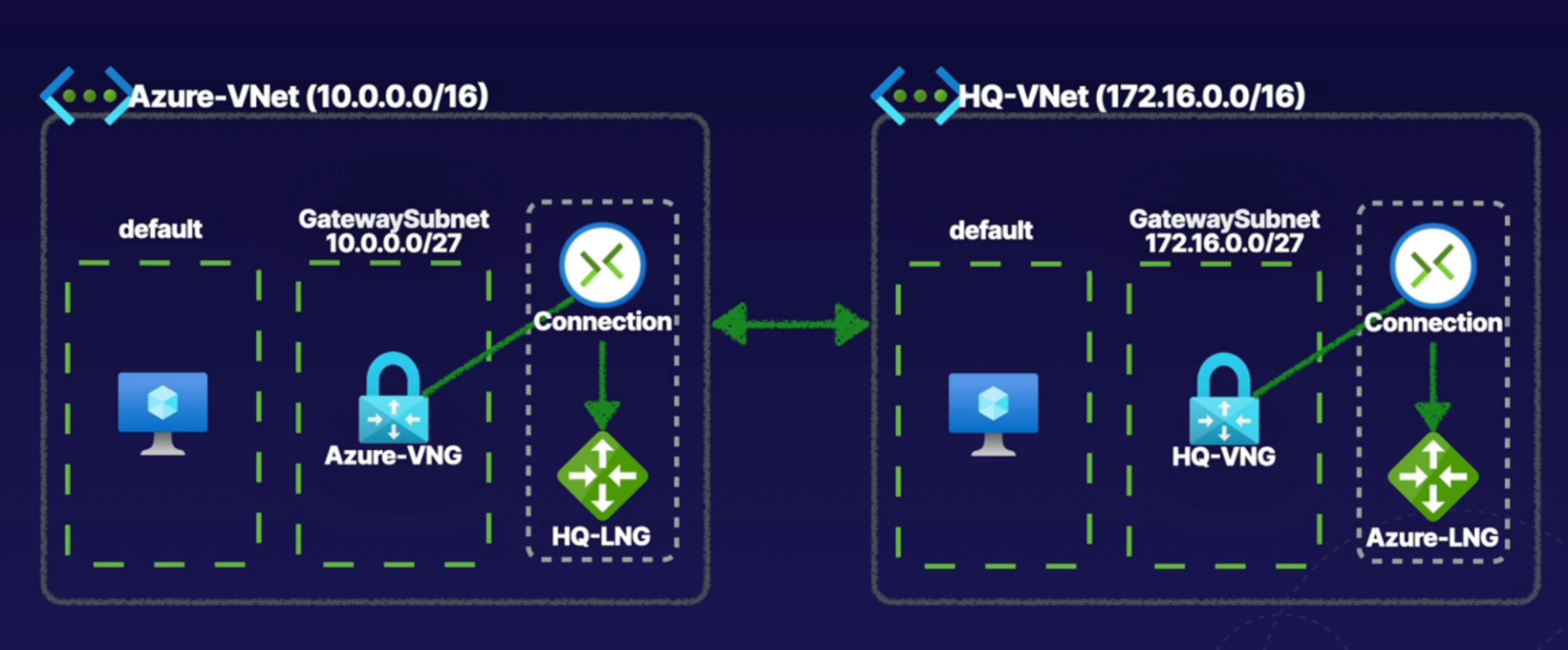
Steps
Both the steps must be performed for both network
- Create VNet gateway on Azure
- Gteway Type: VPN
- VPN Type: route-based // dynamic incase your VM increases
- Create gateway subnet
- 10.0.1.0/27
- Create public IP address
- Create local network gateway
- Need public IP of VNet gateway created in the above step
- Create local network gateway
- IP address: provide VNG IP
- Address space: Azure VNet IP CIDR
- Create connection bw local network gateway and VNet gateway
- In the VNet gateway, create connection
- setting —> Connection
- Add connection
- type: site to site
- Shared key: key has to be the same on both side
Test: ping VM from VNet 1 to VNet 2 as a part of VPN
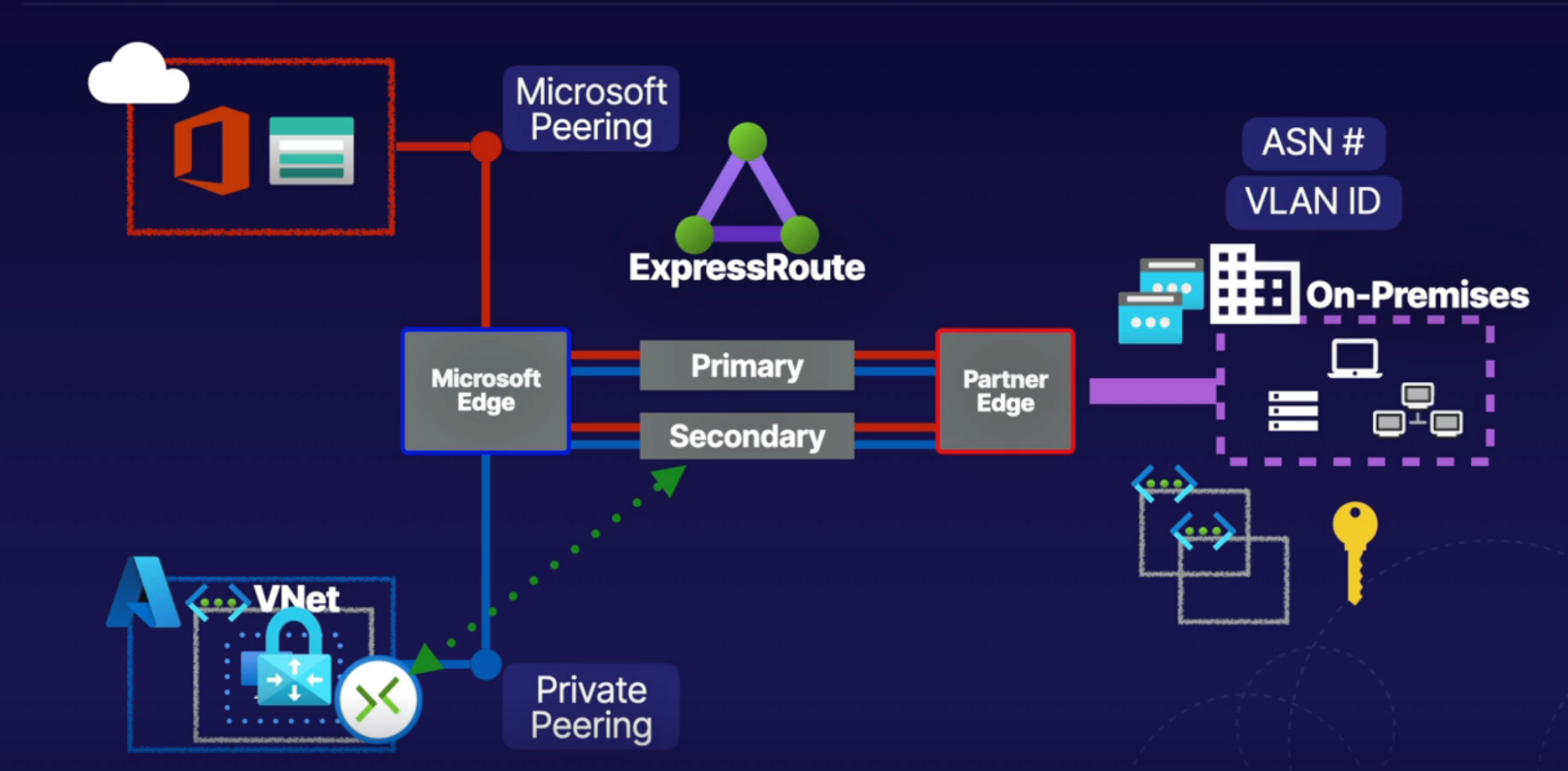
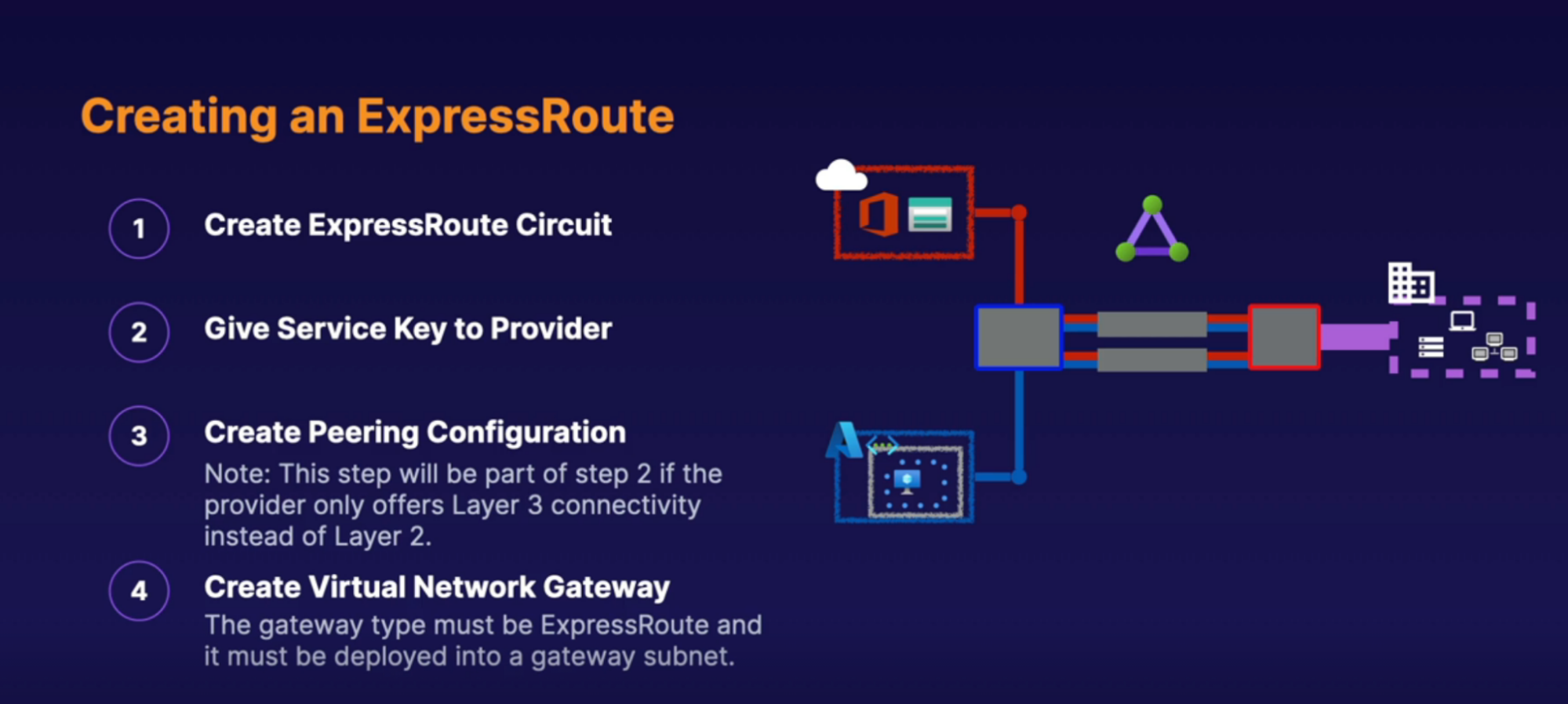
Express Route
What: make direct physical connectoon into Azure resources
- Private physical(over the wire) connection to Azure Network
Architecture
Implementation
Virtual WAN
What: allows single operational interface to be able to manage hub and spoke style network
- We can use Virtual WAN hubs, to create hub and spoke style networks, where we do things like VPN connection(S2S, P2S) both on on-prem and remote users, can connect express route, can make connection to our VNets inside this Hubs
- With this HUBs we have a single operational interface to manage all of these connections to create hub and spoke network
- Connect S2S,P2S, ExpressRoute, VNet to Vnet connection
- Ability to manage firewall and routes to manage entire network on single operational interface
- WANs Per region
How
- You are creating hubs inside WAN in each region
Types
- Basic
- Transitive connection not allowed
- S2S VPN connection only
- Standard
- Transitive connection allowed
- S2S,P2S, ExpressRoute, VNet to Vnet connection
Task: Create Virtual WAN, Virtual Hub to configure S2S,P2S, ExpressRoute, VNet to Vnet connection for that Virtual WAN through single operational interface
- Create virtual WAN // single operational interface to manage fully mash network(manage hubs that manages VNets inside region, for this region you can configure S2S,P2S, ExpressRoute)
- Type: standard
- Create hub // for specific region
- Basics
- Name
- Private address
- S2S
- P2S
- ExpressRoute
- Create hub
Create
VNet Strategy
VNet/Subnet Strategy
- Good naming policy
- Ex: ProjectName-Env-Component-Resource = tiffintouch-dev-root-vnet
- Tag your resources
- Useful for internal reports and billing
- In what region you’re going to deploy VNet
- Resources should be place inside Vnet region
- Design VNet and Subnet
- Don’t overlap VNet/subnet address with any other VNet/subnet in the same/diffrent subscription
- Separate layer of your application within subnet
- Web server can live on their own subnet
- Mid tier and Application tier has their won subnet
- Database tier has their own
- Leave room for IP address for the future
- Ex: VPN, virtual node, express route need their own subnet
- Which device need public address
- Ex: if the internet traffic to your azure resources(VMs) would only go for administrative purposes, Use Bastion or VPN to protect access
- Does this network need to directly communicate with any other network using peering
- They can’t communicate when you have overlapping IP addresses - this is non-issue if the both the VNet is under the same subscription - because azure deosn’t allow creating 2 VNet with overlapping IP address
- If the networks with same IP address in separate subscription can’t talk to each other
Security Strategy
- Create small set of NSGs
- Reuse the same NSG instead of creating new one for every network
- Use application security group - ASG as simplifying your NSG
- Limit the people who can create VNet resources - principal of least previlege
- Use subnet to separate your application into logical security zones
- Subnet for web server and sql kept separately along with their own NSGs
- Use Azure AD conditional access to add additional layer of security
- Just in time access
- So that ports are closed, except when someone is actively using for legit purpose
- Disable RDP and SSH access to resources, except for specific purposes
- Use temporary permission tool instead of admin privilege, when people need elevated privileges to perform authorized task
- Use Azure AD conditional access and PIM(privileg idenityt mananegment) so that those permission are removed after a short time
- Use tool for the job
- Load balancer
- application gateway for WAF
- Azure firewall
- Third party azure appliances
- Reduce the size of the attack surface
- Don’t leave ports open
- Disable program and services from running that you don’t need
- remove executable code from your web service like disabled WordPress plug-ins
- use virtual network, service endpoints to cut off public access to App service, storage and SQL databases
- use network routing to ensure traffic can only travel to, and from your corporate network, or a VPN and block direct access to the Internet
- consider DDoS protection if you are a potential target
- if your user can’t access your application because it’s too busy, that might not be a direct security threat but it’s a form of an attack - basic DDoS protection is provided free by Azure to protect against Denial of service attack
Performance Strategy
- Choose the VM with the right configuration you need
- Depending on the instance type you choose, more NIC cards generally correlates with an increase in the upper limits of performance speed.
CALLOUTS
- VNet with private IP Address
- Span within region and RG
- Subnet with segregation of VNet
- Span within region and RG
- VM NIC - Network Interface card
- VM is connected to NIC —> NIC is then connected to subnet
- Place/connect NIC in the subnet —> subnet pass IP to NIC —> which is then attached to VM
- flow: Subnet —> NIC —> VM
- VM can have multiple NIC. These NIC’s can connect to different subnet // both subnet can be part of the same VNet
- IP configuration (for NIC)
- Private IP: gets from subnet private IP. Can assign static IP if you want, by default it’s dynamic.
- why: Used to communicate bw resources privately over VNet
- Public IP: you don’t need Public IP for NIC. But you can get/create one and attach to
- Why: used to communicate bw internet traffic to your Azure resources(VM)
- ow: modify IP config in NIC for VM so that it has public IP
- 2 types are public IP.
- Basic: insecure and accessible by default, and allow traffic. Require NSG to deny traffic
- Standard: secure by default and not accessible by default. Require NSG to allow traffic
- what: Provides public connectivity for resources. Can connect to resource via internet
- Example flow: create standard public IP —> Create NIC —> configure Public IP in NIC —> Create VM with NIC —> SSH to VM with public IP // can’t make connection
Architecting VPC in AWS
- Decide how many IP address do you want
- Choose your CIDR
- Choose how many subnets do you want and allocate your network IP address into Subnet
- You may want your Database, Application, Web servers into different subnets and want the to have different access level
- your database subnet you can completely prevent external access to your database subnet means no one from outside your VPC can connect your database except for the systems in your VPC
- However, for your web servers, you have to allow external access
Technical Key Points
- You have your network, breaking down into subnets, and you place your resources into subnet
- Router allows all the traffic routing between all of your different subnets
Important things
- Connect your home network to VPC with Private IP (No internet involved)
- How?: via a virtual private gateway
- Connect your VPC networks with one another with VPC Peering (No internet involved)
